
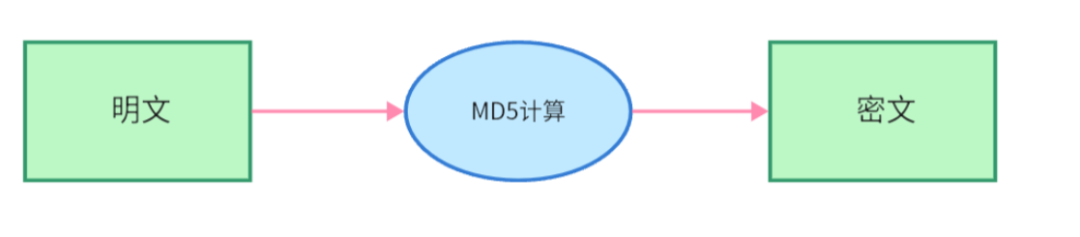

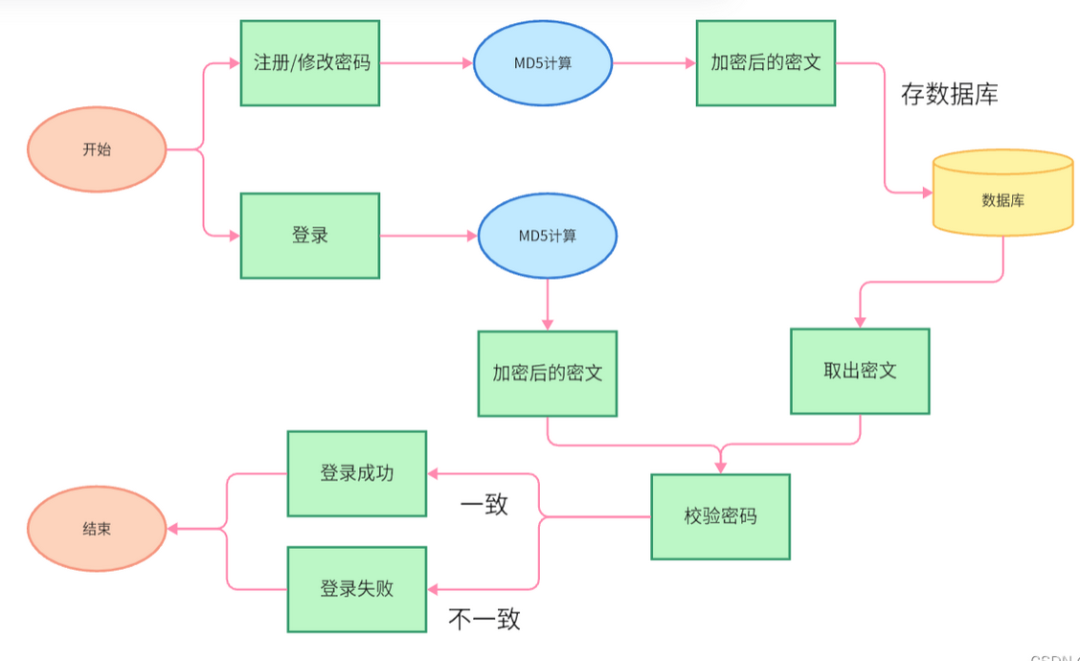

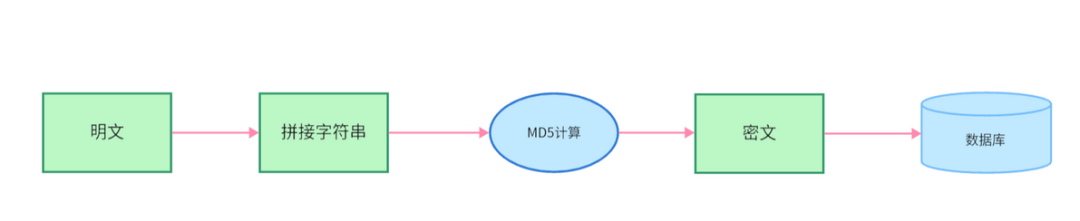



A generates a pair of keys (public key and private key), with the private key kept secret by A. The public key is public and can be accessed by anyone.
A uses their private key to sign the message, generating a signature, and sends the signed message along with the original message to B.
B receives the message and uses A’s public key to verify the signature. If the verification result matches the original message, it proves that the message was sent by A.
