Hackers never sleep, so how can enterprises afford to let their defenses down? Attackers particularly favor launching attacks during non-working hours—when security personnel are fewer, significantly delaying incident response and resolution times. When retail giant Marks & Spencer faced a security incident over the Easter weekend, its e-commerce platform, which accounted for one-third of its clothing and home sales, was forced to shut down completely.
The dispersion of personnel during holidays leads to delays in assembling the incident response team, giving attackers a longer window for lateral movement. While not all enterprises can establish a 24/7 internal team, building a 24/7 Security Operations Center (SOC) remains one of the most effective proactive defense strategies. This article will explore the importance of 24/7 monitoring, implementation challenges, and six key practices.
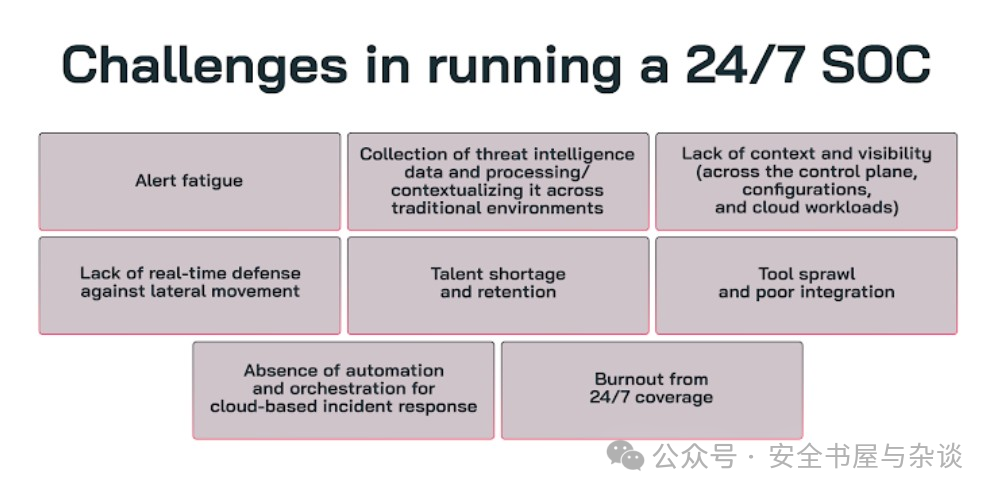
The Importance and Challenges of a 24/7 SOC
As the nerve center of enterprise network defense, the SOC plays a critical role in continuously monitoring, investigating, and responding to potential threats. When combined with automation technologies, its effectiveness is significantly enhanced—especially during critical periods when all personnel are on leave. However, achieving 24/7 SOC operations is no easy task; it requires a perfect balance of mature processes, advanced tools, and professional talent.
Thorough Planning and Automation Technologies are Key
When security teams struggle to cope with the ever-changing attack surface, artificial intelligence can shine. By combining professional teams with standardized processes, AI enhances efficiency through automated threat detection, accelerates response times, and strengthens overall security posture. The following analysis outlines the key elements of the construction process and the integration path of AI.
Six Key Steps to Building a 24/7 SOC
-
Establish a Foundational Framework Aligned with Enterprise Characteristics Building a robust SOC begins with a clear task positioning that aligns with enterprise goals. A well-defined strategy helps determine the scope of security coverage, and a sufficient budget justification is crucial—recent frequent major cyberattack incidents provide strong evidence for this. The choice of SOC model should comprehensively consider risk profiles, compliance requirements, and resource endowments: healthcare institutions prioritize HIPAA compliance, while retailers focus on PCI DSS standards. Regardless of whether an internal, hybrid, or outsourced model is adopted, AI technologies should be introduced to optimize operations; for example, a hybrid SOC equipped with AI analytics can achieve efficient operations.
-
Build a Skilled Team and Provide Continuous Training A multi-tiered talent pipeline is needed: junior analysts handle alert triage, mid-level focus on investigation and response, and senior members concentrate on strategic planning and AI tool optimization. When resources are limited, a dual-layer structure can still achieve effective coverage through reasonable division of labor. It is recommended to prioritize internal talent selection and establish a continuous training mechanism, such as guiding team members to use AI tools to address pain points like SIEM log management costs or SOAR configuration complexities.
-
Implement a Scientific Scheduling Mechanism to Prevent Burnout Innovative scheduling systems, such as 4 days on/4 days off, can be employed, allowing multinational companies to allocate personnel across time zones. Maintaining a 15-20% personnel redundancy ensures flexible scheduling, while regularly rotating responsibilities such as alert triage and script review is essential. An overlapping handover mechanism should be established to facilitate information transfer, and AI should be used to automate repetitive tasks like log analysis. Implementing health programs, establishing anonymous feedback channels, and strictly enforcing rest policies are all crucial. Regular team recognition events can also significantly enhance retention rates.
-
Select Intelligent Security Tools When evaluating AI-driven tools, it is necessary to weigh cost-effectiveness against operational complexity. Traditional SIEMs face scalability bottlenecks, while static SOAR scripts struggle to address new threats. For example, Radiant’s adaptive AI platform can automatically validate true positive alerts and respond quickly; its maintenance-free features and 95% accuracy effectively address the limitations of EDR coverage and the high operational costs of SIEMs. This platform also supports one-click remediation and seamless integration with existing environments.
-
Foster a Culture of Continuous Learning Establish a non-punitive post-incident analysis mechanism to convert experiences into a knowledge base. Provide certification support such as GIAC Intrusion Analyst (GCIA) and optimize processes through red-blue team exercises. Regularly conduct executive stress test decision-making drills and strengthen collaborative training across multiple departments, including legal and public relations.
-
Enhance Governance and Measurement Systems Set core metrics such as Mean Time to Detect (MTTD)/Mean Time to Respond (MTTR) and AI accuracy rates. Real-time dashboards should display alert load balancing across different time periods, and monthly analysis reports should include deep insights into tool effectiveness and team health. Notably, a low false positive rate not only alleviates the burden on analysts but is also key to establishing trust in automation.
When professional talent, optimized processes, advanced AI, and intelligent tools come together, enterprises can effectively avoid becoming headlines. A 24/7 AI-enhanced SOC overcomes the inherent flaws of traditional SIEMs, SOARs, and other solutions through seamless collaboration between automation and human experts. This significantly reduces overall costs while improving operational efficiency. This innovative model is redefining the standards of modern security operations.