The Top Red Team in the US is Actually an AI Robot
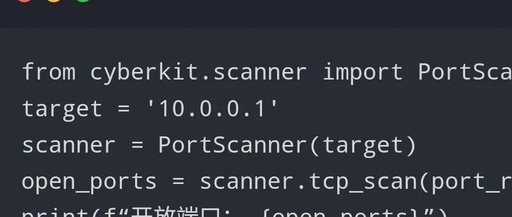
Part01 Chatbot “Xbow” Ranks First on HackerOne The performance of artificial intelligence (AI) has surpassed that of human red team members. On the HackerOne platform, an AI chatbot named “Xbow” currently ranks first in the reputation leaderboard of the US security industry. The platform connects businesses with ethical hackers through a bug bounty program, and … Read more