With the deep integration of cyberspace and physical space, the impact of cyber issues on reality is becoming increasingly severe. Industrial control systems, as a necessary “cornerstone” for the normal operation of society, are of paramount importance. However, the cyberspace is filled with various uncertainties that pose deadly threats to these control systems. As of December 2018, the number of industrial control system devices exposed to the internet globally had exceeded 40,000, covering various industries such as energy, transportation, education, and healthcare. Yet, the number of security incidents in industrial control systems continues to increase each year. As shown in the figure, the security incidents reported from 2010 to 2019 have been on the rise since 2015, making the protection of industrial control systems’ security an urgent matter. Below are some typical security incidents.[1].
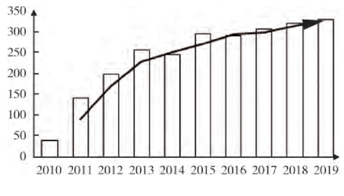
Security Incidents in Control Systems
[Example 1] Davis-Besse Nuclear Power Plant Attacked by Slammer Worm
In January 2003, the Davis-Besse Nuclear Power Plant in Ohio, USA, and related power facilities were attacked by the SQL Slammer worm virus, causing significant network congestion and resulting in slow computer processing speeds at the plant, with the power system unable to recover normal operations for several hours.
[Example 2] Stuxnet Virus Affects Multiple Countries
In 2010, the Stuxnet virus was first discovered. This worm virus specifically targets critical energy infrastructure in the real world. To date, it has affected 45,000 networks globally, with Iran being the most severely impacted country, leading to several delays in power generation at Iranian nuclear plants, and approximately 60% of personal computers in Iran were also infected with this virus. Unlike ordinary computer viruses, Stuxnet has specific targets, with greater destructive capabilities, enhanced stealth, and a more complex structure, resulting in more severe consequences.
[Example 3] Duqu Virus Attack
The Duqu virus was first discovered in October 2011. Unlike the Stuxnet virus, this type of virus does not attack the availability of systems. Instead, its primary purpose is to facilitate the theft of confidential information. Research indicates that this virus is more about lurking and collecting various information about the attack target for use during an attack.
[Example 4] Flame Virus Sweeps Middle Eastern Countries
The Flame virus was discovered in May 2012 and is a highly complex malware that has been used as a cyber weapon to attack multiple countries and conduct cyber espionage. It can steal critical information, including computer display information, system information, stored files, contact data, and audio-video files. Notably, this virus is significantly larger than ordinary viruses but is also harder to detect.
[Example 5] Polish Airlines Operating System Hacked
In June 2015, the ground operations system of Polish Airlines was hacked, leading to a system paralysis lasting 5 hours, with at least a dozen flights canceled and over 1,400 passengers stranded.
[Example 6] Ukraine’s Power System Experiences Massive Blackouts Due to Malware Attack
In December 2015, three regional power systems in Ukraine were attacked by malware, resulting in widespread blackouts, affecting over 1.4 million people in the Ivano-Frankivsk region, with the blackout lasting for more than ten hours. While the power plants were under attack, several other energy companies in Ukraine also faced targeted cyberattacks.
[Example 7] Ransomware Attacks Over 150 Countries
The ransomware was first discovered in May 2017, sweeping across over 150 countries and affecting multiple industries, including government departments, healthcare services, public transport, postal systems, communications, and automotive manufacturing. This virus primarily spreads through emails, trojans, and web exploits. When users click on these programs, their personal files are encrypted, requiring a key provided by hackers to decrypt. On May 8, 2021, the largest fuel pipeline in the USA was attacked by hackers, forcing it to shut down and affecting 45% of fuel supplies on the East Coast. The FBI confirmed that the pipeline company Colonial was infected with ransomware, where hackers typically lock down networks by encrypting data and then demand a ransom.
“2. Manifestations of Vulnerabilities in Industrial Control Systems“
Based on the topology of industrial control systems and the main sources of threats, it can be analyzed that the vulnerabilities of ICS mainly concentrate in three areas[2]: policies and regulations; platform aspects; and network aspects. These manifest in platform vulnerabilities, management vulnerabilities, and protocol vulnerabilities, requiring targeted strategies for different vulnerabilities. The vulnerabilities of industrial control systems are as follows:
1) General Network Security Architecture
Due to business and operational needs, the topology of network devices often changes. In the process of change and modification, potential security impacts are not considered. There is no targeted network structure to adapt to the relevant industrial control systems, making them vulnerable to specific attacks in some infrastructure gaps. Furthermore, with the continuous development of the internet and business demands, some infrastructures are being increasingly connected to the internet. Although these devices have strict user identity authentication, they still carry the risk of being compromised. Once breached, the consequences can be irreparable due to the widespread application of these infrastructures.
2) Immature Intrusion Detection Systems
As the internet continues to develop, the demand for external access to industrial control systems is gradually increasing. However, the relevant security measures are still not perfect. There exists some illegal traffic on the internet that can access industrial control systems, and many of these illegal traffic types pose security threats. Currently, mainstream intrusion detection systems are implemented using machine learning methods, but the existing algorithms can only learn features from previously encountered attack samples and may not effectively learn the characteristics of new or special intrusion samples, leading to incomplete security. Moreover, due to the limitations of machine learning algorithms, achieving high accuracy may result in low recall rates, leading to misjudgment of some legitimate traffic, which significantly deteriorates the user experience for infrastructure administrators. Therefore, it is essential to improve relevant intrusion detection mechanisms to prevent access from illegal traffic or establish relevant firewalls to avoid intrusion.
3) Plaintext Transmission of Relevant Messages
Currently, a considerable number of systems still transmit non-password-related messages in plaintext. Transmitting information in plaintext over transmission media is easily susceptible to eavesdropping. Although these messages cannot directly authorize access to ICS, they can gather essential system information, aiding in the information collection phase prior to an attack. Many government websites and infrastructure sites still use HTTP or FTP protocols for plaintext transmission, making them vulnerable to man-in-the-middle attacks. Relevant departments should promptly transition the content from HTTP and FTP protocols to more secure HTTPS and FTPS for transmission to mitigate the risk of attacks.
4) Lack of Integrity Checks
Integrity verification refers to performing a hash check on messages to determine whether they have been altered by hackers during transmission. Most control protocols in industrial control systems do not provide processes for integrity checks, allowing hackers to modify these unchecked messages to achieve their attack objectives.
5) No Storage or Backup of Network Configurations
After suffering network configuration change attacks, it is difficult to promptly restore the original network configuration of devices, leading to poor maintenance and data loss. To maintain network device configurations, relevant configurations should be backed up in a timely manner, and related documentation should be developed.
6) Incomplete Management Experience
Domestic management experience is incomplete, and there should be a continuous absorption of excellent experiences from both domestic and international sources, as there is a lack of relevant security management standards and references. In contrast, foreign countries have relatively more established management regulations. Additionally, industrial control systems should be able to track event records and assign responsibility. A common issue in some important basic departments is internal personnel rather than external factors, thus differentiating permissions for different individuals is essential, and careful consideration should be given to checks and balances for particularly important permissions.
References



Scan to Follow Us
“Intelligent Manufacturing Garden”
Adhering to the concept of “Advanced Manufacturing, Strong Manufacturing Nation”,
Tsinghua Press provides professional knowledge services for everyone!