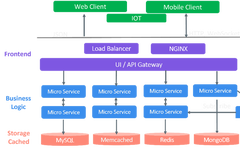
PyRedis: The Python Interface for Efficient Redis Operations!
▼ Click the card below to follow me ▲ Click the card above to follow me PyRedis: The Python Tool for Efficient Redis Operations! Redis is the most popular in-memory database today, and PyRedis is a powerful tool for operating Redis with Python. Today, we will unveil this powerful client library and teach you how … Read more