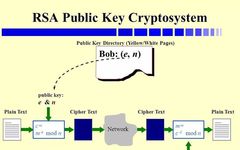
Public Key Encryption Based on Large Prime Numbers – RSA Algorithm
Follow Encounter Mathematics, and discover a more wonderful you Image from: https://slideplayer.com/slide/5369780 The following text is excerpted from “Mathematics Kaleidoscope 2”, with permission from People’s Post and Telecommunications Press, [Encounter Mathematics] expresses gratitude! Modular arithmetic has led to an important development in cryptography: public key encryption. All cryptography relies on keys, and the greatest risk … Read more