
Source: blog.csdn.net/qq_36470686/
article/details/85206648
1. Overview
In the field of security, using key encryption algorithms to encrypt the communication process is a common security measure. This method can ensure three goals of secure data communication:
1. Data confidentiality, preventing user data from being stolen or leaked. 2. Ensuring data integrity, preventing the user’s transmitted data from being tampered with. 3. Identity verification of both parties in communication, ensuring data comes from legitimate users.
The common types of key encryption algorithms can generally be divided into three categories: symmetric encryption, asymmetric encryption, and one-way encryption. Let’s understand the relevant algorithm principles and their common algorithms.
2. Symmetric Encryption
Initially, symmetric key methods were used in encrypted transmission, where the same key is used for both encryption and decryption.
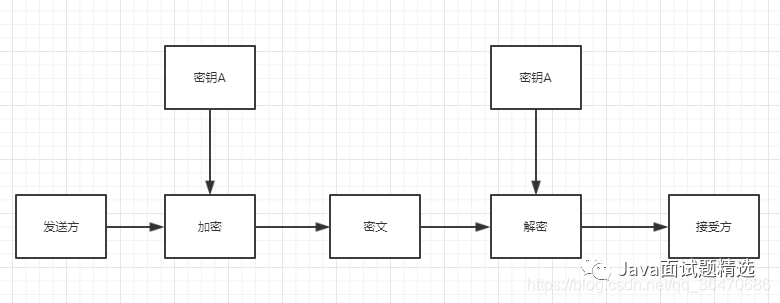
The symmetric encryption process is as follows:
1. The symmetric encryption algorithm uses a single key for encryption. During communication, the data sender divides the original data into fixed-size blocks, encrypts them one by one using the key and encryption algorithm, and sends them to the receiver.
2. The receiver receives the encrypted message and uses the same key with the decryption algorithm to decrypt and combine it to obtain the original data.
Illustration:
Advantages
High efficiency, simple algorithm, low system overhead, suitable for encrypting large amounts of data.
Disadvantages
Poor security
The encryption and decryption algorithms are public, so the secure transmission of the key becomes crucial. Typically, the key is transmitted physically between both parties or through a third-party platform. If this process leads to key leakage, malicious individuals can intercept and decrypt the encrypted transmission content using the corresponding algorithm.
Poor scalability
Every pair of communicating users needs to negotiate a key, so a group of n users requires n*(n-1)/2 different keys, making management inconvenient; if the same key is used, the probability of key leakage greatly increases, rendering encryption meaningless.
Common Symmetric Encryption Algorithms
-
DES: A block cipher algorithm that encrypts data in 64-bit blocks, using the same algorithm for encryption and decryption. -
3DES: Triple Data Encryption Standard, applying the DES encryption algorithm three times to each data block. -
AES: Advanced Encryption Standard, a block encryption standard adopted by the U.S. federal government to replace the original DES, now widely used. -
Blowfish: A symmetric key block cipher algorithm with a 64-bit block size and variable key length, used to encrypt 64-bit length strings.
3. Asymmetric Encryption
The asymmetric encryption algorithm uses two different keys, a public key and a private key, for encryption and decryption. The public and private keys exist as a pair; the public key is derived from the private key and made public. If data is encrypted with the public key, only the corresponding private key (which must remain secret) can decrypt it, and vice versa. For N users to communicate, 2N keys are needed.
Uses
Asymmetric key encryption is suitable for encrypting sensitive information such as keys or identity information, thereby meeting user security needs.
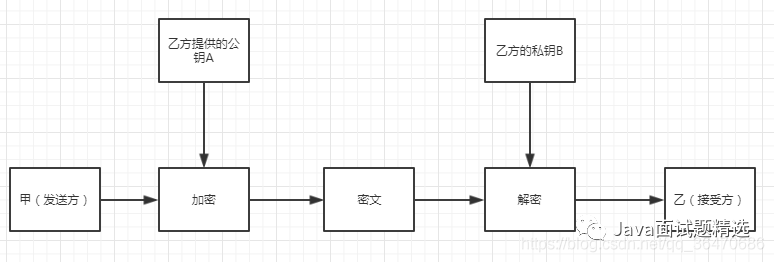
Asymmetric Encryption Process
1. A encrypts the plaintext using B’s public key along with the corresponding asymmetric algorithm and sends the ciphertext to B. 2. B receives the ciphertext, uses their private key and the asymmetric algorithm to decrypt it to obtain the original plaintext.
Illustration:
Advantages
Higher security compared to symmetric key encryption/decryption methods, as different keys are used for encryption and decryption, and one key cannot be derived from the other. Moreover, information encrypted with the public key can only be decrypted with the corresponding private key.
Disadvantages
1. The complexity of asymmetric key encryption algorithms leads to longer times for encrypting large amounts of data, making it suitable only for small amounts of data. Additionally, the added overhead during the encryption process can result in longer ciphertext, which may cause fragmentation and hinder network transmission.
2. It is challenging to verify the legitimacy of the public key’s source and the integrity of the data. We will discuss how to confirm this next.
Common algorithms include:
-
RSA: The RSA algorithm is based on a very simple number theory fact: multiplying two large prime numbers is easy, but factoring their product is extremely difficult. Thus, the product can be made public as an encryption key, usable for both encryption and signing. -
DSA: Digital Signature Algorithm, used only for signing, not for encryption/decryption. -
DSS: Digital Signature Standard, can be used for signing and also for encryption/decryption. -
ELGamal: Utilizes the principle of discrete logarithms for data encryption or signing, with the slowest speed.
4. One-Way Encryption
One-way encryption algorithms can only be used for data encryption and cannot be decrypted. Their characteristics include fixed-length output and avalanche effect (a small change in the message bits causes many bits in the information summary to change).
More: Yearly content, summary of 200 Java interview questions.
Uses
One-way encryption algorithms are commonly used for extracting data fingerprints, verifying data integrity, digital summaries, digital signatures, and more.
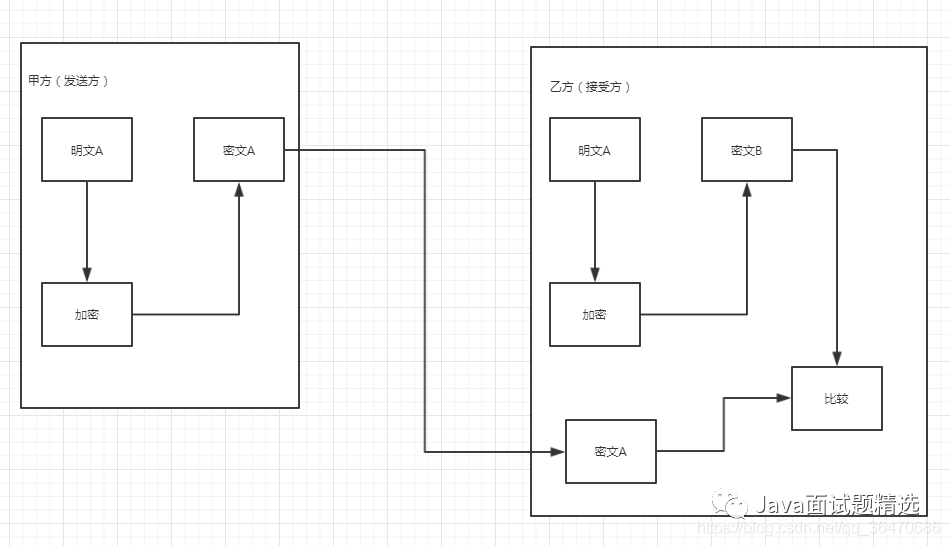
One-Way Encryption Process
1. The sender encrypts the plaintext using a one-way encryption algorithm to generate a fixed-length ciphertext string, which is then transmitted to the receiver.
2. The receiver uses the same one-way encryption algorithm to encrypt the plaintext for comparison, obtaining the encrypted ciphertext string.
3. This is compared with the ciphertext string sent by the sender; if the ciphertext strings before and after transmission match, it indicates that the data was not damaged during transmission; if they do not match, it indicates data loss occurred during transmission.
Illustration:
Common Algorithms
MD5, SHA1, SHA224, etc.
5. Key Exchange
Key exchange IKE (Internet Key Exchange) usually refers to both parties exchanging keys to achieve data encryption and decryption.
Common key exchange methods include the following two:
1. Public Key Encryption
The public key is encrypted and transmitted over the network for the other party to decrypt. The downside is that it has a high possibility of being intercepted and cracked, so it is not commonly used.
2. Diffie-Hellman
The DH algorithm is a key exchange algorithm that is neither used for encryption nor for generating digital signatures.
The DH algorithm encrypts using common parameters, private parameters, and algorithm information shared between both parties. Then both parties exchange the calculated results and perform special algorithms with their private parameters. The results calculated by both parties will be the same, and this result will be the key.
For example:
A has parameters p and g, and A has a private parameter x; B has parameters p and g, and B has a private parameter y. A and B use the same encryption algorithm to compute the corresponding values: value_A = p^(x % g), value_B = p^(y % g). They then exchange the computed values and use their private parameters to compute the power: A, upon receiving value_B, computes x square to get value_B^x = p^(xy % g); B, upon receiving value_A, computes y square to get value_A^y = p^(xy % g); the final results are consistent.
Security
During the entire process, third parties can only obtain the values of p and g, while the results exchanged between A and B are secure.
How to Confirm the Legitimacy of the Public Key Source?
Answer: Use a public key certificate.
Public Key Infrastructure (PKI)
The public key infrastructure is a collection of hardware, software, personnel, policies, and procedures.
Uses
To implement the generation, management, storage, distribution, and revocation of keys and certificates based on public key cryptography.
Components
Certificate Authority (CA), Registration Authority (RA), Certificate Revocation List (CRL), and Certificate Repository (CB).
Public Key Certificate
A public key certificate is a digitally signed declaration that binds the value of the public key to the identity of the individual, device, or service holding the corresponding private key. The generation of public key certificates follows the specifications of the X.509 protocol, and its content includes: certificate name, certificate version, serial number, algorithm identifier, issuer, validity period, effective start date, effective end date, public key, certificate signature, and more.
CA (Certificate Authority) Certificate Authentication Process
1. Client A prepares the digital information (plaintext) to be transmitted. (Preparing plaintext)
2. Client A performs a hash operation on the digital information to obtain a message digest. (Preparing digest)
3. Client A uses the CA’s private key (SK) to encrypt the message digest, obtaining Client A’s digital signature, which is attached to the digital information. (Signing the digital information with the private key)
4. Client A randomly generates an encryption key (DES key) and uses this key to encrypt the information to be sent, forming ciphertext. (Generating ciphertext)
5. Client A encrypts the randomly generated encryption key with the shared public key (PK) and transmits the encrypted DES key along with the ciphertext to B. (Asymmetric encryption, encrypting the DES key with the public key)
6. Bank B receives the ciphertext and the encrypted DES key from Client A, first using its private key (SK) to decrypt the encrypted DES key to obtain the DES key. (Decrypting the DES key with the private key)
7. Bank B then uses the DES key to decrypt the received ciphertext to obtain the plaintext digital information, discarding the DES key afterward (making the DES key invalid). (Decrypting the ciphertext)
8. Bank B uses the shared public key (PK) to decrypt Client A’s digital signature, obtaining the message digest. Bank B performs the same hash algorithm on the received plaintext to obtain a new message digest. (Decrypting the digital signature with the public key)
9. Bank B compares the received message digest with the newly generated one; if they match, it indicates that the received information has not been modified. (Comparing message digest and information)
How to Ensure the CA’s Public Key Has Not Been Tampered With?
The answer is that there is no way to ensure the CA’s public key has not been tampered with. Typically, operating systems and browsers pre-install some CA certificates locally. Therefore, senders should apply for digital certificates from certified CAs for assurance.
However, if malicious CA certificates are inserted into the system, it is still possible to send counterfeit public keys via fake digital certificates to validate fraudulent information. Therefore, the security premise is that illegal CA certificates cannot be inserted into the system.
References:
-
https://www.jianshu.com/p/ce3893a7be09 -
https://www.cnblogs.com/devdeng/p/5334038.html -
https://blog.csdn.net/lycb_gz/article/details/78047417 -
https://blog.csdn.net/tanyjin/article/details/61913987 -
https://www.jianshu.com/p/3d8de6ae87d6
END
十期推荐
【201期】面试官:String长度有限制吗?是多少?还好我看过
【202期】面试官:GET 和 POST请求的本质区别是什么?(本质没区别)
【203期】吃透Java IO:字节流、字符流、缓冲流
【204期】面试官:你手写过堵塞队列吗?
【205期】面试官:数据量很大的情况下,对于分页查询你有什么优化方案吗?
【206期】面试官:你的项目是如何处理重复请求/并发请求的?
【207期】19张图带你梳理SpringCloud体系中的重要知识点!
【208期】敲黑板,也来谈如何设计一个秒杀系统(重点)
【209期】架构设计&分布式&数据结构与算法面试题(2020最新版)
【210期】面试官:说说常用的Redis和zk两种分布式锁的对比
与其在网上拼命找题? 不如马上关注我们~