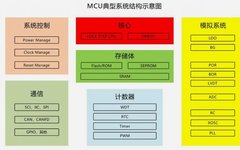
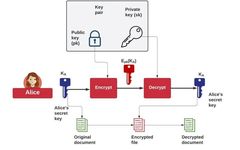
Application of C Language Encryption Algorithms: A Cryptographic Tool for Safeguarding Network Security
In the field of network security, encryption technology is a key means of protecting the confidentiality, integrity, and availability of data. The C language, as an efficient and flexible programming language, can implement various encryption algorithms, providing strong support for network security. 1. Symmetric Encryption Algorithms 1. AES (Advanced Encryption Standard) AES is a symmetric … Read more




![[MalDev-17] Custom Encryption Algorithms and Elliptic Curves](https://boardor.com/wp-content/uploads/2025/05/5b9d64e6-0912-49ef-bf95-2ba5ec6d3a3c.jpg)