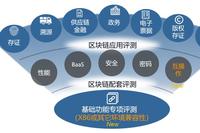
Interpretation of the Seventh Batch of Trusted Blockchain Evaluation System by China Academy of Information and Communications Technology – Basic Functions
As a new type of information technology, blockchain systems exhibit varying degrees of functionality completeness, security, scalability, performance, and maturity. Through multidimensional and in-depth evaluations of blockchain-related products, shortcomings can be identified and addressed, thereby resolving issues related to the sustainability of blockchain applications caused by technical problems and redundant constructions. Introduction to the “Trusted … Read more