About Gallia
Gallia is an extensible penetration testing framework focused on automotive security. This tool can perform penetration testing on an entire vehicle and even test individual vehicle ECUs. Currently, Gallia mainly targets the UDS interface and utilizes a modular design to implement logging and archiving functionalities separately. As a general interface, the logging function enables repeatable testing and supports subsequent processing tasks.
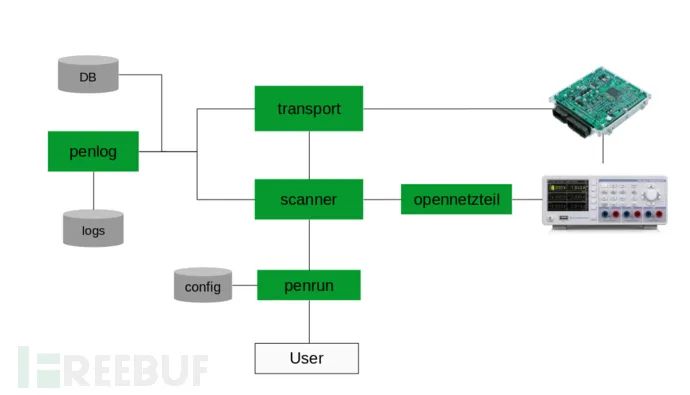
Tool Architecture
The diagram below shows the internal modules and operational mechanism of Gallia:
Tool Dependencies
Linux>= 5.10
Python>= 3.9
poetry (optional, for development)
dumpcap (optional, WireShark component)
The Python dependency components can be viewed in the project’s pyproject.toml file.
Scanning Modes
Standard UDS scanning typically includes the following steps:
1. Search for ECU on the relevant device: discovery scan;
2. Search for UDS services on the found ECU: service scan;
3. Search for UDS identifiers among the discovered UDS services: identifier scan;
4. Scanning for other specific services: such as memory scanning, fuzz testing, etc.;
Discovery Scan
The discovery scan is specific to the underlying transport, such as DoIP or ISO-TP. The idea is to formulate an effective UDS payload. The normal working payload is 1001, which is also required by the DiagnosticSessionControl service. This request allows the ECU to modify the DefaultSession. Both the DiagnosticSessionControl service and DefaultSession are always available, so this payload is the best choice. In addition, payload 1003 can also be used, as many ECUs provide audible feedback when enabling ExtendedDiagnosticsSession (session ID 0x03).
The addressing of the ECU is provided by the underlying transport protocol, and in most cases, there are two addresses: tester address and ECU address. The basic idea of the discovery scan is to send a valid UDS payload to all valid ECU addresses using a fixed tester address. When a valid response is received, it indicates that the ECU has been found.
Service Scan
The service scan operates at the UDS protocol level, where UDS provides several nodes called services. Each service has an identifier and a specific parameter list, and the scanning process uses a fixed payload to request all possible services. The payload does not have to be specific; it can be empty or all zeros. Some ECUs may behave unstably when receiving invalid payloads.
To identify available services, the tool uses a reverse matching mechanism. According to UDS standards, when a request for an unsupported service is made, the ECU will respond with the error codes serviceNotSupported or serviceNotSupportedInActiveSession. Therefore, every service that responds with a different error code is considered available.
Identifier Scan
The identifier scan operates at the UDS protocol level, more specifically at the level of specific UDS services. Most UDS services require an identifier as an input parameter. For example, the ReadDataByIdentifier service requires a data identifier for the requested resource. To find out the available identifiers for a specific service, the tool introduces the identifier scan.
To identify available data identifiers, the tool uses a reverse matching mechanism. According to UDS standards, when a request for an unsupported service is made, the ECU will respond with the error codes serviceNotSupported or serviceNotSupportedInActiveSession. If the ECU responds with any of serviceNotSupported, serviceNotSupportedInActiveSession, subFunctionNotSupported, subFunctionNotSupportedInActiveSession, or requestOutOfRange, the identifier is considered unavailable.
Some services (such as RoutineControl) also provide a sub-function, which can discover sub-function parameters using the same technique, but the error codes for reverse matching differ. To discover available sub-functions, the following error codes indicate that the sub-function is unavailable: serviceNotSupported, serviceNotSupportedInActiveSession, subFunctionNotSupported, or subFunctionNotSupportedInActiveSession.
Every identifier or sub-function that responds with a different error code is considered available.
Tool Installation
Arch Linux
paru -S gallia
Manual Installation
pip install galliaTool Usage
$ gallia simple-dtc --target "isotp://can0?src_addr=0x123&dst_addr=0x312&tx_padding=0xaa&rx_padding=0xaa" read
Project Address
https://github.com/Fraunhofer-AISEC/gallia
Detailed Documentation :
https://fraunhofer-aisec.github.io/gallia/
References
https://www.iso.org/standard/72439.html
https://fraunhofer-aisec.github.io/gallia
https://www.secforcars.de/
https://www.iso.org/standard/74785.html
https://www.iso.org/standard/66574.html