
Of course, this behavior is very unethical, hiding behind a screen and trampling on education and law at will. However, the relevant departments have also taken timely measures to prevent such incidents from occurring frequently.

Back to the point, if an intruder directly cracks passwords through technical means to disrupt classes, does this “password” have any effect on the internet?
Speaking of the word “password”, many people might feel it is mysterious. This is because cryptography is a niche discipline, and its professionalism cannot be understood and mastered by the general public. Therefore, both passwords and hackers are mysterious terms. Today, I, Xiaokun, will take everyone to understand the past and present of cryptography, and I believe everyone can understand!
The History of Cryptography
The origin of cryptography actually dates back a long time. According to historical records, the earliest primitive codes appeared in the 5th century BC, when the ancient Greek Spartans used a primitive cipher device. It was made by wrapping a strip around a stick, writing the plaintext along the stick, and then unwinding the strip to create a jumbled ciphertext.
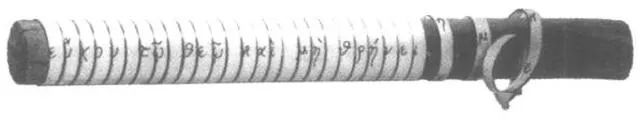
By the 1st century BC, the most famous was the Caesar cipher, which was widely used during the Gallic Wars. The Caesar cipher is also a simple monoalphabetic cipher where all letters in the plaintext are replaced by letters shifted a fixed number of places down the alphabet. For example, when the shift is 3, all instances of the letter A will be replaced by D, B becomes E, and so on.
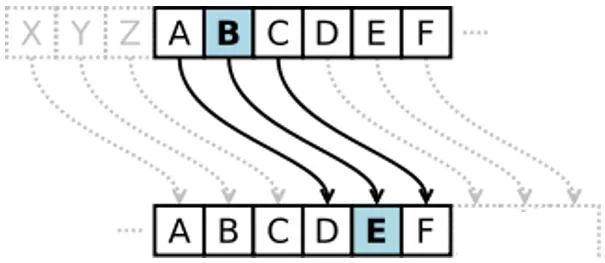
Then, in the late 16th century, the single Caesar cipher was expanded into what is known as the Vigenère cipher. It is an encryption algorithm that uses a series of Caesar ciphers to form a password alphabet and introduces the classic concept of a “key” for the first time, meaning that the key determines which row of the cipher table will be used for substitution.

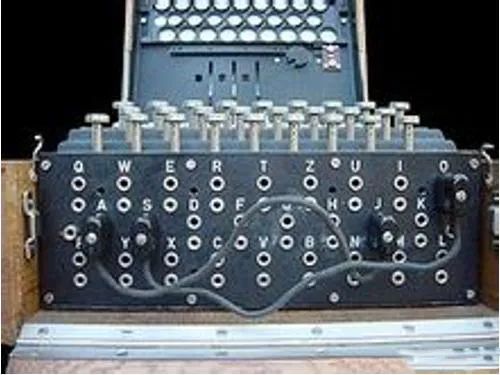
In the history of cryptography, the most famous is the Enigma machine, which is a device used for encrypting and decrypting documents. The Enigma started being used commercially in the early 1920s and was widely adopted by Hitler’s Nazi Germany during World War II.
By the mid-1970s, two epoch-making events occurred in the field of cryptography: in 1976, the DES algorithm was issued as a national standard algorithm by the National Bureau of Standards in the United States. That same year, Diffie and Hellman proposed the new idea of public-key cryptography at Stanford University, which divided keys into an encryption public key and a decryption private key. This was a true revolution in the history of cryptography, marking the beginning of the modern cryptographic wave.
Overview of Cryptography
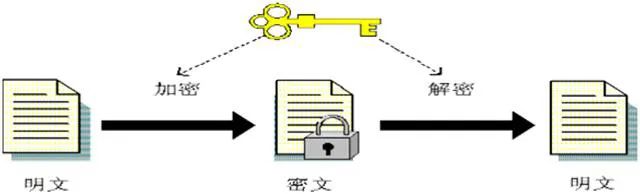
To understand cryptography, one must first grasp some basic concepts within it, such as plaintext, which is the message before being transformed by cryptographic techniques, and encryption, which is the process of disguising a message to conceal its content; ciphertext is the message after encryption; decryption is the process of converting ciphertext back into plaintext; encryption algorithms are mathematical functions used for encryption; and decryption algorithms are mathematical functions used for decryption. The operations of encryption and decryption are usually conducted under the control of a set of keys, referred to as the encryption key and the decryption key.

In fact, cryptographic algorithms can be divided into three categories: symmetric cryptographic algorithms, asymmetric cryptographic algorithms, and hash algorithms.
First, let’s look at symmetric cryptographic algorithms:
A symmetric cryptographic algorithm uses the same key for both encryption and decryption or can easily derive one from the other. The communication model of symmetric cryptosystems is as follows:
Depending on the encryption method, symmetric cryptosystems can be divided into two major categories: block ciphers and stream ciphers.
1) Block ciphers divide plaintext into fixed-length blocks (such as 64bit, 128bit) and then encrypt/decrypt each block using the same key and algorithm, producing ciphertext of fixed length.
2) Stream ciphers, also known as synchronous ciphers, encrypt/decrypt data bit by bit, which means using a known key random sequence to perform XOR operations with the plaintext bit by bit.
At this point, you might wonder: what are the advantages and disadvantages of symmetric cryptosystems?
First, let’s talk about the advantages. The advantages of symmetric cryptography are its fast computational speed and ease of hardware implementation. However, the disadvantages of symmetric cryptosystems are also evident. Before transmitting ciphertext, the sender and receiver need to use a secure channel to communicate the key, leading to a dramatic increase in the number of keys as the number of communicators increases. It does not check the integrity of the transmitted information, making message confirmation problematic, and it lacks the ability to automatically detect key leaks.
Now let’s look at asymmetric cryptographic algorithms:
Asymmetric cryptographic algorithms, also known as public-key algorithms, were proposed by Diffie and Hellman in 1976. They use different keys for encryption and decryption that cannot be derived from each other within a reasonable time. The encryption key is a public key, while the decryption key is a private key.
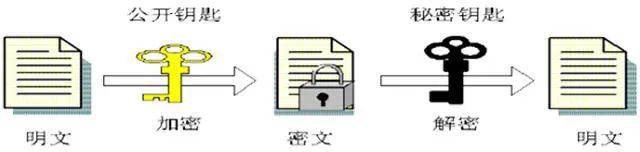
In fact, the emergence of the public-key cryptosystem is a revolutionary development for cryptography because it provides effective and convenient technology for data confidentiality, integrity, and authenticity, while scientifically solving the key distribution problem of symmetric cryptography. In the public-key cryptosystem, notable algorithms include RSA, ElGamal, and elliptic curve algorithms, among which the RSA algorithm is the most classic and influential.
A Brief Discussion on Hash Algorithms
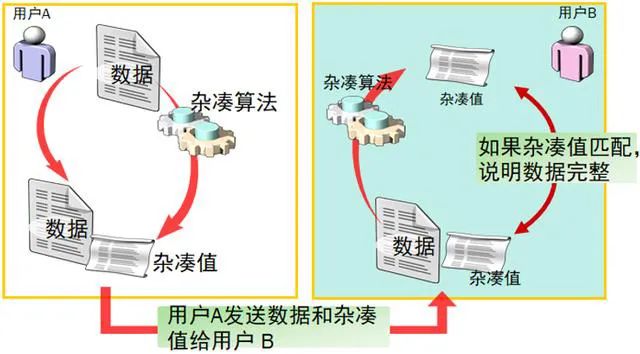
Hash algorithms can take messages of any length as input and produce a fixed-length output, also known as a hash value. In fact, hash algorithms generate a “fingerprint” of the input, and they are widely used in applications such as digital signatures, where a long message is first hashed, and then only the hash value is signed. Another prominent application is in data integrity verification.
The above content provides an overview of the history and concepts of cryptography. Due to its strong professionalism and the mathematical nature of its theories and processes, if you want to master knowledge related to cryptographic algorithms, you must first understand mathematical concepts such as number theory, Boolean operations, and finite field operations.

If you just want to understand this niche discipline, having an impression of the above content means you have already grasped the basics. If you want to delve deeper into professional knowledge related to cryptography, feel free to check out our latest research topics, which are highly specialized and offer significant value.
Latest
Research
Topics
If you have any other questions or want to learn more about research projects, you can scan the QR code below for more details.
———— e n d ————
Come Consult WeChat Assistant (Xinxiaokun)~
Please indicate:
City + Enrollment Year + School + Name + Applied Major + Phone
