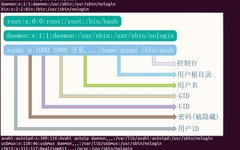
Linux Privilege Escalation Techniques (Part 1)
• 1. Basics of Linux Permissions • Linux Permission Management • Linux Security Mechanisms • 2. Understanding Various Shells • Interactive Shell and Non-Interactive Shell • Forward Shell and Reverse Shell • Common Reverse Shell Commands • 3. Information Gathering in Linux • Manual Enumeration of Basic Linux Information • Automated Enumeration of Basic Linux … Read more