Click the blue text
Follow us

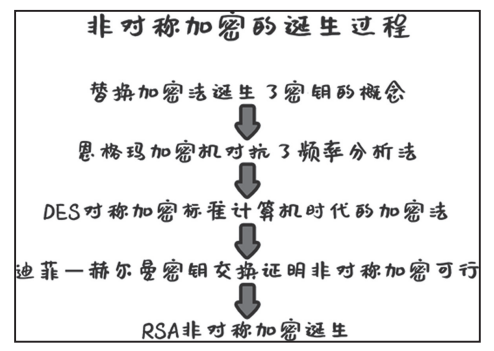
The Birth of Asymmetric Encryption
What is a Key
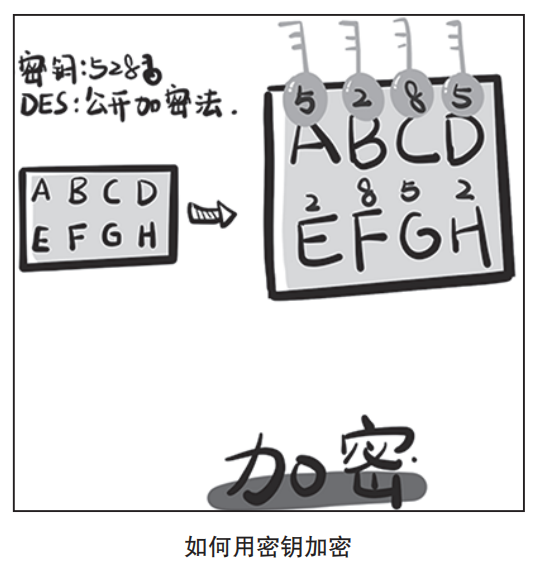
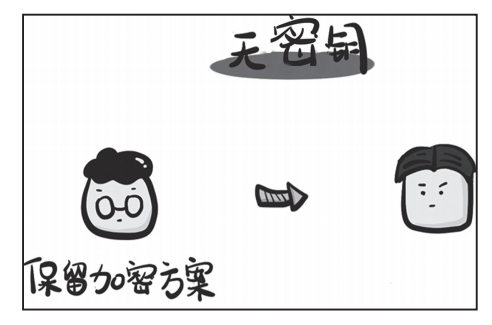
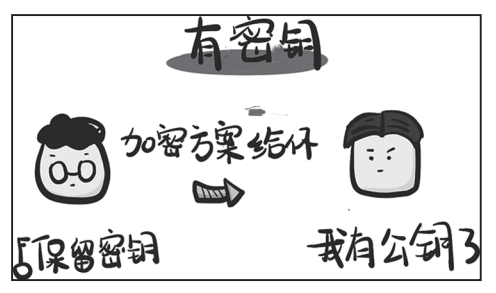
The Birth of RSA Asymmetric Encryption
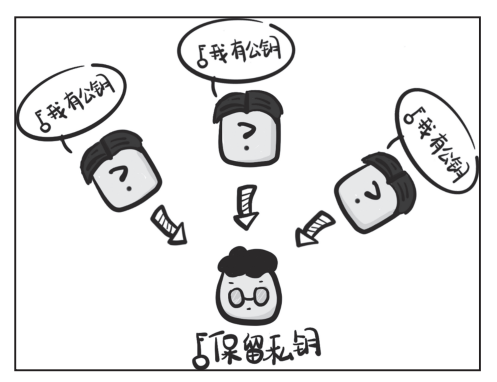
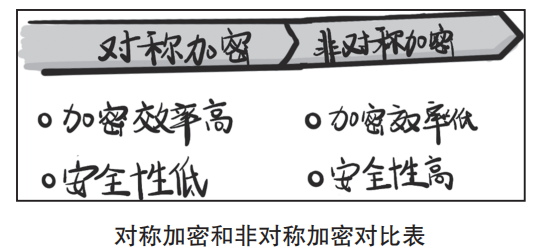
Characteristics of Asymmetric Encryption
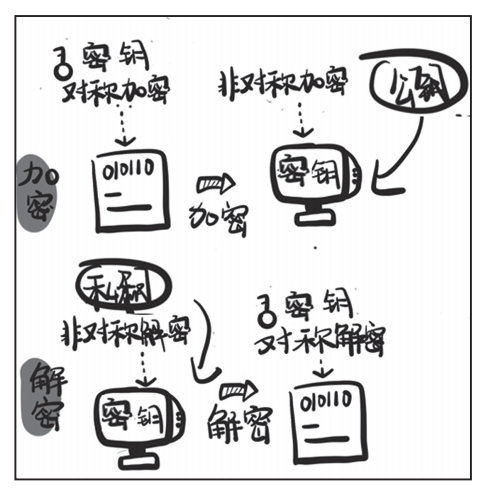
PGP Software: Public Key Encrypts, Private Key Decrypts
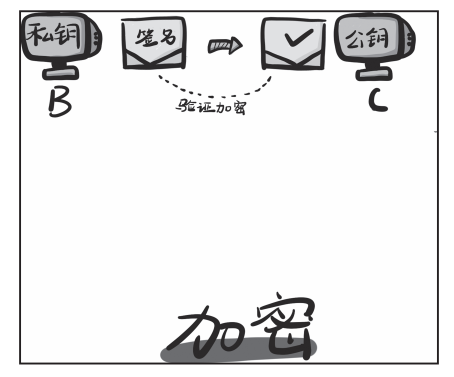
Blockchain Transfer Signature:
Private Key Encrypts, Public Key Decrypts

Author Profile
If you like this article, please give it a “Like“~~~
Read the original text