A few days ago,
the news of Google cracking the SHA-1 algorithm flooded my social media feed.
In fact, the term “crack” is not entirely accurate,
it should be
that they published an example of breaking the SHA-1 algorithm.
Regarding this news,
I saw two different comments:
A: Wow, that’s amazing! They actually cracked an encryption algorithm, the world is so dangerous, should I go back to Mars?
B: Google just spent a lot of computing resources to verify the cracking algorithm, there’s nothing impressive about it. I knew SHA-1 was insecure years ago.

In the spirit of seeking the truth,
let’s discuss today:
1. What is the significance of Google’s achievement?
2. Why did Google create such a stir?
—
First, let’s briefly explain hash algorithms.
We know that everyone’s fingerprints are unique,
so fingerprints can be used to verify a person’s authenticity.
(Except for the Monkey King)

In computer systems,
each different file content also has its own fingerprint—hash value
There are many methods to calculate hash values,
such as SHA-1, SHA-2, MD5, etc.
They are collectively referred to as “hash algorithms”

There is a famous American movie called Gone with the Wind,
the SHA-1 hash value calculated is:
5C9CD8EEECE37D8A66206D4652132C00B4D9F8F4
If the hash value of the Gone with the Wind.avi
is different,
you might be misled into downloading the complete collection of “Calabash Brothers”

In simple terms, a hash value is the fingerprint of the digital world.
Now the question arises,
although the probability is very low,
it is still possible for two people’s fingerprints to be exactly the same
and for two files to have the same hash value
In other words,
if I can find someone with the same fingerprint as Jack Ma,
then it is possible to steal Jack Ma’s property
and if I construct a video file with the same hash value as the movie,
I can successfully mislead you into downloading the complete collection of “Calabash Brothers”.

Actually, this is what Google did this time.
They successfully constructed two different PDF files,
with exactly the same SHA-1 hash value

So what does this mean?
Google officially stated:
We have cracked SHA-1 from an application perspective. This cryptographic hash function standard used in the industry is applied in digital signatures, file integrity verification, and protects people’s digital assets in various fields, including credit card transactions, electronic documents, open-source software repositories, and software updates. In practice, we can construct two PDF files with the same SHA-1 result. This allows the SHA-1 digital signature of the second file to be validated by the SHA-1 digital signature of the first file. For example, we can construct two PDF rental agreement files with the same SHA-1 result, where the rental amounts indicated in the agreements are different, but the SHA-1 signature result of the high-rent file is the same as that of the low-rent file. This allows the lessee to sign the low-rent file and then replace it with the high-rent file, achieving the purpose of forging the rental agreement.
The reason some friends feel that Google’s result
is not impressive, not shocking
is because SHA-1 has long been theoretically proven to be crackable
but the computational cost is extremely high.
In 2005,
Chinese cryptography expert Wang Xiaoyun
collaborated with the Yao Qizhi couple
to propose a cracking method
which reduced the time to crack SHA-1 from 2^69 steps to 2^63 steps,
making the Chinese cryptography field shine on the world stage.

[Wang Xiaoyun]
By the way,
the aforementioned Yao Qizhi is the Turing Award winner who recently gave up his foreign nationality to become an academician of the Chinese Academy of Sciences along with Yang Zhenning.

[Yao Qizhi]
That research result forced the National Institute of Standards and Technology (NIST) to start selecting new SHA-2 series hash functions.
However, due to the high cost of cracking,
SHA-1 is still in widespread use.
After that,
scholars have been working hard to find more efficient cracking methods.
In 2013,
a guy named Stevens reduced the computational amount needed to crack it to
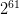
In 2016,
he once again reduced the computational amount to
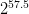
Google borrowed his cracking method this time
and using this method,
it would take about a year of computation on 100 GPUs to crack it
which would cost tens of thousands of dollars
the cost is indeed not low,
but for national institutions and advanced hacker organizations,
it’s simply a drop in the bucket.

Regarding the significance of this achievement,
I believe it serves as a warning bell
Just like people know that weak passwords are not secure,
but only when one account theft incident happens around them
will people truly learn their lesson.

Now we come to the second question:
Why has Google been so determined to push for the demise of the SHA-1 algorithm?
As the author of this article knows,
many websites that use SSL encryption use the SHA-1 algorithm to prevent their identity from being impersonated.
use the SHA-1 algorithm to prevent their identity from being impersonated.
When you visit a website ,
,
it ensures that you are indeed visiting the genuine Facebook,
and that you won’t send your password to an attacker.
To complete the verification work,
your browser determines whether the website’s certificate is issued by an authoritative agency.
(Certificate Authority, abbreviated as “CA”)
The process of browser verifying certificates is as follows:
When the browser encounters a certificate,
it calculates the SHA-1 value of the certificate information,
and then compares it with the original SHA-1 value used as identification.
If the two values are the same,
the browser is confident that the provided certificate and the CA-issued certificate are the same,
and have not been tampered with.
If you design a certificate
that can collide with the target site’s certificate,
and then trick the CA into issuing you this certificate,
ultimately, you can use this certificate to impersonate the target site,
even if the browser cannot distinguish between true and false.
The certificate spoofing process
is somewhat similar to me misleading you into downloading the complete collection of “Calabash Brothers”.
Now that SHA-1 is insecure, there are two solutions:
Certificates issued by CA do not support SHA-1
Browsers do not provide SHA-1 certification
However,
before the SHA-1 algorithm, there was also an algorithm called MD5
which was disclosed to have theoretical vulnerabilities in 1995,
but until 2008, MD5 was still used by some CAs.
Well, relying on CAs to eliminate SHA-1 is hopeless,

So, to prevent the use of SHA-1 for forging certificates
there is only one way:
Browsers cancel support for SHA-1.
Two or three years ago, Google announced that due to the weakness of SHA-1,
it planned to display warnings to users in the Chrome browser
Although Microsoft and Mozilla (Firefox) also released related plans early on,
Google was still the one leading the charge.
By doing this,
the browsers would face an awkward situation:
When the browser tells users that an important site is at risk, users will think there is a problem with the browser and will switch to another browser.
Just like when you are browsing some websites, if the browser tells you that the site is unsafe and does not allow you to view it, in many cases, you will still click to continue visiting, or switch to another browser that doesn’t interrupt.
Thus, it explains why Google has been continuously conveying a message:
SHA-1 is no longer secure! Hurry up and change! Browser vendors, quickly join the resistance!
Charging too far ahead, while teammates have not kept up, feels a bit insecure.
By the way, the Safari team has yet to express a stance on this SHA-1 issue.
However, overall, Google being the first to take the plunge, promoting the iteration of encryption algorithms, and enhancing overall network security is commendable! It should be fully supported!

Note: The above content references these sources:
Zhihu Q&A: “How to evaluate Google’s announcement of achieving SHA-1 collision on February 23?” by Liu Weiran – Xuesu;
Freebuf 2014 Rabbit_Run translated article: “Why is Google in a hurry to kill the SHA-1 encryption algorithm?”
Source: Zhai Ke Channel (with slight modifications from the original)

Editor: yangfz
Recent Hot Articles Top 10
↓ Click the title to view ↓
1. How big is the difference between grabbing WeChat red envelopes first and later? Big data analysis gives you the answer!!
2. A map to the world of mathematics
3. EVA’s explosive nuclear weapon finally realized! A Chinese team synthesized the all-nitrogen anion salt for the first time
4. Remembering these key moments can save lives! (Part 1) | Online Science Day
5. Is it physics that makes the aging of the human body inevitable, not biology
6. The mental poison of doctoral students, male doctoral students will be silent, female doctoral students will cry, which line made you cry?
7. Scientific flirting techniques! Ten small experiments to help you easily express your affection | Online Science Day
8. Academician of the Chinese Academy of Sciences teaches you to dismantle CP on Valentine’s Day!
9. All our knowledge of geography in middle school actually comes from one person!
10. Why does lightning not travel in a straight line?| No.44
Click here to view all past hot articles
