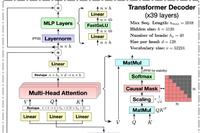
Technical Interpretation of DeepSeek (1) – A Comprehensive Understanding of MLA (Multi-Head Latent Attention)
Zhihu: Jiang Fuchun (Authorized) Link: https://zhuanlan.zhihu.com/p/16730036197 Editor: “Deep Learning Natural Language Processing” WeChat Official Account Introduction DeepSeek has recently gained significant attention, and I have been following some of the technical reports released by DeepSeek. They have consistently surprised everyone with their model training, inference performance, and computational costs. After reading DeepSeek’s technical reports, I … Read more