In recent years, with the rapid development of technologies such as artificial intelligence, 5G, and the Internet of Things, the volume of data has continued to rise. At the same time, the number of cybercrimes has also increased, leading to escalating losses. According to statistics from research institutions like Statista and Cybersecurity Ventures, the total global data volume reached 149ZB in 2024, and it is expected to continue growing at a high compound annual growth rate in the following years; the losses caused by global cybercrime in 2024 are as high as $9.5 trillion, reflecting the increasingly rampant and complex nature of cyberattacks.
The high losses caused by cybercrime are fundamentally due to security vulnerabilities being exploited by hackers. They trigger a series of issues such as information leaks and online fraud through attack methods like ransomware, phishing, and Trojans. Within the entire data security protection system, Multi-Die systems (multi-chip integrated systems) have become a focal point due to their complex hardware architecture and interconnectivity characteristics. Dana Neustadter, Senior Director of Security Solutions Product Management at Synopsys, stated: “Multi-Die systems are the trend of the future, but they also bring new security challenges. Security for Multi-Die systems needs to be further extended based on SoC, and due to their higher ecological complexity, standardization is key to unlocking the potential of Multi-Die systems, while supply chain security must also be elevated to new heights.”
To achieve security throughout the entire lifecycle of Multi-Die systems, Synopsys provides solutions such as Physical Unclonable Functions (PUF), Hardware Security Modules (HSM), and post-quantum cryptography, helping developers achieve efficient results when building secure systems.
New Cybersecurity Landscape and Strategies for Multi-Die Systems
Data shows that the increase in data value and the expansion of attack surfaces create a “vicious cycle” where traditional security boundary protection models (such as firewalls) are gradually becoming ineffective, necessitating a shift to higher-level global protection. Especially, enterprise financial systems and individual users have become primary targets for cyberattacks.
The emergence of quantum computing has made the cybersecurity landscape even more severe. Its unique quantum mechanical properties pose a “dimensionality reduction attack” on traditional public key algorithms (such as RSA and ECC). For example, Shor’s algorithm can crack widely used long-key encryption systems in a short time, which means that modern cryptographic systems face the risk of collapse. However, in response to the threat of quantum computing, the cryptography community is undergoing a paradigm revolution. Post-quantum cryptography (PQC) has established a mathematical cryptographic system that can be implemented on existing electronic computers, capable of resisting future quantum computing attacks. Currently, post-quantum cryptography has developed multiple technical branches, including hash-based post-quantum cryptographic algorithms, code-based post-quantum cryptographic algorithms, and lattice-based post-quantum cryptographic algorithms.
In the new cybersecurity landscape, chips, as the core of system architecture, also face unprecedented challenges. In traditional chip design, security modules are often additional features, but with the frequent occurrence of global cyberattack incidents in recent years, security modules have become essential components in applications involving information security. As Multi-Die gradually becomes one of the mainstream design methods for large chips, new and more complex challenges arise.
Multi-Die packages multiple dies (small chips) together, and its system design relies on global division of labor. In Multi-Die systems, different vendors’ chiplets are interconnected via UCIe/PCIe, utilizing advanced 2.5D and 3D packaging technologies to achieve dimensional upgrades in chip design and address various issues such as heterogeneous integration, design planning, power consumption, heat dissipation, and die-to-die connections. However, the upgrade at the system level also leads to the failure of the traditional SoC single-chip root of trust (RoT) mechanism. Additionally, some untrusted foundries or third-party IPs may implant hardware Trojans or tamper with data stored in OTP, such as encryption keys, device unique identifiers (IDs), and secure boot codes, turning the entire Multi-Die system into a “backdoor” for hackers to steal information.
To enhance system security, Multi-Die design must establish a multi-dimensional defense system from various aspects, including hardware architecture, supply chain, communication interfaces, cryptographic systems, and standardized collaboration. For instance, in hardware architecture design, each die entering the Multi-Die system should have traceability. PUF (Physical Unclonable Function) is an important hardware security technology that utilizes the inherent properties of silicon-based semiconductors to extract random and unclonable physical features, generating a “silicon fingerprint” similar to a biological fingerprint, serving as a hardware credential for supply chain traceability and identity authentication.
Communication interfaces are also key points for hacker attacks. Interfaces like PCIe and CXL transmit large amounts of data, and hackers may initiate root access attacks to steal confidential information or tamper with code execution through these interfaces, thereby invading core units such as memory. Adding security features such as authentication, key management, integrity, and data encryption (IDE) to PCIe and CXL interfaces can enable low-risk data transmission.
Of course, for Multi-Die to achieve widespread application, adherence to UCIe standards and Arm’s Platform Security Architecture (PSA) is crucial. Arm PSA is specifically designed to ensure the security of interconnected devices at scale, defining a standard programming environment and firmware for implementing and accessing security services within the device’s root of trust, with main functions including secure partitioning, secure partition manager (SPM), isolation mechanisms, RoT services, and secure IPC.
For the Chiplet design approach in the post-Moore’s Law era, the UCIe standard is not only a comprehensive specification for die-to-die interconnects, ensuring interoperability of compatible devices, but also has made significant efforts in security protection. On one hand, the PCIe and CXL interfaces on which the UCIe standard is based inherently possess security protection features; on the other hand, the UCIe 2.0 specification introduces an optional standardized system architecture that provides a common manageable architecture and hardware/software infrastructure to manage UCIe-based Multi-Die systems, supporting the holistic and dynamic deployment of security policies.
Synopsys Supports Achieving Multi-Die Lifecycle Security
Dana Neustadter believes that Multi-Die presents unprecedented challenges in terms of eavesdropping, tampering, man-in-the-middle attacks (MITM), cross-device attacks, and physical attacks, requiring a comprehensive approach to security boot, state protection, data protection, trusted computing, and supply chain security to build system integrity and achieve platform security.
At the same time, she introduced that to assist developers in building secure Multi-Die systems, Synopsys provides a full-stack solution, including SRAM PUF (secure silicon fingerprint), embedded hardware security module HSM, PCIe and CXL integrity and data encryption (IDE), and public key accelerator (PKA).
SRAM-based PUF
PUF is a core component for implementing Multi-Die systems, capable of generating unique, non-reproducible, and unclonable silicon fingerprints, serving as the basis for the root of trust and supply chain tracking. For chips, their threshold voltage is easily affected by environmental conditions such as temperature and voltage, making it unsuitable as a unique key or identifier, while SRAM cell PUF is much more stable than basic threshold voltage.
Synopsys’s SRAM-based PUF has integrated error correction, randomness extraction, security countermeasures, and anti-aging technologies into its products, enabling highly secure extraction of encryption keys from SRAM PUF and providing them in RTL netlist or software form. Compared to traditional key storage solutions like OTP (One-Time Programmable Memory), the significant advantage of Synopsys’s SRAM PUF in Multi-Die systems is that, in addition to high security and reliability, it also offers high flexibility and portability across process nodes, adapting to dies using different processes in Multi-Die systems while enhancing the supply chain security level of Multi-Die systems.
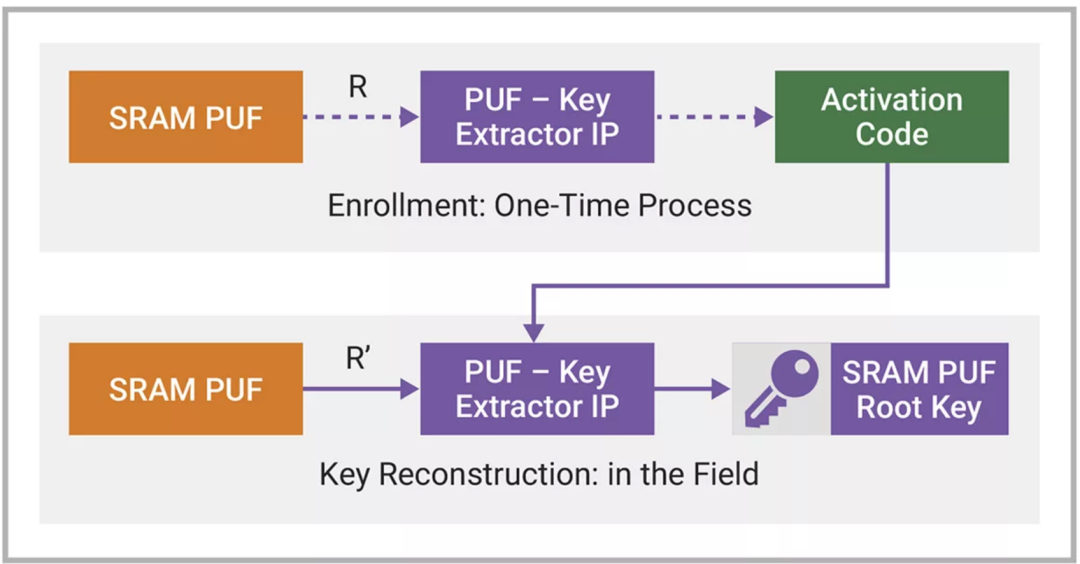
Figure 1: SRAM PUF Registration and Reconstruction Process.
(Image source: Synopsys)
DesignWare tRoot HSM
Synopsys’s DesignWare tRoot HSM, with its root of trust functionality, helps developers create a Trusted Execution Environment (TEE) to protect sensitive information and operations, and implement security-critical functions required throughout the device lifecycle, such as secure boot, storage, debugging, anti-tampering, and key management. Additionally, DesignWare tRoot HSM features a true random number generator (TRNG) compliant with NIST standards, with secure instruction and data controllers that include side-channel protection, supporting secure access to external storage and runtime tamper detection.
For Multi-Die systems, DesignWare tRoot HSM provides an immutable unique identity for functional dies in the system and extends the trust of that identity across the entire system. The software components of DesignWare tRoot HSM include a secure application software development kit (SDK), NIST-validated cryptographic libraries, device drivers, and reference designs, and support seamless integration with Physical Unclonable Functions (PUF) / Non-Volatile Memory (NVM), allowing developers to quickly integrate this security solution without needing specialized knowledge in writing secure software.
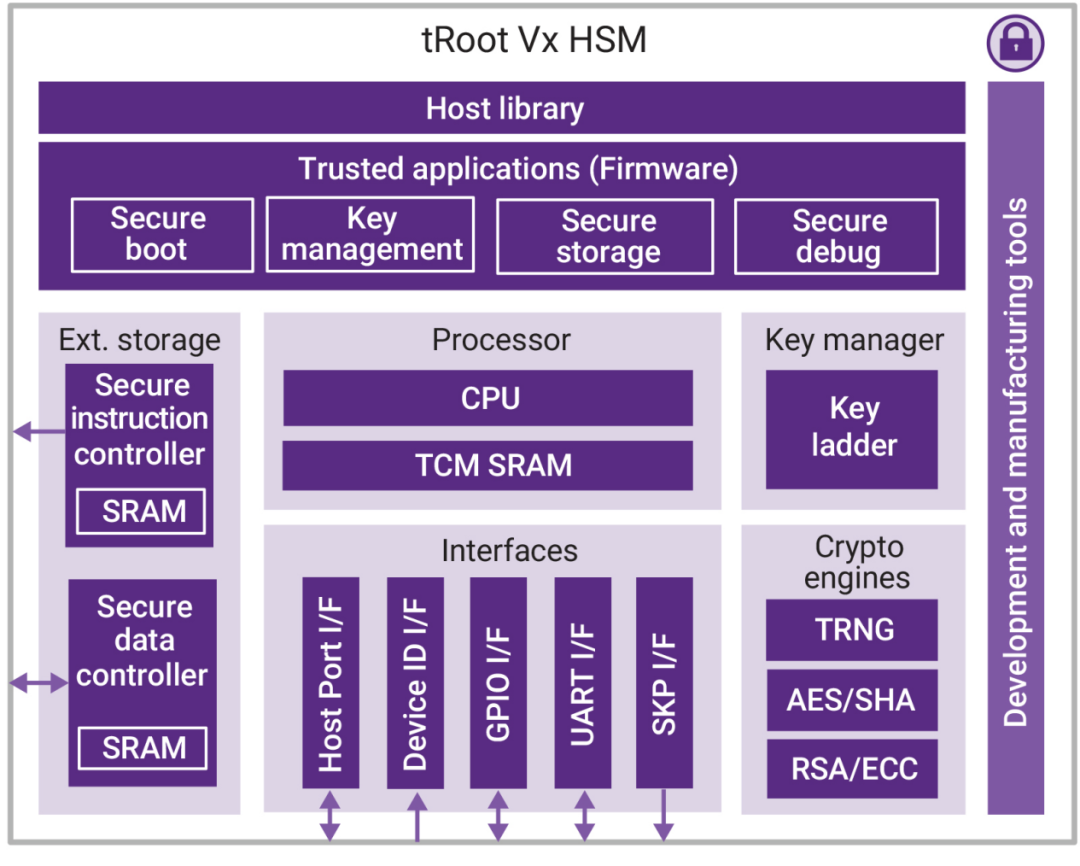
Figure 2: tRoot Vx HSM System Block Diagram.
(Image source: Synopsys)
PCIe and CXL IDE
The security features of PCIe and CXL interfaces mainly consist of authentication and key management, and IDE. Among them, IDE provides confidentiality, integrity, and replay protection for PCIe’s Transaction Layer Packets (TLP) and CXL’s Flow Control Units (FLIT), ensuring that data on the line cannot be observed, tampered with, deleted, inserted, or replayed. IDE is based on the AES-GCM encryption algorithm and receives keys from the authentication and key management security components.
Synopsys provides a complete PCIe 5.0/6.x/7.0 and CXL 2.0/3.x solution (including controller + IDE + PHY) for Multi-Die systems, which features many industry-leading characteristics:
-
High-performance, low-latency solutions supporting the latest standards;
-
Encryption/decryption/authentication of TLP/FLIT data packets based on a highly optimized AES-GCM algorithm;
-
Integration of advanced features such as PCRC checks, TDISP timestamp distribution, TSP transaction scheduling priority, and ordered bypass;
-
Covers all types of devices in the CXL protocol, including I/O, cache, and memory;
-
Supports dynamic key updates and efficient key control strategies, compliant with FIPS 140-3 security certification requirements.
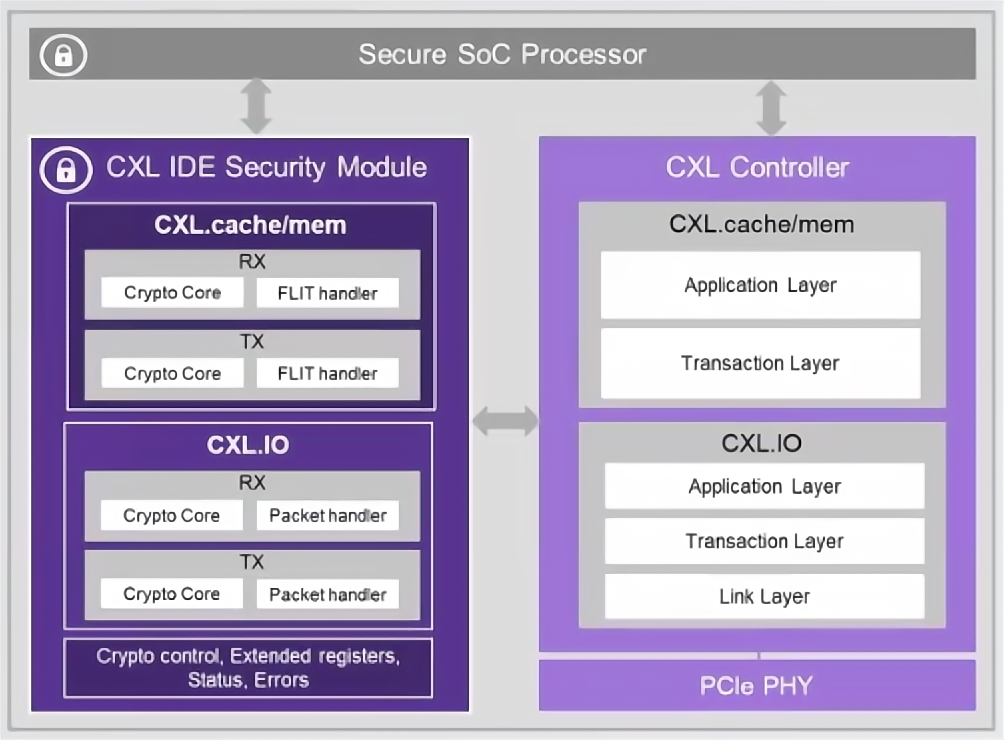
Figure 3: PCIe and CXL IDE.
(Image source: Synopsys)
Post-Quantum Cryptography Public Key Accelerator (PKA)
For building secure Multi-Die systems, post-quantum cryptography is crucial. With the development of quantum computing, traditional public key algorithms (RSA, ECC) will be compromised, and modern cryptographic systems face collapse, necessitating the adoption of new algorithms standardized by organizations like NIST. Previously, NIST released four new algorithms: CRYSTALS-Kyber, CRYSTALS-Dilithium, Falcon, and Sphincs + to counter quantum attacks.
Synopsys’s post-quantum cryptography public key accelerator (PKA) serves as an IP solution against quantum attacks, protecting various applications from the edge of the Internet of Things to the cloud from quantum computing threats through efficient collaboration between hardware and embedded firmware. This solution complies with NIST’s latest post-quantum digital signature, key encryption, and encapsulation algorithm standards, specifically covering:
-
ML-KEM (FIPS 203, formerly CRYSTALS-Kyber): An algorithm based on lattice problems, achieving a balance between security, efficiency, and ease of implementation, suitable for general encryption tasks.
-
ML-DSA (FIPS 204, formerly CRYSTALS-Dilithium): Also based on lattice problems, designed specifically for digital signatures, combining high security with efficient performance.
-
SLH-DSA (FIPS 205, formerly SPHINCS+): Adopts a stateless hash method, providing differentiated security assurance compared to lattice-based algorithms.
-
XMSS & LMS (SP 800-208): Based on Merkle tree structures, capable of securely and efficiently managing and verifying a large number of signatures, derived from the NIST standard released in 2020.
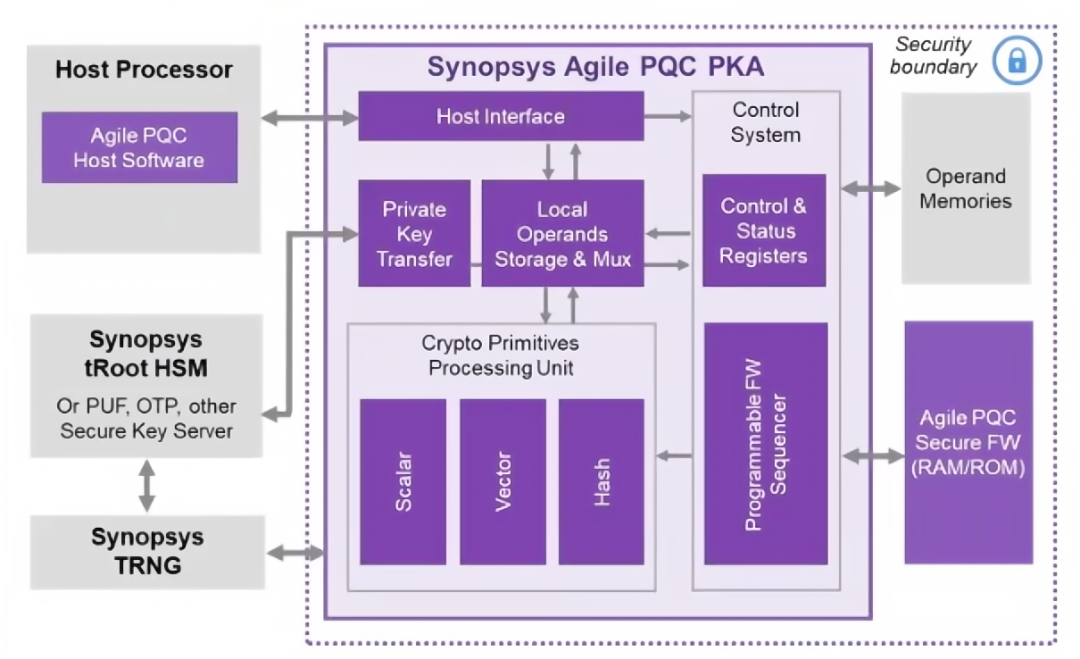
Figure 4: Post-Quantum Cryptography Public Key Accelerator (PKA) Solution Block Diagram.
(Image source: Synopsys)
Additionally, Synopsys’s post-quantum cryptography public key accelerator (PKA) meets FIPS 140-3 security certification, supports traditional ECC, RSA algorithms, and hybrid schemes, can resist side-channel attacks and fault injection attacks, and features high configurability and scalability, allowing for optimal tuning for performance, area, power consumption, and latency.
Dana Neustadter emphasized that more importantly, the launch and iteration of Synopsys’s aforementioned solutions always comply with UCIe standards.
In Conclusion
Cybersecurity threats are intensifying with technological advancements, and the global $9.5 trillion loss from cybercrime underscores the urgency of building a comprehensive security protection system. As the core architecture of the post-Moore era, Multi-Die systems bring performance breakthroughs while also becoming “high-value targets” for cyberattacks due to complex hardware interconnections, diverse supply chain ecosystems, and open communication interfaces.
To assist in creating secure and reliable Multi-Die systems, Synopsys offers a complete suite of solutions, including SRAM PUF, tRoot HSM, PCIe/CXL IDE, and post-quantum cryptography public key accelerator, covering the entire lifecycle of Multi-Die system design, manufacturing, and deployment, providing a practical path for the security trust system of heterogeneous integrated architectures.
END