
Abstract
This presentation introduces an adaptive fuzzing physical testing platform designed to identify vulnerabilities in automotive systems, with a particular focus on the Controller Area Network (CAN) bus. By employing “Automated Reverse Engineering Guided Fuzzing” (ARE – GF), our framework assesses the security resilience of CAN networks against complex attacks. The demonstration showcases a live fuzz testing process, the creation of a testing platform using affordable electrical components, real-time analysis of Electronic Control Unit (ECU) responses, and examples of discovered vulnerabilities, providing insights into advanced automotive cybersecurity testing methods.
1. Introduction
Modern vehicles are complex digital ecosystems, whose operation and safety depend on intricate networks. However, cybersecurity vulnerabilities within these networks can jeopardize road safety. This paper explores the critical interactions between Electronic Control Units (ECUs) facilitated by the CAN bus. Originally designed to ensure reliable communication, the CAN bus did not prioritize security, raising concerns about vulnerabilities. To address these challenges, we propose the ARE – GF framework, which combines automated reverse engineering to optimize fuzz testing efforts. By focusing on common CAN bus communication patterns, this framework can be applied to various vehicle models and other automotive networks, ensuring broad applicability and effectiveness across different scenarios. By addressing these vulnerabilities, we aim to enhance the overall security and resilience of modern automotive systems. The main contributions of this presentation include:
Modular testing platform: Replicating vehicle networks for precise simulation and vulnerability detection.
Adaptive fuzz testing: Targeted vulnerability discovery combined with real-time ECU response analysis.
Example demonstration: Showcasing the testing platform setup, ECU responses, and discovered vulnerabilities, validating the effectiveness of the approach.

2. Testing Platform Design and Implementation
The modular testing platform consists of the following components:
1. Multiple ECUs within the vehicle network.
2. CAN bus interface for ECU communication.
3. Control unit running custom fuzz testing software.
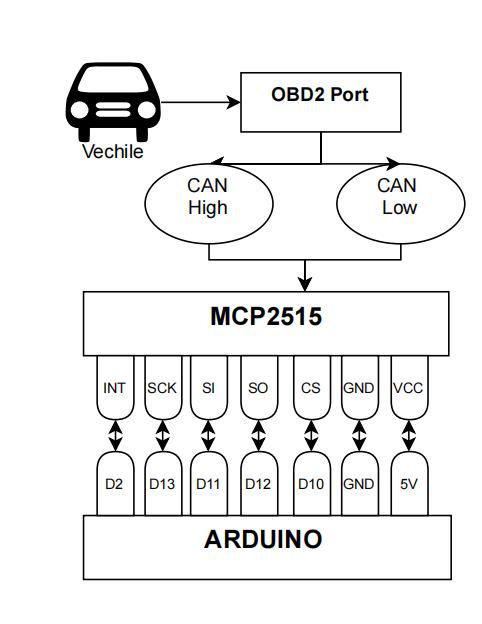
Figure 1. Test bench design connecting the vehicle to the fuzzing CAN network
The fuzz testing software generates various malformed CAN messages and analyzes the ECU’s responses to guide subsequent fuzz testing iterations. Figure 1 illustrates the architecture of the modular testing platform, highlighting the connection between the CAN bus interface and the physical testing platform unit. This design allows for flexible testing across various automotive systems and facilitates the integration of additional components, enabling the testing platform to adapt to different research needs. To effectively utilize this testing platform, we developed custom fuzz testing software that implements our adaptive fuzz testing approach. The software operates in two distinct phases:
1. Initial fuzz testing phase: The software generates various malformed CAN messages to test the ECU’s resilience to unexpected inputs.
2. Adaptive fuzz testing phase: Real-time analysis of ECU responses, including error codes, unexpected behaviors, and missing acknowledgment information, guides the optimization of subsequent fuzz testing iterations to more effectively discover vulnerabilities.
Incorporating dynamic ECU responses into the fuzz testing process enables the identification of vulnerabilities that traditional fuzz testing techniques may overlook. By adjusting the communication protocols used during the fuzz testing process, our approach can be generalized to other types of vehicle networks, ensuring a comprehensive method for identifying potential security vulnerabilities in automotive systems.
2.1 Fuzz Testing Process
The adaptive fuzz testing process includes several stages:
• Initialization of fuzz testing: Setting up the fuzz testing environment, including fuzz testing tools, target ECU, and communication interfaces.
• Test case generation: Creating various test cases to trigger potential vulnerabilities within the ECU.
• Test case injection: Injecting test cases into the ECU through appropriate communication channels (e.g., CAN bus).
• Monitoring ECU responses: Capturing and monitoring the ECU’s outputs, behaviors, and any error messages or anomalies.
• Analyzing ECU responses: Analyzing the responses to determine whether the ECU’s behavior aligns with expectations or exhibits any abnormal behavior.
• Vulnerability discovery? : Determining whether vulnerabilities have been discovered and reporting them for further investigation and remediation.
• Reporting vulnerabilities: Generating detailed reports on discovered vulnerabilities, including their potential impacts.
• Optimizing fuzz testing inputs: Refining fuzz testing inputs based on test results to enhance the effectiveness of the testing process.
• Iterating the fuzz testing process: Repeating the fuzz testing cycle until satisfactory testing outcomes are achieved.
2.2 Real-time ECU Response Analysis and Fuzz Testing Adaptation
This process includes real-time ECU response analysis, capturing error codes, unexpected behaviors, and missing acknowledgment information generated by fuzz testing inputs. Key features include:
• Dynamic analysis dashboard: Displaying real-time ECU response data.
• Adaptive mechanism: Demonstrating how the fuzz testing software dynamically adjusts strategies based on ECU behavior, optimizing test cases to effectively discover vulnerabilities.
2.3 Examples of Discovered Vulnerabilities
The discovered vulnerabilities illustrate their potential impact on vehicle safety and highlight the advantages of our approach over traditional fuzz testing techniques. To demonstrate the effectiveness of our method, we summarize key vulnerabilities identified using the ARE – GF framework. Table 1 outlines these significant findings, showcasing the severity and potential impact of each vulnerability. These examples emphasize the importance of our adaptive fuzz testing approach in revealing critical security flaws that could jeopardize vehicle safety and functionality.
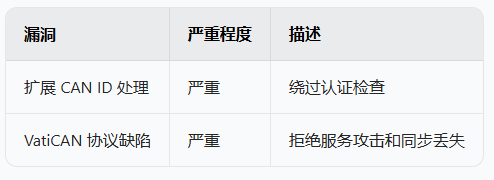
Table 1. Vulnerabilities discovered using (ARE-GF)
3. Conclusion and Future Work
This paper presents a novel approach to adaptive fuzz testing of automotive ECUs using a modular physical testing platform. By incorporating dynamic ECU responses into the fuzz testing process, this method enables more targeted and efficient vulnerability discovery, contributing to the development of secure and resilient automotive systems. The design of the modular testing platform allows for flexible testing across various automotive systems and can be easily scaled to meet future research needs. Future work will explore the integration of additional communication protocols and further automation of the fuzz testing process, enhancing the scalability and robustness of our approach. This will enable our framework to address a broader range of vulnerabilities and adapt to emerging threats in the automotive cybersecurity domain.
This article was translated by Doubao Software; please refer to the original text for any inaccuracies. Download by scanning the QR code:

 Previous Highlights
Previous Highlights







