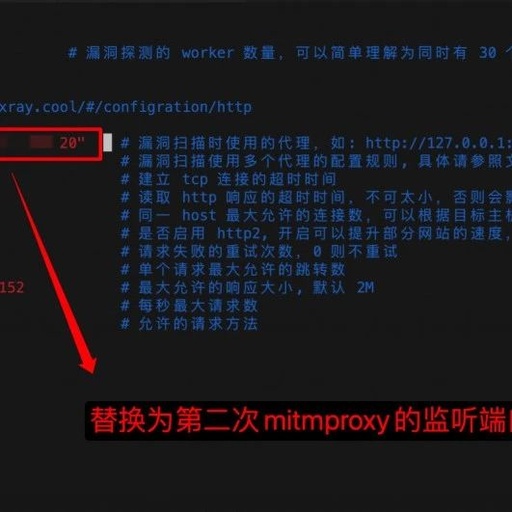
Essential Linux Commands for Hackers: 10 Practical Tips
During penetration testing, the Linux command line is like a Swiss Army knife: compact yet powerful. Today, we will discuss ten particularly useful Linux commands that can make a hacker’s work more efficient and open the eyes of network security enthusiasts. Explore System Information: uname -a Want to know about your target machine? uname -a … Read more