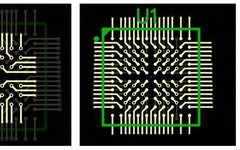
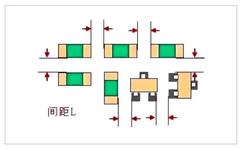
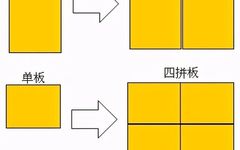
PCB Layout and Wiring: Essential Guidelines
PCB, also known as Printed Circuit Board, enables the connection of electronic components and the realization of functions. It is also an important part of power circuit design. This article will introduce the basic rules for PCB layout and wiring. Basic Rules for Component Layout 1. Layout according to circuit modules. Related circuits with the … Read more