Improvement of DES Encryption Algorithm
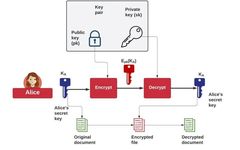
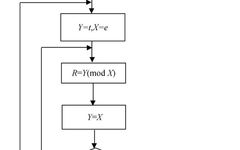
ClickBlue TextFollow Us Abstract: The symmetric and asymmetric cryptographic systems each have their own advantages and disadvantages.Exploring a hybrid cryptographic system that combines both, retaining their advantages while maximizing the elimination of their disadvantages, is of great significance for the efficiency and security of modern network communication.Using asymmetric encryption to protect symmetric key is a … Read more