About BlueBunny
BlueBunny is a powerful command control framework that enables data communication based on Low Energy Bluetooth, allowing researchers to send control commands directly to the Bash Bunny via Bluetooth.

What is Bash Bunny
Bash Bunny is a multifunctional USB attack tool similar to USB Rubber Ducky (claimed to be the world’s most advanced USB attack platform). However, Bash Bunny is a fully functional Linux operating system, offering more advantages over USB Rubber Ducky, such as the ability to carry multiple advanced payloads, simulate device combinations, and execute various advanced attacks. This is something penetration testers looking to elevate their physical attacks would highly value.
Tool Operation Process & Architecture
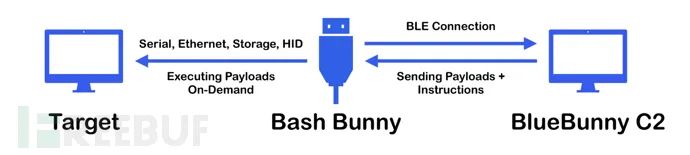
Tool Installation
Since this tool is developed based on Python, we first need to install and configure the Python environment on our local device.
Next, researchers can use the following command to clone the project source code to their local machine:
git clone https://github.com/90N45-d3v/BlueBunny
cd BlueBunny/C2
(向右滑动,查看更多)
Dependency Installation
Use the following command to install the required dependencies for this tool:
pip install pygatt "pygatt[GATTTOOL]"
Then installBlueZ, and ensure gatttool is available:
sudo apt install bluez
Tool Usage
The following command can be used to start the C2 server:
sudo python c2-server.py
Then insert the Bash Bunny with the BlueBunny payload into the target device, with the payload path as follows:
BlueBunny/payload.txt
Open a web browser and visit the following address to connect and communicate with your Bash Bunny:
http://localhost:1472
Communicate with Bash Bunny Manually via Python Script
We can also manually communicate with your Bash Bunny using BlueBunny’s Low Energy Bluetooth (BLE) backend.
Below is a reference Python script code:
# Import backend script (BlueBunny/C2/BunnyLE.py)
import BunnyLE
# Define the data to be sent
data = "QUACK STRING I love my Bash Bunny"
# Define the type of data to be sent, either "cmd" or "payload", payload data will be temporarily written to a file, similar to executing multiple commands in a Payload script file
d_type = "cmd"
# Initialize BunnyLE
BunnyLE.init()
# Connect to Bash Bunny
bb = BunnyLE.connect()
# Send and execute data
BunnyLE.send(bb, data, d_type)
(向右滑动,查看更多)
License Agreement
This project is developed and released under the MIT open source license agreement.
Project Address
BlueBunny:https://github.com/90N45-d3v/BlueBunny



http://www.bluez.org/download/