20 Lines of Python Code for Encrypted Communication
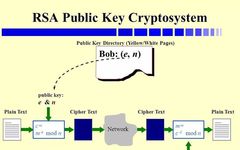
1. Introduction The internet is filled with eavesdropping, and our information can easily be obtained by malicious individuals, causing us negative impacts. If you need to transmit confidential or sensitive personal information over the internet, you may need to encrypt it to guard against prying eyes. Using online or mobile encryption software may also expose … Read more