Follow/Star Public Account, don’t miss any updates!
I believe everyone often sees abbreviations like MCU, MPU, MMU, etc. Do you know about the MPU?
1Introduction
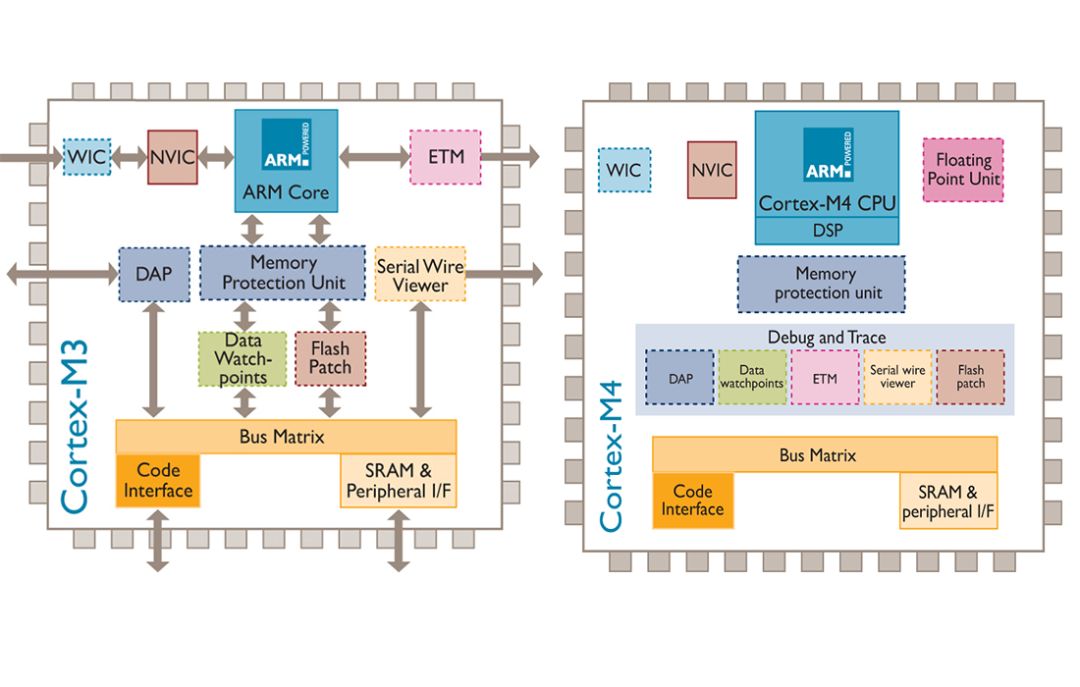
Not sure if everyone has paid attention to some aspects of the Cortex-M core, but most STM32 models have an MPU.
The MPU is an optional component of Cortex-M. For example, in the STM32F1 series, only the STM32F10X_XL series chips have this MPU memory protection unit, while other STM32F1 chips do not.
Many people might only have a basic understanding of the MPU. Today, I will write a bit about the MPU to help everyone gain a deeper understanding.
2
Understanding MPU and Its Function
MPU: Memory Protection Unit, the memory protection unit.
The MPU memory protection unit can implement protection for memory (mainly memory and peripheral registers) to make software more robust and reliable. It must be programmed according to needs before use. If the MPU is not enabled, it is equivalent to not having an MPU in the system.
The MPU has the following capabilities that can enhance system reliability:
-
Prevent user applications from corrupting data used by the operating system.
-
Prevent one task from accessing another task’s data area, thereby isolating tasks.
-
Can set critical data areas to read-only, fundamentally eliminating the possibility of corruption.
-
Detect unexpected memory accesses, such as stack overflows and array out-of-bounds.
-
Additionally, the MPU can set other access attributes for memory regions, such as whether they are bufferable, cached, etc.
3
Understanding Wild Pointers
We have briefly understood the functions of the MPU, and one important function is its protection against memory accessed by pointers. So, let’s understand pointers and wild pointers.
To review, what is a pointer? A pointer is actually an unsigned integer in memory, but its value is given a special interpretation: it represents the address of a variable or function. That’s why it is vividly called a “pointer,” as if it points to someone’s home. Before using a pointer, it must first point to a meaningful entity that is allowed to be used by the program—data and code. A “wild pointer” refers to a pointer variable whose value exceeds the legal range, causing it to point randomly. Program logic errors, array out-of-bounds, stack overflows, uninitialized pointers, improper handling of caches and buffers, chaotic conditions in multitasking environments, or even malicious corruption can all create wild pointers. If a wild pointer is used to read or modify memory, the location being accessed is unpredictable. The former leads to reading random data, while the latter can corrupt data of unknown purpose. This often results in inexplicable functional chaos in the system, and in severe cases, can cause the system to lose control and crash without warning.
A wild pointer is like “a thorn in the meat, a maggot in the sauce”: one wild pointer is enough to destroy the entire system, and it is extremely stealthy, making it difficult to identify where the wild pointer exists based on symptoms. It is even hard to determine whether the symptoms are caused by a wild pointer (as larger programs may have many other bugs that can lead to the same symptoms). For typical microcontroller systems, there is no way to prevent the damage caused by wild pointers; it completely relies on the programmer’s quality and self-discipline. But even the wisest can make mistakes. Especially when the program scale becomes large, complexity rises exponentially, and it becomes tangled and unclear. Even cautious individuals like Zhuge Liang or geniuses like Bill Gates cannot guarantee that there are no oversights.
— From the CM3 kernel translation author
4
Further Understanding of MPU
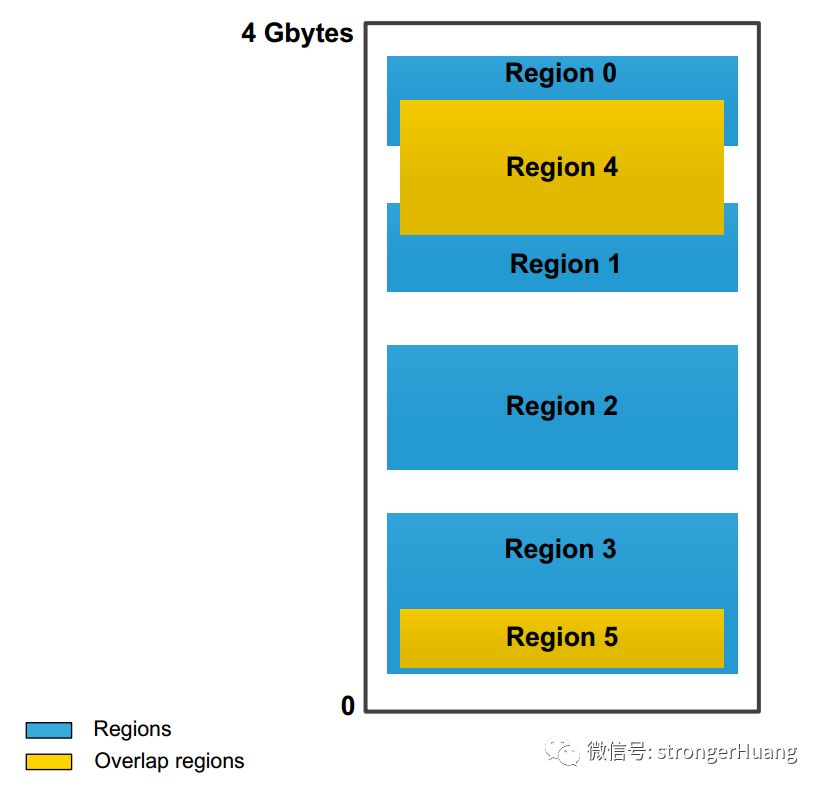
When the MPU performs its functions, it does so in units called “regions.”A region is actually a segment of contiguous addresses, but their positions and ranges must meet certain constraints (alignment, minimum capacity, etc.).
The CM3 MPU supports a total of 8 regions and allows each region to be further divided into smaller “subregions.” Additionally, a “background region” (i.e., the entire address space when the MPU is not active) can be enabled, but it can only be accessed by privileged levels. After enabling the MPU, access to address ranges outside the defined regions is prohibited, as is access to unauthorized regions. Otherwise, it will be treated as an “access violation,” triggering a MemManage fault.
The regions defined by the MPU can overlap. If a block of memory falls within multiple regions, the access attributes and permissions will be determined by the region with the highest number. For example, if region 1 overlaps with region 4, the overlapping part will be controlled by region 4.
The MPU can protect up to 16 memory regions. If the region is at least 256 bytes, these regions can have 8 subregions. The size of subregions is always equal, and they can be enabled or disabled through the subregion number. Since the minimum region size is driven by the cache line length (32 bytes), 8 subregions of 32 bytes correspond to a size of 256 bytes.
5
MPU Learning Resources
The above just further helps everyone understand the MPU memory protection unit. For those who want to delve deeper, more related materials need to be consulted.
To learn MPU programming, it is necessary to master the related registers of the MPU. The MPU registers are relatively few, and here in the Cortex-M core technical reference manual, as well as in the STM32 application note Managing memory protection unit (MPU) in STM32 MCUs, and programming manuals, there is a discussion about MPU knowledge.

To facilitate everyone, I will briefly mention a few points.
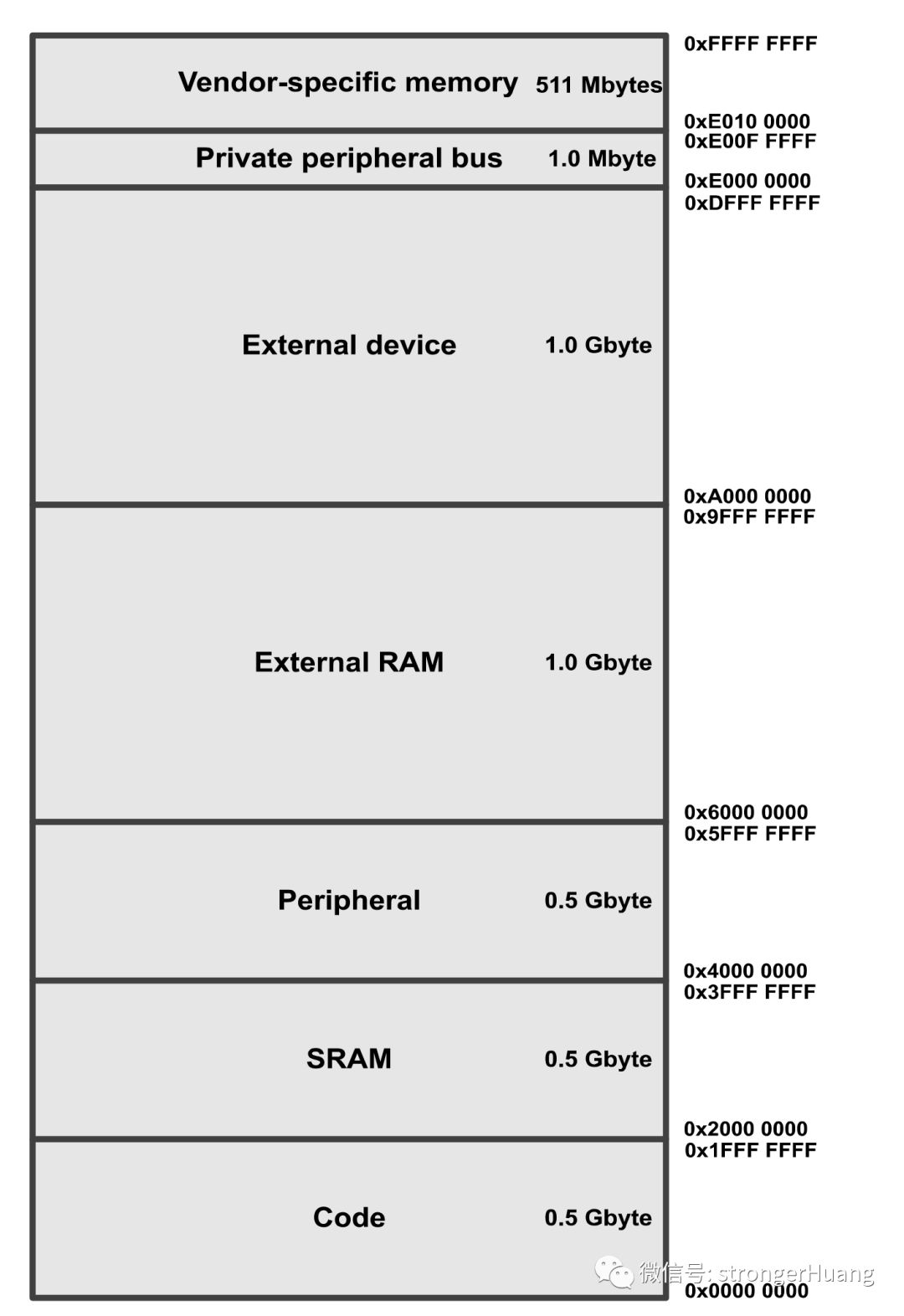
1.STM32 Memory Mapping
2.MPU Register Set
Operating the MPU is like operating ordinary STM32 peripherals, achieved by accessing its several registers. The MPU registers are shown in the table below.
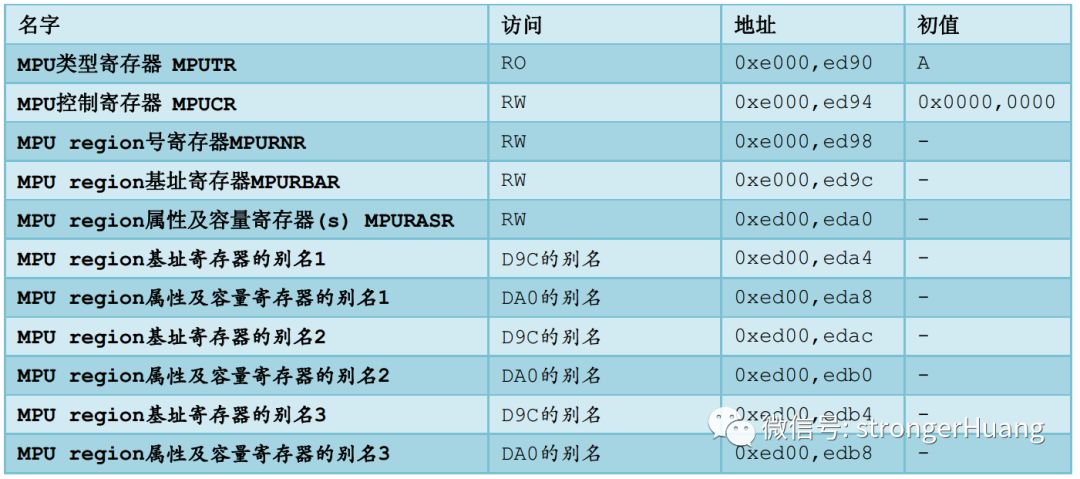
The MPU registers look quite complex, which is natural, as they have reached a level of memory management. But if we are well-prepared—having already thought about how to partition the memory, then it becomes just tedious and a test of carefulness. Typically, in systems with enabled MPU, the following regions are usually present.
Privileged program code (such as OS kernel and exception service routines)
User-level program code
Privileged program data memory, located in the code area (data_stack)
User-level program data memory, located in the code area (data_stack)
General data memory, located in other memory areas (e.g., SRAM)
System device area, accessible only by privileged levels, such as NVIC and MPU register address ranges
General peripheral area, such as UART, ADC, etc.
3.Cube HAL MPU Configuration Example
void MPU_RegionConfig(void)
{
MPU_Region_InitTypeDef MPU_InitStruct;
/* Disable MPU */
HAL_MPU_Disable();
/* Configure RAM region as Region N°0, 8kB of size and R/W region */
MPU_InitStruct.Enable = MPU_REGION_ENABLE;
MPU_InitStruct.BaseAddress = 0x20000000;
MPU_InitStruct.Size = MPU_REGION_SIZE_8KB;
MPU_InitStruct.AccessPermission = MPU_REGION_FULL_ACCESS;
MPU_InitStruct.IsBufferable = MPU_ACCESS_NOT_BUFFERABLE;
MPU_InitStruct.IsCacheable = MPU_ACCESS_CACHEABLE;
MPU_InitStruct.IsShareable = MPU_ACCESS_SHAREABLE;
MPU_InitStruct.Number = MPU_REGION_NUMBER0;
MPU_InitStruct.TypeExtField = MPU_TEX_LEVEL0;
MPU_InitStruct.SubRegionDisable = 0x00;
MPU_InitStruct.DisableExec = MPU_INSTRUCTION_ACCESS_ENABLE;
HAL_MPU_ConfigRegion(&MPU_InitStruct);
/* Configure FLASH region as REGION N°1, 1MB of size and R/W region */
MPU_InitStruct.BaseAddress = 0x08000000;
MPU_InitStruct.Size = MPU_REGION_SIZE_1MB;
MPU_InitStruct.IsShareable = MPU_ACCESS_NOT_SHAREABLE;
MPU_InitStruct.Number = MPU_REGION_NUMBER1;
HAL_MPU_ConfigRegion(&MPU_InitStruct);
/* Configure FMC region as REGION N°2, 0.5GB of size, R/W region */
MPU_InitStruct.BaseAddress = 0x60000000;
MPU_InitStruct.Size = MPU_REGION_SIZE_512MB;
MPU_InitStruct.IsShareable = MPU_ACCESS_SHAREABLE;
MPU_InitStruct.Number = MPU_REGION_NUMBER2;
HAL_MPU_ConfigRegion(&MPU_InitStruct);
/* Enable MPU */
HAL_MPU_Enable(MPU_PRIVILEGED_DEFAULT);
}For more information about the MPU, refer to the CM3 technical manual, as well as STM32 application manuals and programming manuals.
Recommended Reading:
1.Will STM32G0 Explode This Year?
2.ST’s STM32 Cube.AI Artificial Intelligence Neural Network Development Toolkit
6Conclusion
If you find this article helpful, clicking like and sharing is a great support and encouragement for me.
Scan the QR code below, follow the public account, and check the bottom menu for more exciting content!

Press and holdto recognize the QR code in the imageto follow