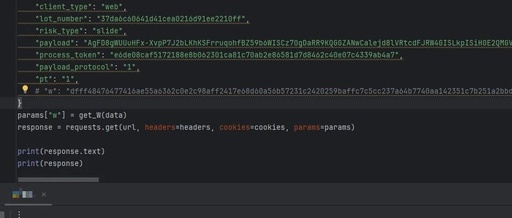
Step-by-Step: Implementing a Blockchain Client Based on RSA Algorithm Using Python
Big Data Digest Work Compiled by: Wan Jun, Molly, Jiang Bao Shang Blockchain, as the core technology behind Bitcoin and other cryptocurrencies, has attracted global attention in recent years. However, countries have varying attitudes towards this disruptive technology. Its decentralized distributed structure allows users to communicate directly without the need for a central node, which … Read more