Data Analysis of Single Wire Probes Using Matlab for Hanghua CTA04 Hot-Wire Anemometer
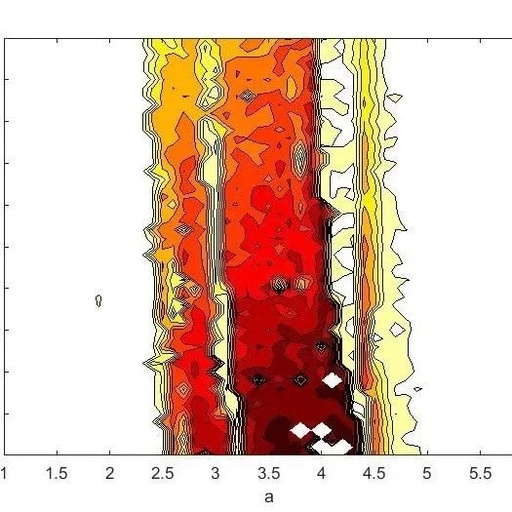
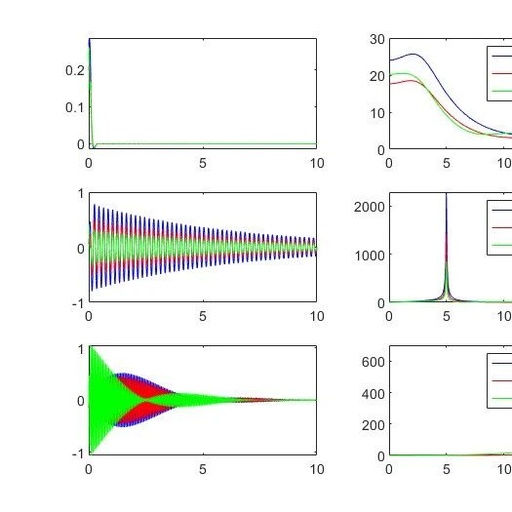
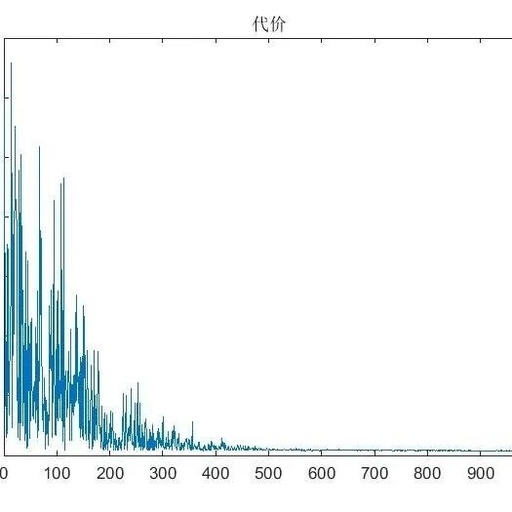
Continuing from the last article, we have obtained a collection result: an array named allData. This array has a size of [4096×180], containing all the wind speed data collected over 180 seconds. The entire process can be found on the following webpage Using Matlab to Operate Hanghua CTA04 Hot-Wire Anemometer 1: Parameter Settings Using Matlab … Read more