Hello everyone, I am Pi Zi Heng, a genuine tech enthusiast. Today, I will introduce the ARM Cortex-M functional modules, focusing on three processors with security features.
The ARM Cortex-M processor family has evolved over 8 generations by 2020. In addition to the previously discussed CM0/CM0+, CM1, CM3, CM4, and CM7 in the article “Differences in Cortex-M Functional Modules,” we also have the security-focused CM23, CM33, and CM35P.
1. Cortex-M Security Features
In recent years, the Internet of Things (IoT) has become a hot topic among embedded system developers. When discussing IoT, security is a major concern for everyone. Embedded system products require better solutions to ensure system security. In light of this, ARM has released the new ARMv8-M architecture, along with three processors based on this architecture: ARM Cortex-M23, CM33, and CM35P, which introduce the following security features:
1.1 TrustZone
The ARMv8-M architecture includes a security extension called TrustZone, which is a security encryption technology that originated in 2004 and gained prominence in the Cortex-A series processors with the rise of mobile applications. However, until the emergence of Cortex-M23 and CM33, this feature was not available in the more power-efficient Cortex-M processors used in the IoT embedded domain. TrustZone introduces an orthogonal division of secure and non-secure states, allowing non-secure state software to only access non-secure state memory and peripherals, while secure software can access all resources in both states. The TrustZone security mechanism can prevent hackers from taking control of the entire device, limiting the impact of attacks, and also enabling remote system recovery. Additionally, the ARMv8-M architecture introduces stack boundary checks and enhanced MPU designs to encourage the adoption of extra security measures.
1.2 Anti-tampering
Physical attacks can be categorized into invasive and non-invasive attacks. Invasive attacks require dismantling the chip package and exploiting vulnerabilities at the chip level, while non-invasive attacks, such as Side-Channel Attacks (SCA), detect information leaked from the chip, like power consumption or electromagnetic radiation during password operations, while being in close proximity to the chip. The targets of these attacks are generally to implant malicious software into devices or obtain sensitive internal information. The newly launched Cortex-M35P is the first processor in the Cortex-M product line to have anti-tampering and physical attack defense capabilities. The Cortex-M35P utilizes anti-tampering technology similar to that of SecurCore processors like SC000 and SC300, helping embedded security developers prevent physical tampering and achieve higher levels of security certification.
2. Differences in Cortex-M Functional Modules
Since CM23 is an upgrade of CM0/CM0+, and CM33 is an upgrade of CM3/CM4, we will specifically compare the original and upgraded cores.
2.1 CM0+ vs CM23
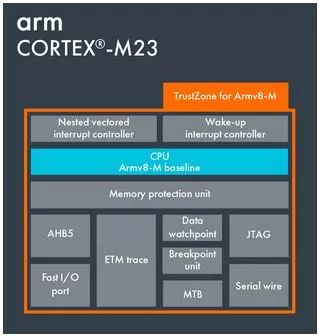
So what improvements does CM23 bring?
ARMv8-M Baseline CPU Core: This core was launched by ARM in 2016. It has introduced a 32-bit hardware divider compared to ARMv6-M.
NVIC Nested Vector Interrupt Controller: Supports up to 240 external interrupts while maintaining 4 levels of preemption priority (2 bits).
AHB5 Bus: A 32-bit high-performance system bus according to the AMBA-5 standard responsible for all Flash and SRAM instruction and data access.
MPU Memory Protection Unit: Can divide memory into 16*8 regions at most.
Debug Module: Maintains a maximum of 4 hardware breakpoints, with data monitoring points (Watchpoints) increased to 4.
ETM Trace Unit: Provides real-time instruction and data tracing.
Systick Timer: The number of timers has increased to 2.
So what has CM23 added?
TrustZone Software Security Feature: TrustZone introduces orthogonal division between secure and non-secure states, allowing non-secure state software to only access non-secure state memory and peripherals, while secure software can access all resources in both states.
2.2 CM4 vs CM33

After comparing CM0+ and CM23, let’s see where CM33 has enhanced over CM4:
So what improvements does CM33 bring?
ARMv8-M Mainline CPU Core: This core was launched by ARM in 2016. It has removed instruction branch prediction compared to ARMv7E-M.
NVIC Nested Vector Interrupt Controller: Supports up to 480 external interrupts while maintaining 8-256 levels of priority (8 bits).
2x AHB5 Bus: Two AHB5 buses, where the AHB-P peripheral interface completes the original system bus function, and the AHB-S slave interface is responsible for external bus controller functions (like DMA).
MPU Memory Protection Unit: Can divide memory into 16*8 regions at most.
Systick Timer: The number of timers has increased to 2.
So what has CM33 added?
TrustZone Software Security Feature: TrustZone introduces orthogonal division between secure and non-secure states, allowing non-secure state software to only access non-secure state memory and peripherals, while secure software can access all resources in both states.
2.3 CM33 vs CM35P
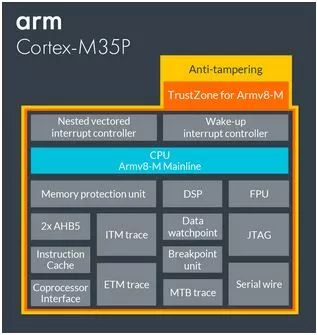
After comparing CM33 and CM4, let’s see where CM35P has enhanced over CM33:
So what improvements does CM35P bring?
Well, CM35P does not improve any existing modules compared to CM33.
So what has CM35P added?
I-Cache Buffer: This is what we commonly understand as L1 Cache, with a cache size of 2-16KB.
Anti-tampering Physical Security Feature: Designed to resist various physical attacks, it can assist developers in defending against physical tampering attacks through embedded security mechanisms, allowing products to achieve higher levels of security certification.