
With the help of ECC (Elliptic Curve Cryptography), we can utilize the powerful capabilities of public key encryption while achieving the speed and security of symmetric encryption. Therefore, we gradually turn to practical scenarios, focusing on the following categories:
(1). Public Key Key Exchange Protocols: ECDH (P256), ECDH (P384), ECDH (P521), X25519 and X448.
(2). Public Key Encryption: RSA and ECIES.
(3). Hash-based Key Derivation (HKDF): SHA256, SHA384 and SHA512.
(4). Symmetric Encryption: 128-bit AES GCM and 256-bit AES GCM.
All of the encryption algorithms mentioned above are compatible with most systems. Bob and Alice can choose an elliptic curve to define their key pairs, and then use a given hash algorithm to compute the encryption key, which is usually implemented through HKDF (HMAC Key Derivation Function). In practical scenarios, we typically use symmetric encryption as it is much faster than public key encryption.
In summary, there is a general trend towards using AEAD (Authenticated Encryption with Associated Data), where one typical mode is GCM.
Next, let’s use the hybrid encryption method:
Now, suppose Bob wants to send an encrypted message to Alice. First, Alice generates a key pair (public key and private key), and then she sends her public key to Bob. Bob uses the public key to compute the symmetric key used for encryption (S).
Then, Bob encrypts the message using K and the AES GCM encryption algorithm, resulting in the corresponding ciphertext (C) and the value of R. From R, Alice can derive S from her private key, and with this key, she can decrypt the ciphertext to retrieve the plaintext message.
To achieve this with RSA, Alice creates a random symmetric key (KA), encrypts it with Bob’s public key, and then uses KA to encrypt a file. She then sends the encrypted key (E_pk(KA)) and the encrypted file to Bob, who decrypts the encrypted key to obtain KA, allowing him to decrypt the file. The following (Figure 1) is a schematic diagram of the hybrid encryption model.
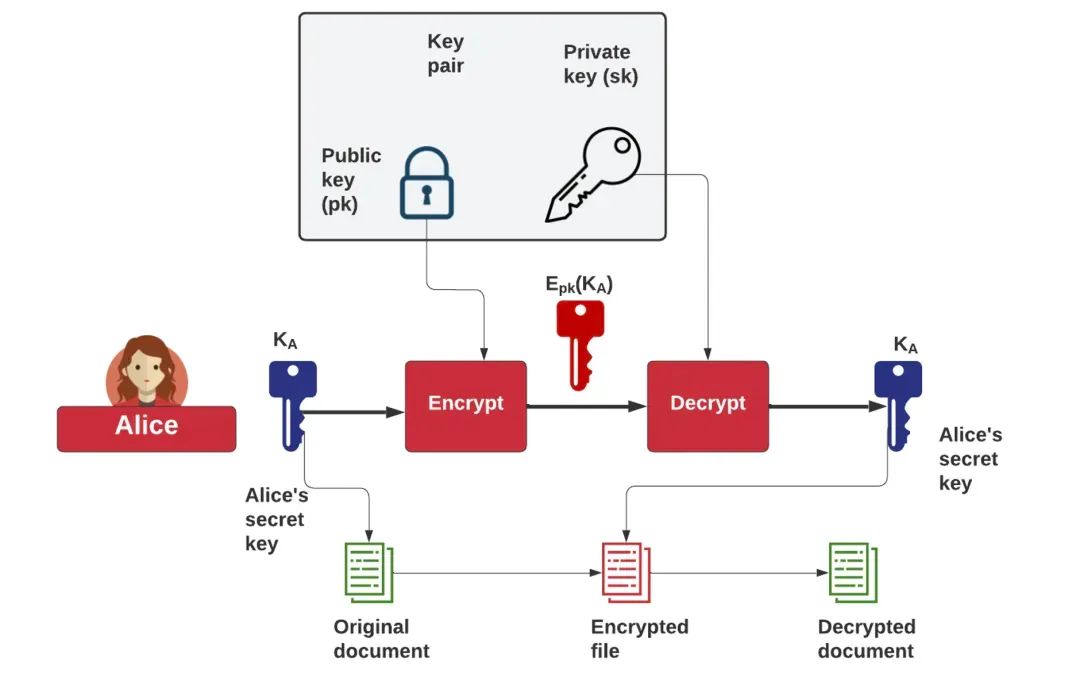
Figure 1 Hybrid Encryption System
However, the elliptic curve method cannot be directly used to encrypt data, so let’s see how these methods achieve this.
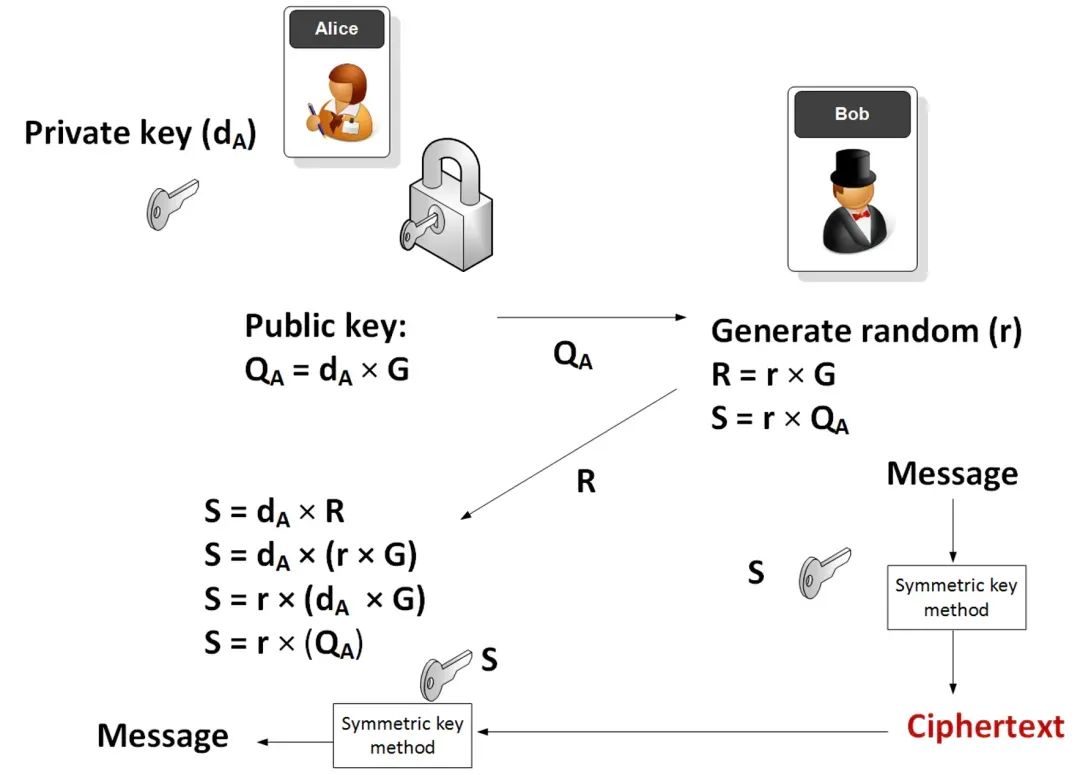
In the context of elliptic curves, Alice generates a random private key (dA), then takes a point on the elliptic curve (G) and determines her public key (QA): QA=dA×G
Therefore, G and QA are both points on the elliptic curve. Alice then sends QA to Bob, who subsequently generates: R = r × G and S = r × QA, where r is a random number (nonce) generated by Bob, and then uses the symmetric key (S) to encrypt the message.
Then Alice receives the encrypted message along with R, and she can determine the same encryption key as follows: S = dA × R, which is because:
S = dA ×( r × G )
S = r × ( dA × G )
S = r × QA
This is the same key generated by Bob. Once Alice has S, she has the symmetric key for the encrypted file and can decrypt it. The following (Figure 2) is a schematic diagram of this method.
While RSA remains the most common form of public key encryption, ECIES provides rich functionalities of public key encryption and the speed of symmetric encryption. Meanwhile, RSA can be used alongside symmetric encryption, and we typically use the public key to encrypt the symmetric key, allowing RSA to encrypt our symmetric key.
Source:
https://medium.com/asecuritysite-when-bob-met-alice/elliptic-curve-integrated-encryption-scheme-ecies-encrypting-using-elliptic-curves-dc8d0b87eaa
Author: Prof Bill Buchanan OBE
Translated by: Yang Yunbo
This sharing is for learning reference only. If there are any issues, please contact us for resolution.
Previous Recommendations