At the 2021 Shanghai Auto Show, a female car owner, wearing a T-shirt that read “Brake Failure,” passionately accused Tesla from the roof of her car. Is there really a brake failure? Without data, we cannot know. However, Tesla’s strong corporate stance has made driving data a luxury for car owners seeking to protect their rights, resembling the posture of a data hegemon.
From a national perspective, regarding driving data, the more concerning issue is that the data collected by Tesla vehicles, especially sensitive information related to our territory and geographic information, is not stored on servers within mainland China but rather on overseas servers.This raises concerns about the company’s intent in collecting user information and casts a shadow over the future of information security in the development of connected vehicles.
As this incident continues to gain traction online, the breach of Tesla Model S’s defenses by Tencent’s Keen Security Lab has also come into the public eye.
In 2016, the first successful penetration of a Tesla vehicle brought fame to Tencent’s Keen Security Lab in the automotive industry. In 2017, the lab discovered multiple high-risk security vulnerabilities and achieved remote attacks on Tesla without physical contact, ranging from remotely unlocking any car door with a smartphone to intervening and controlling the braking system, and even controlling various ECU (Electronic Control Unit) modules of the vehicle, allowing for remote control in both parked and driving modes.
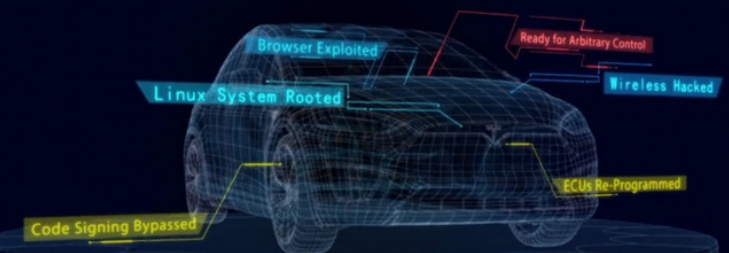
Figure1 Tesla Model S
Warren Buffett once said, “Only when the tide goes out do you discover who’s been swimming naked.” The safety risks of Tesla may just be the tip of the iceberg for many issues facing smart connected vehicles. While smart driving and connected vehicles are currently very popular, one must wonder: if implemented, are we living in an interconnected world without protection? What safety risks will arise in the development of connected vehicles?
First, we need to understand that the Internet of Vehicles (IoV) mainly consists of communication systems between vehicles and various sensors collecting data. Similar to any other network, the vehicle network also follows a layered architecture. However, it differs from traditional network structures in that it requires a more open and flexible layering structure.Researchers have identified a three-layer architecture: the perception layer, the network layer, and the application layer.
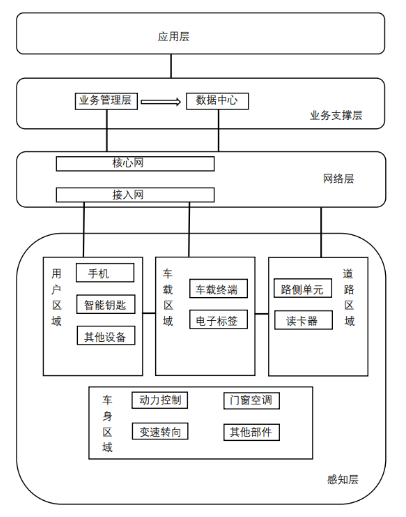
Figure2 System Architecture of IoV
The main security issues in IoV are concentrated in these three layers:
(1) Perception Layer
From Figure 2, it can be clearly seen that the perception layer is the bottom layer of the three-layer architecture, and the information security of various sensors installed on connected vehicles belongs to perception layer security.
The role of the perception layer is simply to collect data from the surrounding environment to help the vehicle identify surrounding objects, while uploading the recognized objects in data form to the upper layer for further network transmission and processing.
The perception layer is like the human eye; we all know that seeing is not necessarily believing; your eyes can deceive you. As the eyes of the IoV, the perception layer can also be subject to interference or even malicious attacks.
Common attack methods include signal interference and eavesdropping attacks. Each sensor on the vehicle has its fixed communication frequency, and if not protected, it is susceptible to hackers’ signal interference, making the information data perceived by the sensors vulnerable to eavesdropping and information leakage. Here, we also explain two types of hacker attacks: active and passive attacks, as shown in Figure 3. Active attacks disrupt normal information transmission, including interruption, tampering, and forgery, making them easier for maintainers to detect. Passive attacks only steal information without altering any data, allowing them to remain “invisible” in the network, making them harder to detect.
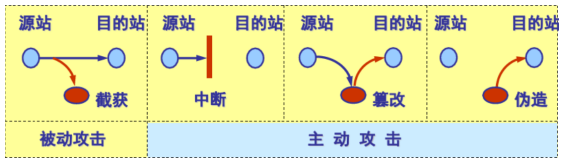
Figure3 Active and Passive Attack Diagram
Taking RFID technology as an example, it is a type of automatic identification technology that uses radio frequency for non-contact bidirectional data communication, utilizing radio frequency to read and write recorded media (electronic tags or RFID cards) for the purpose of identifying targets and exchanging data. The security risks it brings are numerous, mainly including the loss and theft of RFID memory data and the privacy of the driver’s driving trajectory.
Current vehicle systems have implemented keyless systems that also utilize RFID technology.However, due to the lack of a unified standard for keyless systems, many of them have inadequate security measures, posing significant security risks. Hackers can directly exploit system vulnerabilities to intercept wireless transmission signals to crack encryption systems, thereby stealing information.
Of course, there are various attack methods, such as tampering and physical destruction attacks, impersonation node attacks, etc., which will not be detailed here, but they all blind the eyes of the IoV and pose threats to its practical applications.
(2) Network Layer
The network layer is the middle layer of IoV communication, mainly responsible for processing data received from the lower layer and transmitting it to the application layer. It primarily uses network technologies such as LAN, wireless/wired networks, and various transmission media to handle large amounts of data.The communication technologies used in this layer include Wi-Fi, Bluetooth, Zigbee, or UWB (Ultra-Wideband), facilitating seamless integration with emerging networks, as shown in the following table:
Table1 Comparison of Communication Technologies
|
Name |
Wi-Fi |
Bluetooth |
Zigbee |
UWB Ultra-Wideband |
|
Transmission Speed |
1G and above |
1Mbps |
100Kbps |
53-480Mbps |
|
Communication Distance |
20-200 meters |
20-200 meters |
-20 meters |
0.2-40 meters |
|
Security |
Low |
High |
Medium |
High |
|
Power Consumption |
10-50mA |
20mA |
5mA |
10-50mA |
|
Cost |
25¥ |
2-5¥ |
5¥ |
20¥ |
Due to the different types of networks, the network layer itself is susceptible to various network attacks, such as information leakage, denial of service attacks, using network packet capture tools to steal information, viruses, and Trojans.It is important to note that there are multiple wireless interfaces that vehicle nodes can connect to, meaning that the types of wireless connections can also be diverse, such as WI-FI and mobile networks. The current network fusion mechanism caused by various network technologies is not very complete, making it easy for the IoV to have security vulnerabilities.
(3) Application Layer
The application layer is the highest layer of IoV communication, providing storage and processing for data. It is also the aggregation of vehicle information and applications, akin to mobile applications.
Since it is similar to applications, it inevitably faces threats from viruses, just like various viruses on our computers, which have strong network propagation capabilities and can disrupt the normal operation of IoV applications, posing a significant threat to the application layer.
It is also important to note the remote attacks by hackers, who use methods such as DNS poisoning and TCP synchronization to attack the application layer of the IoV remotely, threatening the overall security and stability of the system.
Since it is an application, there are both good and bad, similar to the rogue software we encounter on computers. The IoV application layer will inevitably encounter junk programs that may cause information leakage, such as annoying pop-up ads or unwanted software like adware and spyware. While they may not directly affect the operation of the application layer, they can leak node privacy, posing a risk to information security.
In summary, the threats faced by smart connected vehicles can be illustrated as shown in the following figure:
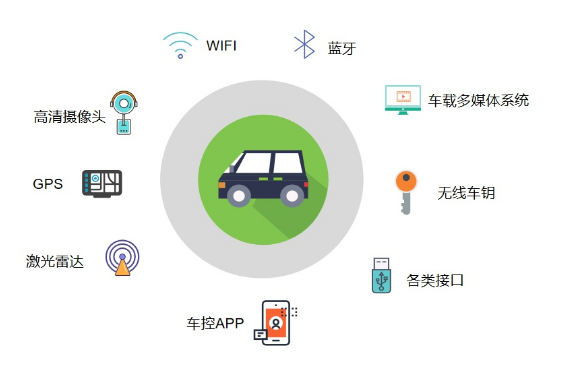
Figure4 Potential Threats to Smart Connected Vehicles
Of course, the above merely scratches the surface of the many information security risks facing smart connected vehicles. This leads us to wonder: given the multitude of risks, can the IoV truly be implemented? With threats and risks, we naturally have countermeasures.
To ensure that the IoV system operates efficiently and securely, there is already a security protection system in place for the three layers mentioned above, as illustrated in the following diagram:
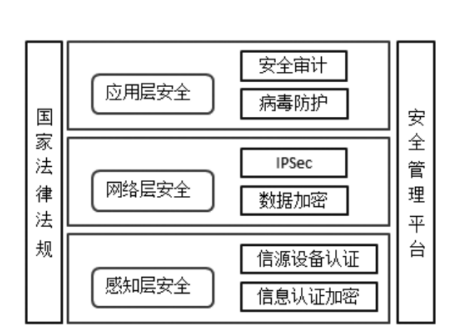
Figure5 IoV Security Architecture Diagram
At the perception layer, to ensure the privacy of nodes and the speed of pseudonym replacement, efficient node information authentication methods need to be used to prevent counterfeit nodes from passing authentication. Meanwhile, intrusion detection must be strengthened so that when subjected to active and passive attacks at the perception layer, attacks can be quickly detected, and defense measures can be taken.
Network layer devices need to monitor the various ports of devices, the operational status, and performance of system devices, reporting and addressing issues promptly.
So how can we ensure the security of the network layer?To ensure the integrity of data transmission, an IPSec and SSL encryption technology system needs to be established to encrypt and transmit data obtained from the IoV perception layer, preventing data from being tampered with during transmission.
As the top layer of the network architecture, the security measures for the application layer are crucial. First, data must be encrypted and subjected to security audits. Most information needs to be encrypted before transmission to ensure data integrity and privacy security. Second, a firewall must be established for the IoV application layer. By filtering unsafe information and services through the firewall, certain virus attacks can be effectively filtered, achieving virus protection. However, the firewall settings must also consider the characteristics of IoV communication, such as real-time and high dynamics.
With threats and opportunities coexisting, the road to IoV security is long. As a technology that can benefit humanity, it is hoped that IoV-related companies and management departments will pay enough attention to security issues, and that relevant manufacturers and research institutions will further improve security protection technologies. Of course, it is also essential for the government to enact laws and regulations related to IoV security.
In the future IoV era, security will no longer be a luxury for consumers, and privacy will become a basic dignity for car owners.
Jia Ding Intelligent Low Carbon Vehicle Popular Science Ecological Construction Plan, sponsored by the Shanghai Science and Technology Commission’s popular science project (Project No: 20DZ2306500)
· END ·