From Julius Caesar
to Sherlock Holmes
from Nazi leader Hitler
to the father of AI, Turing…
How did the
ultimate code in the field of communication
come into being?
All of this must start from the beginning.
A Brief History of Codes
The first dictator in Roman history, the father of the Roman Empire, an undefeated general, a calendar inventor, a Latin literature scholar, and the man behind Cleopatra… In addition to these legendary deeds, Julius Caesar also had a little-known skill: cryptography.
In fact, the emperor was not the first person in history to come up with an encryption algorithm. It is said that Jiang Ziya from our dynasty invented the ancient version of a codebook called “Yinshu” three thousand years ago. In the 4th century BC, the ancient Greeks invented a scroll-type codebook called “Tianshu”; in the 5th century BC, Spartan men would wrap a belt around a wooden stick, and only a specific diameter of the “password stick” could restore the characters on the belt to plaintext. But today, we still credit cryptography to Caesar because the Caesar cipher was likely the first widely used encryption technology in military communication.
The principle of the Caesar cipher can be summed up in one word: substitution!
If you think of the letter A, you write B on paper; to write B, you replace it with C. Of course, I can also replace A with D, B with E, and so on (shifted by 3 letters).
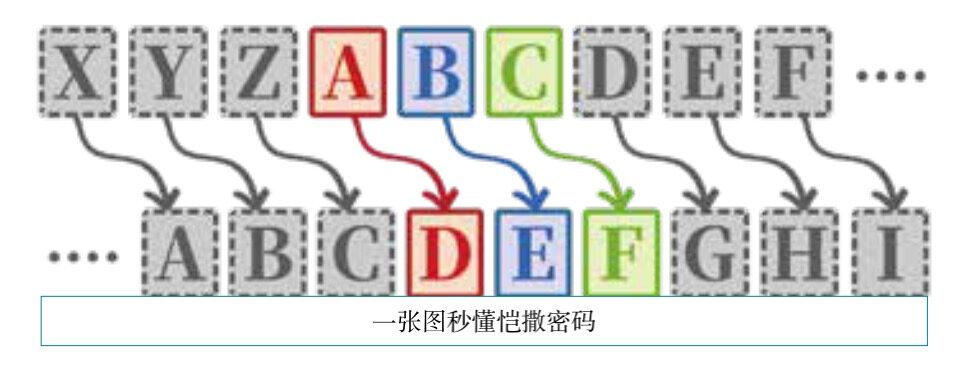
As long as both parties know the offset, they can easily encrypt and decrypt; and what outsiders see is just a pile of gibberish. Passing notes in class has a new trick! Thinking (plaintext): I love U; the teacher sees (ciphertext): L oryh X.
Today, this algorithm seems very easy to crack and lacks technical content. But on the Roman battlefield back then, this was the black technology that intimidated the onlookers!
At the height of Caesar’s dominance in Rome, even the Pope had to admit: “Render unto God what is God’s, and unto Caesar what is Caesar’s.” The so-called “what is Caesar’s” refers to the fact that the region where Jesus was (now Jerusalem, Israel) had already been conquered by Rome, and people had to pay taxes to the Roman Empire using currency stamped with Caesar’s portrait (Caesar’s).
Ironically, this military genius who was cool and proficient in cryptographic espionage died in a conspiracy, stabbed 23 times. To commemorate the emperor, people made Caesar a specimen in playing cards: the King of Diamonds.
Another thousand years later, Julius Caesar and his Roman Empire had long since vanished, while the Caesar cipher and playing cards have been carried forward by later generations.

The Dancing Little Man
The original Caesar cipher uses letters to replace letters, and all letters are replaced according to the order of the offset, greatly reducing the difficulty of cracking.
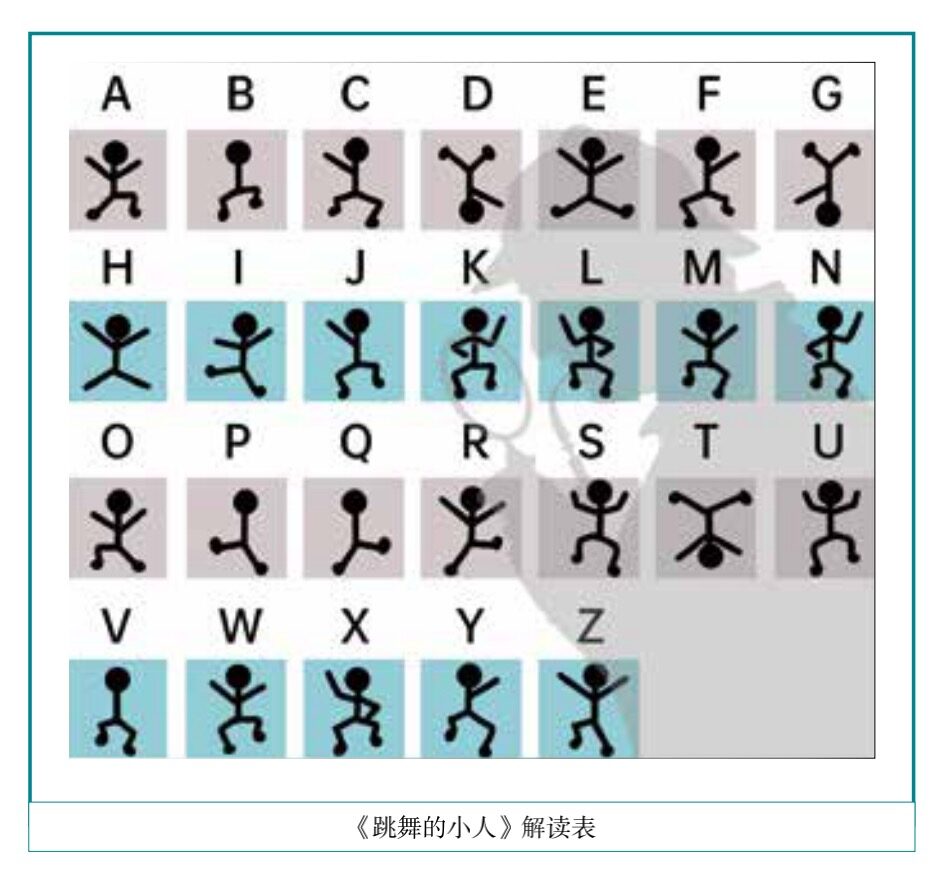
By the Victorian era, these two weaknesses were finally improved. Thus, even an ordinary gangster caught by Sherlock Holmes learned to create such a cipher:

Let’s take a look at how the legendary Holmes cracked this pictogram cipher.
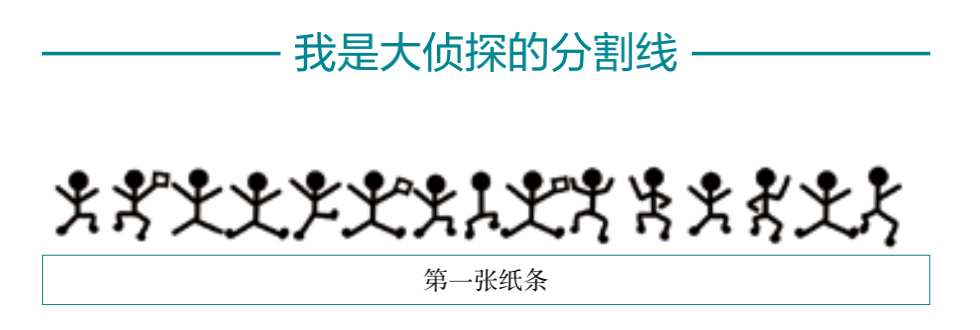
The letter E is the most common in the English alphabet. Among the 15 little men on the first note, 4 are exactly the same, so guess it is E.
Among these figures, some have flags and some do not. From the distribution of the flags, the figures with flags may be used to divide this sentence into individual words.

Now comes the most difficult question.
Because, besides E, the order of the frequency of letters in the English alphabet is not very clear. If I try every combination, it would be an endless painful task.
I can only wait for new material to arrive.
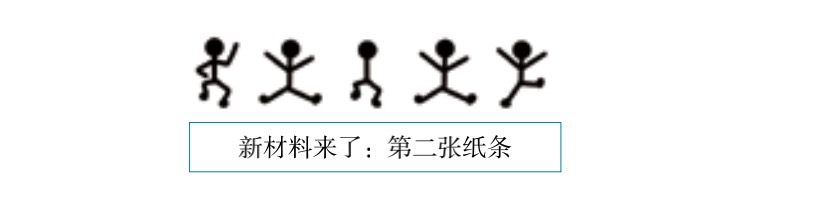
Based on a sentence that seems to have only one word, I found that the 2nd and 4th are both E.
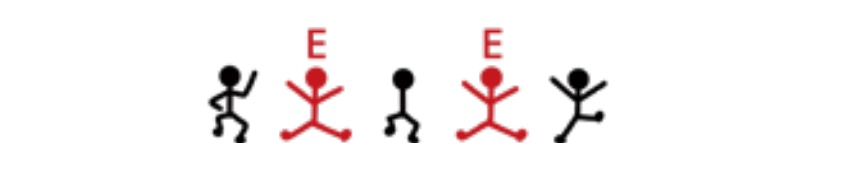
This word could be sever, lever, or never.
There is no doubt that the possibility of using the word never to respond to a request is extremely high, so the other three little men represent N, V, and R respectively.

Thus, by this reasoning, Holmes used the context to crack the code, deciphering all 52 ciphertexts in no time:
All substitution-based encryption algorithms have a fatal weakness. Any text composed of letters must conform to the laws of language, for example, the letter E is the most common in English words, while Z and X are the rarest. No matter how bizarre the substitution is, the distribution of symbols will never change. Using probability statistics + exhaustive search + basic skills of crossword puzzles, cracking any ciphertext is just a matter of time.
Just when everyone thought that the development of the Caesar cipher had reached its peak, the German Scherbius gave a major upgrade to substitution ciphers, creating the most reliable encryption system in history.
This is the nightmare that once made the Allies despair and the weapon that made Hitler rise and fall during World War II: the Enigma machine.

The New Brain of Machines
What is so amazing about the Enigma machine?
1. Machine Encryption
This is the world’s first fully automatic encryption machine, whereas encoding and decoding had previously relied on manual labor. The benefit of using a machine is not only time-saving and labor-saving but also allows for complex algorithms that are difficult to achieve manually.
2. Compound Substitution
Although the basic principle is the same as the Caesar cipher, the character substitution method of the Enigma has upgraded by more than one level: compound substitution.
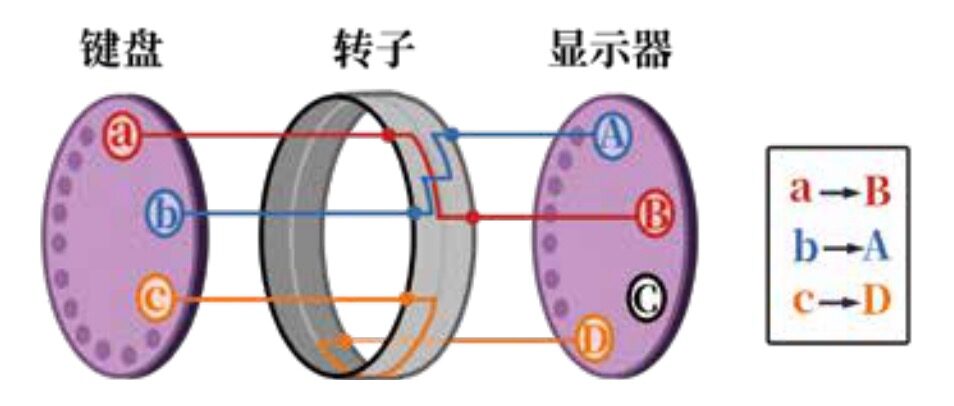
The essence of the Enigma lies in the “encoder” which changes the substitution method in real-time through the rotation of “rotors”. Each rotor has 26 settings, each representing a substitution pattern, for example:
Setting 1: Replace A with B, B with C, C with D…
Setting 2: Replace A with Z, B with Y, C with X…
Setting 3: Replace A with Q, B with G, C with D…
If you look at each setting individually, it is just the simplest Caesar substitution; but each time a letter is pressed, the rotor rotates like a revolver, automatically switching to a different substitution pattern. After inputting 26 letters, each letter uses a different substitution pattern, rendering the frequency analysis and probability statistics methods of cracking ineffective. This is the power of compound substitution.
In other words, if you press 3 A’s in a row, the ciphertext of the Caesar cipher could be BBB or CCC; no matter what A is replaced with, three identical letters encrypted will always be the same. But the ciphertext of the Enigma could be BZQ! This is something that the emperor could never achieve.
The original Enigma machine only had one rotor, and after inputting 26 letters, the encryption pattern for the next letter would cycle back to the initial pattern. In other words, the encryption pattern of compound substitution is limited and will produce repetitions. During World War II, the German army added 3 rotors to ensure that after encrypting 26 × 26 × 26 = 17,576 letters, it would take a complete cycle.
Even more extreme, the founder Scherbius came up with a new trick: making each rotor interchangeable, so the order of the 3 rotors could change the encryption pattern. For example, the encryption results of [Rotor 1 | Rotor 2 | Rotor 3] and [Rotor 3 | Rotor 2 | Rotor 1] would be completely different. This way, the encryption pattern increases by 6 times, with the total possible settings for 3 rotors reaching 26 × 26 × 26 × 6 = 105,654 combinations!

And it doesn’t stop there—Scherbius came up with a second trick: adding a “wiring board” between the keyboard and the encoder, which can temporarily swap the encryption methods of individual letters. For example, if A and B are swapped, then the ciphertext BZQ from encrypting AAA would change to CYG.
Among the 26 letters, any 6 pairs of letters can be selected for swapping. Just this swapping trick alone produces 100,391,791,500 (approximately 100 billion) variations!
So, how many encryption patterns does the Enigma really have?
Just the encoder has 105,654 different combinations, multiplied by the wiring board’s 100,391,791,500, equals:
10,586,916,764,424,000
Is that mind-boggling? This astronomical number is approximately 1 followed by 16 zeros: 1 hundred quadrillion.
If purely relying on luck to guess, even if one does not eat or drink and tests one encryption pattern per second, it would take 300 million years to try all the patterns of the Enigma. Thus, even the slightest hope of brute force cracking is extinguished.
Such a complex encryption system is as simple to decrypt as a password lock: just take another Enigma machine, set the positions of the 3 rotors to be the same as the sender’s machine, and encrypt the ciphertext again to automatically restore it to plaintext. Modern people in the 21st century can hardly imagine that in an era without integrated circuits, such exquisite designs were achieved using gears and wires; the ingenuity of the inventor is truly astonishing!
However, the invention of compound encryption was not solely the work of Scherbius; at least three inventors developed encryption machines centered around rotor encoders at that time, but their fates are lamentable.
The earliest to exit was the Dutchman Alexander Koch, who sold his patent after 8 years (in 1927) because he could not find customers; the one who invested the most was the American Edward Hebern, who invested 380,000 dollars (equivalent to 150 million RMB today) to build a factory to mass-produce encryption machines around 1920, ultimately only selling 12 units; while the most miserable was the Swede Arvid Damm, who died without ever selling his product, and no one even wanted his patent…
How can such a groundbreaking invention end up like this? The answer is simple: the market did not pay. A basic model of the Enigma costs the equivalent of 200,000 RMB today; convincing the client to spend money on this small matter of “encryption” is not easy. Of course, fundamentally, it is because customers felt it was unnecessary. Traditional encryption methods, though simple, were good enough; why waste money on “encryption”?
When the whole world deemed compound encryption too expensive and useless, only Germany, this cunning boy, purchased over 30,000 Enigma machines in 20 years, and they were military-grade high-spec models. The sales of this one product from Scherbius’s company reached at least 6 billion RMB. It is no exaggeration to say that the short-sightedness of the Western powers and the genius of Scherbius made the German Enigma stand out, becoming the strongest espionage tool on earth at that time, claiming to be “ten years ahead of the world.”
The next story, I believe everyone knows: with the backing of the “strongest encryption”, the German army swept across Europe with their devastating “Blitzkrieg”, striking unexpectedly and attacking unprepared. In the world of martial arts, speed is the ultimate defense. If one cannot crack the German intelligence and prepare defenses in advance, it would be almost impossible to counter the well-armed German armored forces.
Because the Enigma was so incredible at the time, the German army became complacent, thinking that the Allies would never crack it in their lifetime.
They were not wrong. Relying solely on human effort, it was impossible to outsmart the Enigma machine.
The only thing that could crack this machine was another machine, a more powerful machine.
– To Be Continued –

“Cats, Einstein, and Cryptography: Quantum Communication That I Can Understand”
Author: The Gods Themselves

Zhihu Popular Science HeatNo.1Work!
From Schrödinger’s Cat to Einstein’s Nightmare
From Bell’s Mathematical Principles to Bohr’s Paranormal Experiments
Funnier than meme videos, more exciting than suspense dramas!
Laughing along, quantum black technology becomes understandable!
Due to the trial of random push notifications by WeChat public accounts, you may no longer receive timely updates from the Mozi Salon. To avoid losing contact with Xiao Mo, please set “Mozi Salon” as a starred account and frequently click the “Looking” button at the bottom right of the article.
Mozi Salon is a large public welfare science forum named after the ancient Chinese sage “Mozi”, hosted by the Shanghai Institute of the University of Science and Technology of China, with co-sponsorship from the New Alumni Foundation of the University of Science and Technology of China, the Education Foundation of the University of Science and Technology of China, the Science and Technology Association of Pudong New District, the China Association for Science and Technology, and the Science and Economic Committee of Pudong New District.
Mozi is a famous thinker and scientist in ancient China, and his thoughts and achievements reflect the early budding of science in China. The establishment of the “Mozi Salon” aims to inherit and promote scientific traditions, build a society that values science, enhance citizens’ scientific literacy, and advocate and promote the spirit of science. The target audience for popular science is the general public who love science, have an exploratory spirit, and curiosity. We hope to allow the public with at least a secondary school education to understand and appreciate the most cutting-edge scientific advancements and thoughts globally.
About “Mozi Salon”