This article provides a preliminary understanding of the field of information security.
1. Briefly describe security attacks, security mechanisms, and security services.
-
Security attack: Any act that jeopardizes the security of an information system.
-
Security mechanism: A process used to detect, prevent attacks, or recover from an attack state to a normal state.
-
Security service (security attributes): A process that enhances security and counters security attacks using one or more security mechanisms.
2. Several attributes and definitions of security services (security attributes)
-
Authentication: Ensuring that each entity is who they claim to be.
-
Access control: Preventing unauthorized use of resources.
-
Data confidentiality: Protecting data from unauthorized disclosure.
-
Data integrity: Protecting data from unauthorized modification.
-
Non-repudiation/authenticity: Protecting against denial attacks from any party in communication.
-
Availability: Ensuring that resources are available to authorized parties when needed.
3. Understanding several typical security mechanisms
A single mechanism cannot provide complete security services, but encryption (cryptography) is a primary technology employed.
-
Specific security mechanisms:
Encryption, digital signatures, access control, data integrity, authentication exchange, traffic padding, routing control, notarization.
-
General security mechanisms:
Trusted functions, security labels, event detection, security audit trails, security recovery.
4. What security attributes are compromised in security attacks
-
Eavesdropping/disclosure – attacks confidentiality.
-
Forgery – attacks authenticity/non-repudiation.
-
Replay – attacks authentication and authenticity.
-
Modification – attacks integrity.
-
Interruption – attacks availability (narrowly: damaging hardware, denial of service DOS).
5. The difference between active and passive attacks
-
Passive attacks:
Includes eavesdropping and traffic analysis, without modifying the data.
Mainly attacks confidentiality.
Hard to detect.
Preventable – encryption, traffic padding.
-
Active attacks:
Includes modification of data streams and system states, creating false information.
Mainly attacks authenticity, non-repudiation, integrity, and availability.
Hard to prevent.
Detectable – digital signatures, HASH, intrusion detection, etc.
6. The five elements of a cryptographic system
-
Plaintext (Message)
-
Ciphertext
-
Key
-
Encryption algorithm (encrypt)
-
Decryption algorithm (decrypt)
7. Three classifications of cryptographic systems
-
Stream cipher/sequence cipher: Processes input and output in bits or characters.
-
Block cipher: Processes input and output in blocks.
-
Hash function – keyless.
-
Secret (symmetric/traditional/single-key) cipher – one key.
-
Public key (asymmetric/two-key) cipher – two keys (public and private).
-
Restricted algorithm: Confidential algorithm – classical cipher.
-
Key-based algorithm: Confidential key – modern cipher.
-
Based on the content of confidentiality.
-
Based on the number of keys.
-
Based on plaintext encryption processing methods.
8. Advantages and disadvantages of traditional and public key cryptography
-
Advantages of traditional cryptography: Fast encryption and decryption speed.
-
Disadvantages of traditional cryptography: Difficult to distribute and manage keys, challenging to implement digital signatures.
-
Advantages of public key cryptography: Easy to distribute and manage keys, easy to implement digital signatures.
-
Disadvantages of public key cryptography: Difficult to generate keys, slow encryption and decryption speed.
9. Characteristics of classical and modern encryption
-
Classical encryption: The security of data relies on the secrecy of the algorithm.
-
Modern encryption: The security of data relies on the secrecy of the key rather than the secrecy of the algorithm.
10. Three methods of cryptanalysis and their characteristics
-
Brute-force attack (trying all keys until the correct plaintext is found):
Theoretically can break any cipher system, on average, trying half of the key space can succeed.
-
Statistical analysis attack (comparing and analyzing the statistical characteristics of ciphertext):
Can break most classical ciphers.
-
Mathematical analysis attack (breaking ciphers based on mathematical theory):
The primary method for attacking public key cryptography.
11. Unconditional security and computational security
-
Unconditional security: Absolute security, a cipher that cannot be broken by any computational resources, only Shannon’s one-time pad meets this condition.
-
One-time pad characteristics: Uses a random key that is the same length as the plaintext, and does not repeat; plaintext-ciphertext statistics are independent; key generation and distribution are difficult.
-
Computational security: The cost of breaking the cipher exceeds the value of the encrypted information; the time to break the cipher exceeds the validity period of the information (M or K).
12. Definitions of substitution and transposition
-
Substitution: Plaintext is replaced by other letters, numbers, or symbols; plaintext is treated as a bit stream, replacing the plaintext bit stream with the ciphertext bit stream.
-
Transposition: The actual letters used are not changed, but the order of the letters is rearranged to hide the information.

13. Single-letter substitution (single table substitution, multiple table substitution) and multi-letter substitution
-
Single table substitution
One plaintext letter corresponds to one ciphertext letter.
-
Multiple table substitution
One plaintext letter corresponds to multiple ciphertext letters.
-
Single-letter substitution
Each plaintext letter is independently mapped to a ciphertext letter.
-
Multi-letter substitution
Letter mapping is done in groups, depending on their contextual position.
14. The formula for the general Caesar cipher (single-letter single-table substitution)
Caesar cipher formula:
C = E(m) = (m + k) mod 26
m = D(C) = (C – k) mod 26
K = 0~25 (taking 0 is meaningless) (the key is a number)
By exhausting 25 searches, the general Caesar cipher can be broken.
15. Statistical analysis attack of transposition ciphers (single-letter single-table)
Instead of shifting the alphabet, the alphabet is randomly scrambled, with each plaintext letter matching a random ciphertext letter.
Key: The correspondence between the plaintext alphabet and the ciphertext alphabet.
Since not all letters in human language are used with equal probability, statistical (frequency) analysis can break it.
16. The formula, key length, key space, and breaking methods of the Vigenere cipher (the most famous multi-table substitution cipher) and the one-time pad idea of the Vernam cipher (stream cipher)
-
Vigenere cipher
Cycles through 26 Caesar cipher keys, with each key repeating after use.
Multiple ciphertext tables smooth the frequency distribution, making cryptanalysis more difficult.
Keyword repetition makes the key the same length as the plaintext.
Formula: Ci = (Pi + K[i mod m]) mod 26 Ki=a~z
Key: The key consists of repeated keywords, m is the length of the keyword, and the key space is 26^m.
Repeating ciphertext exposes the key cycle; if the key length is short, exhaustive attacks are possible; if the key length is long,
assuming the keyword length is m, then through m times single-letter frequency analysis, m keyword letters can be obtained.
-
Vernam cipher
Stream cipher: Based on bits rather than letters.
Ci=pi⊕ki
pi=Ci⊕ki
Security relies on the randomness of the key. (Personal understanding:) Although the computational principles are different, the effect can be seen as a transposition cipher with a key length equal to the plaintext length.
-
One-time pad
The key is the same length as the plaintext and never repeats.
Plaintext and ciphertext statistics are independent.
Unconditional security (never broken).
Key generation and distribution are difficult, only used by the military.
17. Formation of the Playfair matrix (multi-letter single-table substitution) and its encryption algorithm
Example:

Encryption algorithm rules:
1. Start with the first letter, grouping every two letters; if there is a repeated group, fill in a letter between them, then take the second letter of the repeated letter as the first letter to continue step 1 until the plaintext ends.
For example: “balloon” becomes “ba lx lo on”.
2. If the double letters are in the same row, replace each letter with the letter to the right of it. (Wrap around to the start of the row).
3. If the double letters are in the same column, replace each letter with the letter below it. (Wrap around to the start of the column).
4. Otherwise, replace each letter with the letter at the intersection of the same row and different column.
Decryption: If in the same row, the operation is opposite to encryption; otherwise, it is the same as encryption.
Similarly, one can compare the frequency statistics of the 26 letters; here, it only requires statistics of 26X25=650 pairs of double-letter combinations.
18. Transposition ciphers (fence ciphers, column transposition ciphers, multi-step transposition, product ciphers, rotor machines) note that the rotor machine rotates one notch for each letter input.
-
Fence cipher
Write the plaintext letters diagonally, then read out the ciphertext letters row by row.
Example:

-
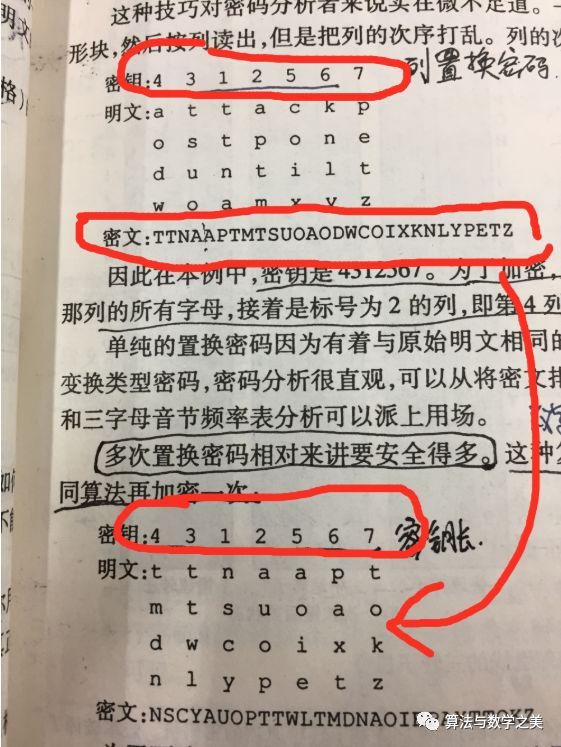
Column transposition cipher
The plaintext is written in a rectangular manner, but read out column by column; the key is the length of the rectangle and the order of reading columns.
Example:

-
Multi-step transposition cipher
Multiple column transposition operations make reconstruction difficult.
Example:
-
Product cipher
Due to the statistical characteristics of language, merely using substitution or transposition is insufficient.
Using ciphers consecutively makes the algorithm more secure: two substitutions yield a more complex substitution cipher, two transpositions yield a more complex transposition cipher, one substitution plus one transposition yields a significantly more secure cipher.
This is a bridge from classical ciphers to modern ciphers.
-
Rotor machine
Each rotor corresponds to a substitution cipher;
Each rotor produces a multi-table substitution cipher corresponding to 26 ciphertext tables (Vigenere cipher);
After each key press, the rotor rotates one notch;
The output of each rotor is the input of the next rotor;
After each rotor completes a cycle, the adjacent next rotor rotates one notch.
(A 3-rotor rotor machine produces 26^3 ciphertext tables).
19. Some misconceptions about public key cryptography
-
Public key cryptography is more secure than symmetric cryptography.
-
The emergence of public key cryptography has made symmetric cryptography obsolete.
-
Compared to the cumbersome key distribution of symmetric cryptography using KDC, public key cryptography makes key distribution easy.
20. Requirements for public key cryptography
-
Information encrypted with the public key can be decrypted with the private key (basic condition) D(E(M,PU),PR)=M.
-
Given the encryption key, deriving the decryption key is computationally infeasible (security condition).
-
When the relevant encryption key is known, performing the corresponding encryption operation is fast and efficient (engineering usage condition).
-
The order of encryption can be interchanged (optional condition) D(E(M,PU),PR)=D(E(M,PR),PU)=M.
21. Comparison of symmetric and public key cryptographyAnalysis
-
Public key cryptography
-
Uses two keys (public key and private key).
-
Public key PU does not leak private key PR.
-
Due to asymmetric communication, the person encrypting the information cannot decrypt it.
-
Based on mathematical functions rather than substitution and transposition.
-
Symmetric key (secret key):
-
Uses one key, shared by both parties.
-
Key leakage compromises the security of communication.
-
Due to symmetric communication, both parties are equal, thus cannot prevent the sender from denying sending, nor can prevent the receiver from forging information and claiming it was sent by the sender.
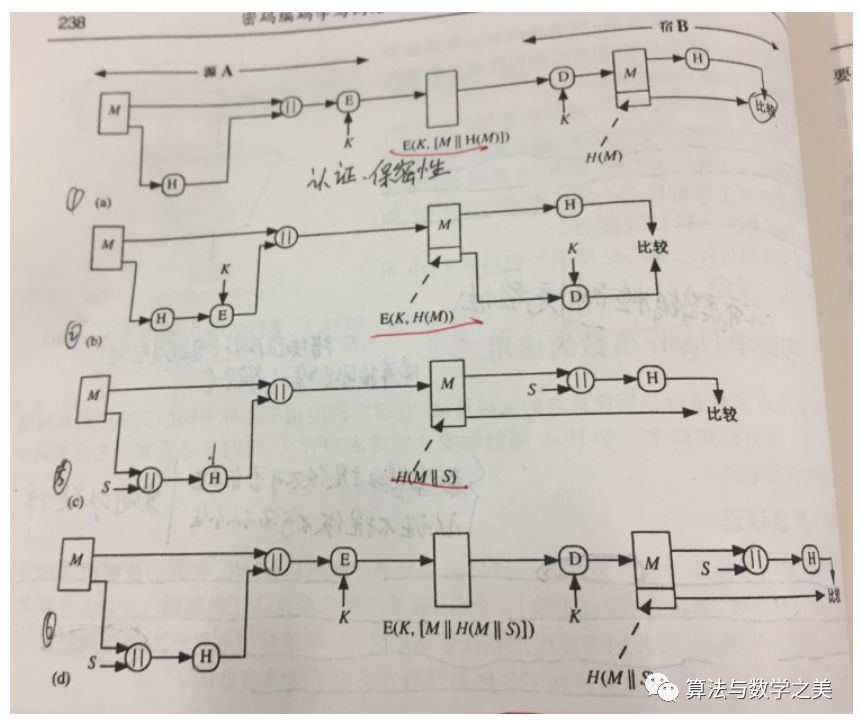
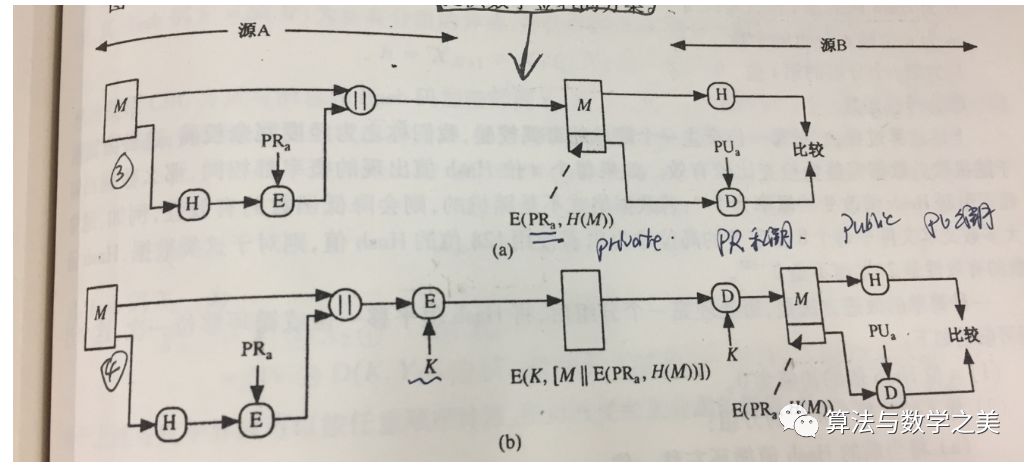
22. Several diagrams of public key cryptography and related security attributes
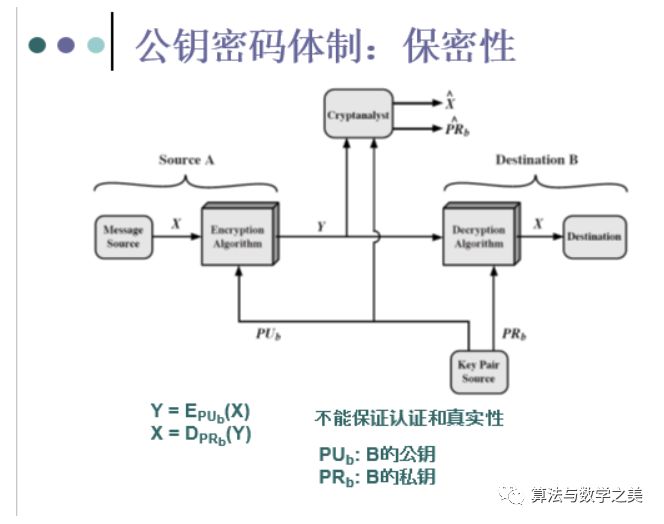
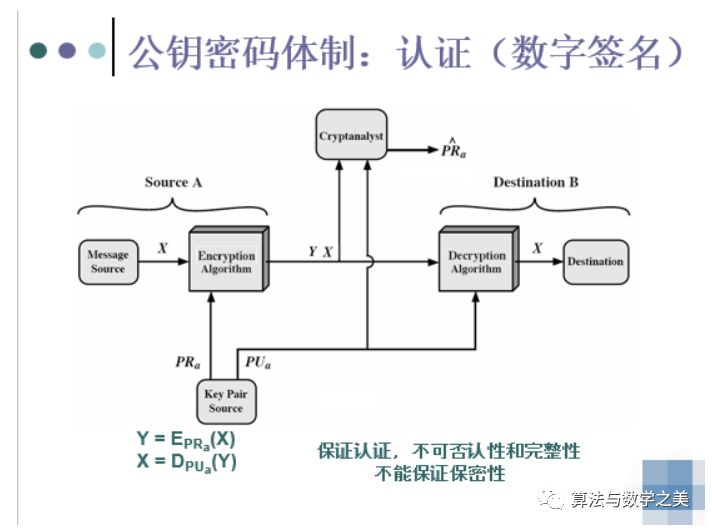
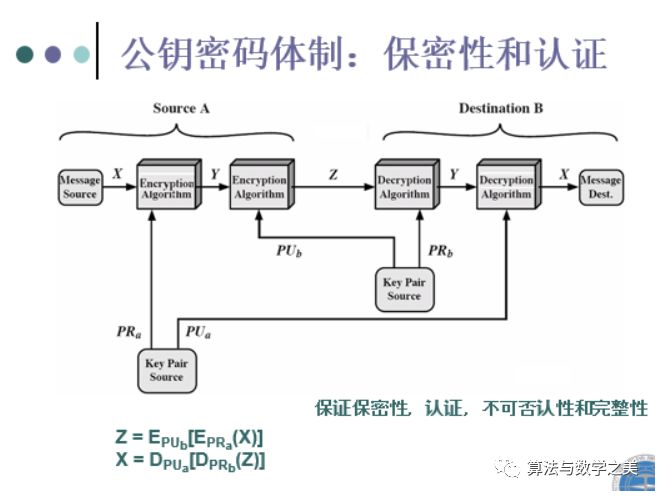
Encryption and decryption – confidentiality. Digital signatures – authentication, integrity, and non-repudiation. Key exchange – providing session keys.
23. One-way functions and trapdoor one-way functions
-
One-way function: Each function value has a unique inverse, and computing the function value is easy, but finding the inverse is infeasible.
-
Trapdoor one-way function: A function where computing the function value is easy, and calculating the inverse is infeasible without some additional information, but with that additional information, it can be computed in polynomial time.
24. Public key cryptography analysis
-
Exhaustive attack against PR.
-
Mathematical analysis attack: Deriving PR from PU.
-
Exhaustive message attack.
25. Definition of hash functions and six basic usage modes
-
The hash function H takes a data block M of variable length as input and produces a fixed-length hash value h=H(M).
26. Strong collision resistance, weak collision resistance
-
One-wayness: Given h, finding x such that H(x)=h is infeasible.
-
Weak collision resistance: Given x, finding y such that H(x)=H(y) is infeasible.
-
Strong collision resistance: Finding any x, y such that H(x)=H(y) is infeasible.
27. General structure of hash functions (iterative compression functions)
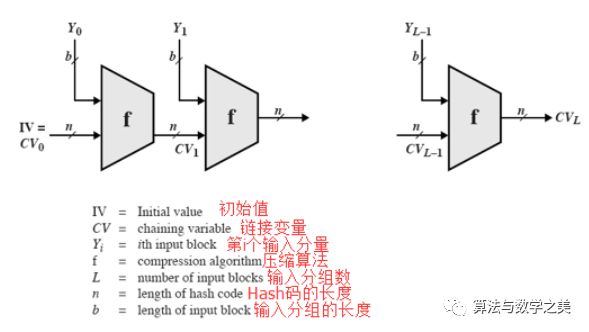
If each f is collision-resistant, then the hash result is also collision-resistant.
28. Attributes and definitions included in digital signatures
Attributes of signatures:
-
Prevents denial by the sender, including signature content and time (non-repudiation).
-
Only the sender can create the signature and the signed content (authenticity, integrity).
-
Can be verified by a third party to resolve disputes (arbitrability).
Definition: A digital signature is an authentication mechanism, a code attached by the message creator to the message. It can guarantee the authenticity/non-repudiation and integrity of the message source.
Attributes of digital signatures:
-
Must depend on the signed information – ensuring integrity.
-
Must use unique information of the sender (PR) – preventing forgery and denial (authenticity/non-repudiation).
-
Relatively easy to produce.
-
Relatively easy to verify (PU).
-
Computationally infeasible to forge (for a given digital signature, forge a new message corresponding to it; for a given message, forge a digital signature corresponding to it).
-
Storing a copy of the digital signature is feasible.
29. The role of hash functions in digital signatures
-
Reduces the length of digital signatures and communications.
-
Maintains the correspondence between messages and signatures to prevent forgery (authenticity, integrity).
30. Arbitration of digital signatures

31. Password storage mechanism
Principle: Hash function, given h (password), it is difficult to reverse to obtain the password Process: User passwords are stored as hash values h (password), when the user inputs the password, the system calculates the hash value of the password and compares it with the stored hash value in the password file; the original password is not stored on the disk.
32. Dictionary attack on passwords Commonly known as guessing passwords.
33. Three purposes of introducing salt
-
Prevents the occurrence of identical passwords in the password file.
-
Effectively increases password length.
-
Prevents hardware implementation of DES.
34. Intrusion detection systems
-
Can timely identify intruders.
-
An effective intrusion detection system can prevent intrusions.
-
Intrusion detection can collect intrusion information to enhance intrusion prevention functions.
35. Pay attention to the behavior profile of intruders and authorized users in that diagram
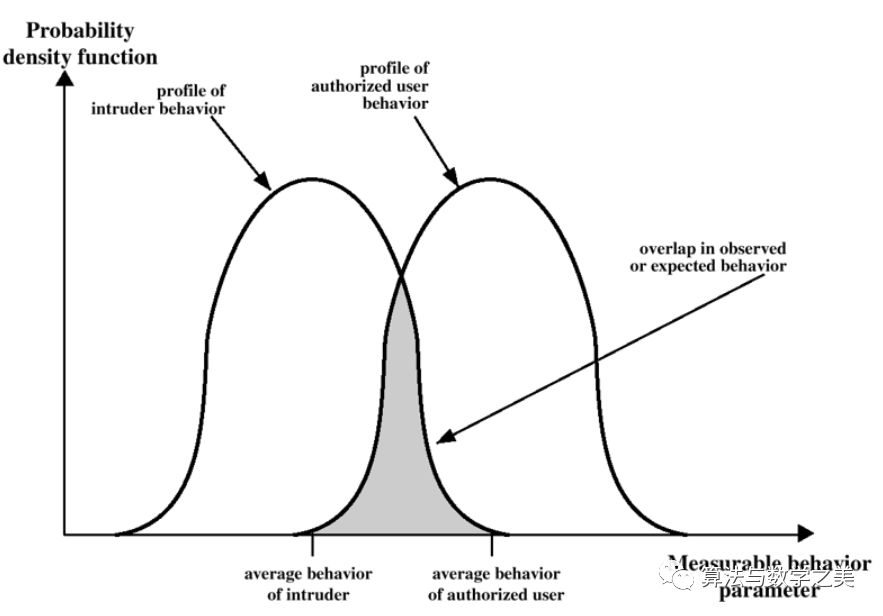
36. Understand false positives and false negatives, which situations cause false positives, which situations cause false negatives, and intrusion detection technologies
-
Relaxing the definition of intrusion will lead to false positives – identifying authorized users as intruders.
-
Strictly defining intrusion will lead to false negatives – identifying intruders as authorized users.
Intrusion detection technologies
-
Misuse detection: Defines existing intrusion patterns, difficult to discover new intrusions.
-
Anomaly detection: Defines normal usage profiles, judging the deviation of intrusion behavior from normal behavior.
-
Can detect unknown intrusions.
37. Challenge-response authentication mechanism
-
3.0
On the basis of protocol 2.0, A adds a secret password to prove that they are A, C can perform replay attacks.
-
3.1
Based on 3.0, the secret password is encrypted, but it doesn’t help…
-
Protocol 1.0
A directly sends plaintext to B, C can directly impersonate A to send messages to B.
-
Protocol 2.0
A sends their IP address and plaintext to B, C can create a data packet to spoof A through IP spoofing.
-
Protocols 3.0 and 3.1
-
Protocol 4.0
B sends a random number N to A, A encrypts it with the shared symmetric key, if B can decrypt it to get N, then A is A.
-
Protocol 5.0
On the basis of 4.0, replace the symmetric cipher with A’s private key encryption, B decrypts with A’s public key.
38. Key distribution, authentication services, certificate verification, cross-certification, certificate revocation, and PKI under the X.509 service system
-
Key distribution: Ensures the authenticity and integrity of PU in the public key database PKDB through digital signatures; certificates are the digital signature carrier of the user’s identifier and their public key PU by a trusted third party; CA is the trusted third-party entity that signs PU.
-
Authentication services: Define the framework of services (store public key certificates in directories, signed by CA with its private key PR); use public key algorithms and digital signature technology; public key certificates are trusted carriers of public key PU, enabling secure distribution of public keys.
-
Certificate verification: Users can obtain the CA’s public key from CA’s certificate, which is then used to verify the security of other users’ public keys in their certificates; CA’s certificate can be self-signed or signed by its parent CA.
-
Cross-certification:

-
Certificate revocation:
Certificates have validity periods and can be revoked early (key leakage, loss of trust between user and CA, destruction of CA’s certificate), maintaining a certificate revocation list (CRL) through digital signatures; users periodically update the CRL and check the certificate names in the CA’s CRL list before using certificates, for speed reasons, the local machine caches the CRL list.
-
PKI (public key infrastructure)
Definition: The PKI system is a complete system composed of hardware, software, people, policies, and corresponding processes for creating, managing, storing, distributing, and revoking digital certificates (PU).
Goal: To distribute public keys PU. Trust is conveyed through certificates.
Elements: End entities, Certification Authorities (CA), Registration Authorities (RA) (optional), Certificate Revocation List (CRL) publication points (optional), Certificate repositories (certificates and CRLs).
Tasks: User registration, user initialization (generation and distribution of key pairs), authentication (generation and storage of certificates), backup and recovery of key pairs (for data encryption, backup PU and PR; for digital signatures, only PU can be backed up), automatic key pair updates, certificate revocation requests, cross-certification (mutual signing of certificates between CAs).
39. LSB algorithm, digital watermarking, link attacks against privacy
LSB (Least Significant Bit) algorithm:
-
Modifies the low-order bits indicating color in digital images to hide information; one pixel contains 24 bits of RGB color information, modifying the least significant bit (LSB) does not significantly change the quality of the image.
-
Advantages: Fast, simple.
-
Disadvantages: Hidden information may be destroyed by information processing, such as signal conversion and image compression.
Digital watermarking:
-
Adds an “invisible” copyright information (unique identifier or serial number) to digital media; digital watermarking can be extracted as evidence of unauthorized copies when needed.
-
Characteristics: Embedding or extracting copyright information does not affect the normal use of the host media.
-
Requirements: Transparency, robustness.
-
Divided into spatial domain and frequency domain techniques.
-
Similar to steganography but serves a different purpose.
Link attacks against privacy: Link attacks are a common method of obtaining private data from published data tables. The basic idea is: the attacker links the published data with external data obtained through other channels to infer private data, leading to privacy leakage.
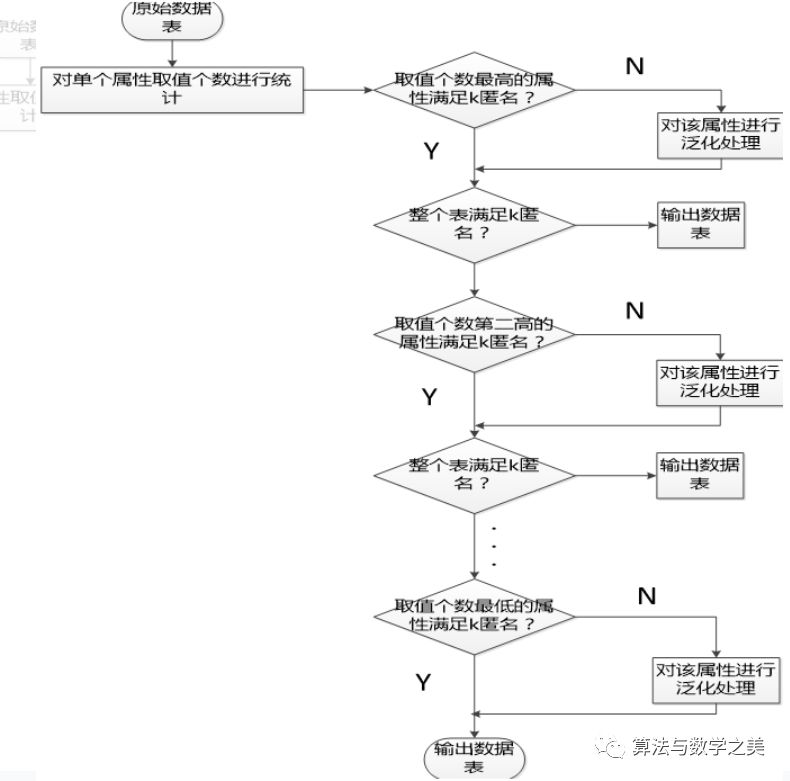
40. Familiarity with K-anonymity algorithm and generalization process
K-anonymity algorithm idea: Each calculation can only choose one attribute value to generalize, and the cardinality of the value set of this selected attribute is the largest among the remaining attributes, repeating the previous steps until all quasi-identifier attributes are selected.
41. What is access control and the purpose of access control
-
Access control definition: The subject gains different permissions to access the object based on certain control policies.
-
Purpose of access control: To provide certain security protections for subjects and objects, ensuring that unauthorized individuals do not use legitimate or sensitive information, while also ensuring that legitimate users can correctly use these resources, thus achieving secure hierarchical management.
42. The three elements of access control and implementation
Three elements:
-
Subject: The entity making the access request to the object, referred to as S, also known as the user or authorized accessor.
-
Object: The passive entity that accepts the subject’s access request, referred to as O.
-
Control policy: The set of access rules of the subject to the object, referred to as P.
Implementation of access control:
Framework:
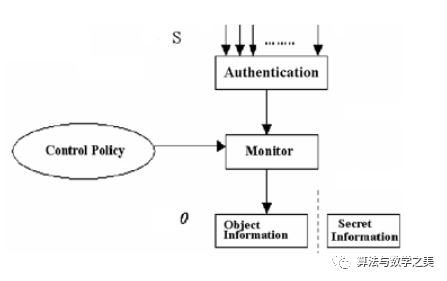
Implementation:
-
Authentication: Bi-directional authentication between subject S and object O.
-
Policy formulation and implementation: Formulation – creating users; Implementation – user behavior.
-
Audit: Auditing is an important content and complement of access control, which can record and monitor what information resources users have used, when they used them, and how they used them.
43. Definitions and differences of two types of access control (DAC, MAC)
DAC (Discretionary Access Control): Belongs to non-hierarchical multi-level security, also known as discretionary access control, allows legitimate users to access objects as users or user groups as specified by the policy while preventing unauthorized users from accessing the objects; certain users can also grant access permissions of their owned objects to other users at their discretion.
MAC (Mandatory Access Control): Belongs to hierarchical multi-level security, the system pre-assigns different security levels to subjects and objects; when implementing access control, the system first compares the security levels of the subject and object, then decides whether the subject can access the object.
Difference between DAC and MAC:
-
DAC is non-hierarchical; MAC is hierarchical.
-
DAC access permissions can be freely granted to other users, authorization is based on users; MAC access permissions are strictly enforced according to security levels, authorization is based on security levels and can only be modified by security administrators.
44. Four types of access methods
-
Downward read (rd): Allowed read operation when the subject’s security level is higher than the object’s security level.
-
Upward read (ru): Allowed read operation when the subject’s security level is lower than the object’s security level.
-
Downward write (wd): Allowed execution or write operation when the subject’s security level is higher than the object’s security level.
-
Upward write (wu): Allowed execution or write operation when the subject’s security level is lower than the object’s security level.
45. BLP model under MAC and Biba model
-
Bell-LaPadula (BLP) model: Features only allowing downward reads and upward writes, effectively preventing confidential information from leaking to lower levels. Disadvantages: Makes illegal, unauthorized modification possible.
-
Biba model: Features only allowing upward reads and downward writes, effectively protecting data integrity. Disadvantages: Ignores confidentiality.
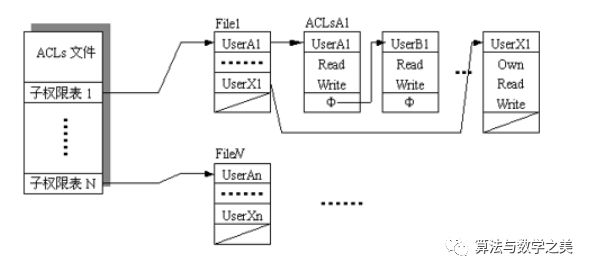
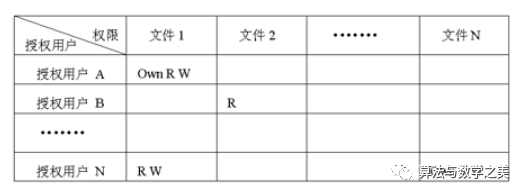
46. Access control lists and access control matrices under DAC
-
Access control list: File-centered.
-
Access control matrix: Includes a complete matrix of all subjects and objects.
47. Security label lists under MAC Set of security levels for subjects and objects.
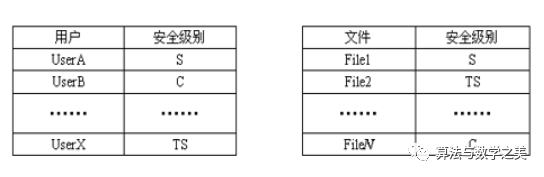
48. Difference between authorization and auditing
-
Authorization: The prerequisite for access control, the permission granted by the object to the subject. Authorization is based on a trust model (a framework for establishing and managing trust relationships, where trust is the expectation that the subject meets the object’s presumed expectations).
-
Auditing: A necessary supplement to access control, the last line of defense for ensuring system security, operating at the highest level of the system, tracking and recording system and user behavior. Auditing not only helps ensure that the system and its resources are not compromised by unauthorized users but can also prevent legitimate users from overstepping their bounds and can assist in data recovery.
49. Audit content
-
Individual functions.
-
Event reconstruction.
-
Intrusion detection.
-
Fault analysis.
∑ Edited by | Gemini
Source | CSDN

The beauty of algorithm mathematics WeChat public account welcomes submissions.
Manuscripts involving mathematics, physics, algorithms, computer science, programming, and related fields will be rewarded upon acceptance.
Submission email: [email protected]