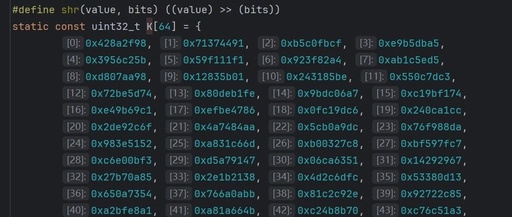
The Essence of Non-Competition Between the ‘Giants’ in the Global Analog Chip Industry
As the “giants” in the global analog chip industry, ADI (Analog Devices) and TI (Texas Instruments) have managed to avoid vicious competition and achieve peaceful coexistence for a long time, despite being in the same industry. The core reason lies in their deep differentiation in strategic positioning, technological routes, and market layouts, forming a complementary … Read more