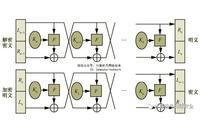
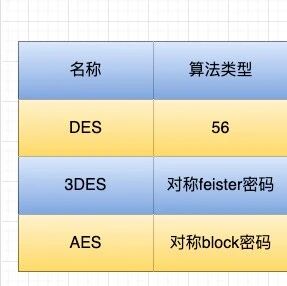
Data Encryption Using AES Algorithm
1. Data Encryption Using AES AlgorithmEnsuring data security is a matter of utmost importance for every company. When performing data tracking on websites, the unique identifier for customers (Customer ID) often needs to be stored in our database. The purpose of this is to correlate and analyze customer behavior data on the website with their … Read more