About WEF
Feature Introduction
Log Generation WPA/WPA2, WPS, and WEP Attacks Automated Handshake Cracking Multiple Templates for EvilTwin Attacks Check Monitor Mode and Status 2Ghz and 5Ghz Attacks Custom Dictionary Selector Automated Detection Bluetooth Support (Interference, Read, Write)
Supported Testing Types
Deauthentication Attacks Authentication Attacks Beacon Flooding Attacks PMKID Attacks EvilTwin Attacks Passive/Stealth Attacks Pixie Dust Attacks Null Pin Attacks Chopchop Attacks Replay Attacks Michael Exploitation Attacks Caffe-Latte Attacks Interference, Read and Write Bluetooth Connections GPS Spoofing with HackRF
Tool Requirements
aircrack-ng reaver mdk4 macchanger hashcat xterm hcxtools pixiewps python3 btlejack crackle php hostapd dnsmasq
Tool Installation
git clone https://github.com/D3Ext/WEF
cd WEF
bash setup.shgit clone https://github.com/D3Ext/WEF && cd WEF && bash setup.shAdditional Requirements for Arch Linux
curl -O https://blackarch.org/strap.sh
chmod +x strap.sh
sudo ./strap.sh
pacman -S base-devel libnl openssl ethtool util-linux zlib libpcap sqlite pcre hwloc cmocka net-tools wpa_supplicant tcpdump screen iw usbutils pciutilsTool Usage
# Different devices may have different interfaces
wef -i wlan0
wef --interface wlan0# Specify the name of the test
set name my-wifi
# Set the time interval for each test
set time 60
# Specify the number of packets to send for each test
set packets 15Tool Usage Demonstration
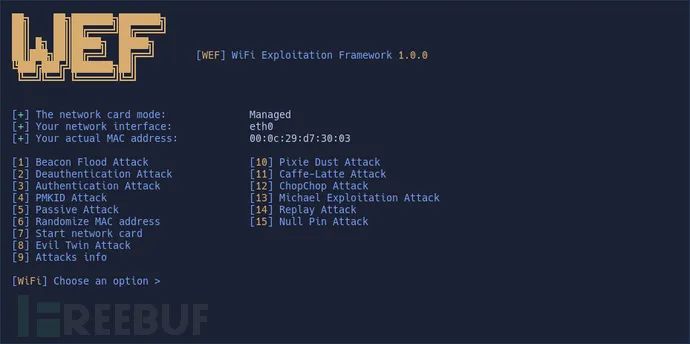
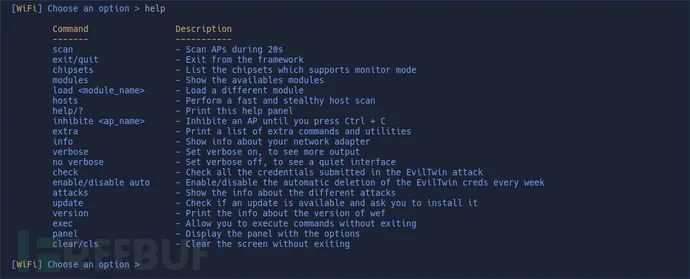
License Agreement
Project Address
Source: FreeBuf.com
The technologies, ideas, and tools involved in the articles published or reprinted by Heibai Zhidao are for educational and communication purposes only for security. No one may use them for illegal purposes or for profit; otherwise, they will bear the consequences themselves!
If there is an infringement, please private message us to delete the article
END
