Researchers from the industrial cybersecurity company Claroty revealed on January 17 that their Team82 discovered five exploitable vulnerabilities (CVE-2022-46732, CVE-2022-46660, CVE-2022-43494, CVE-2022-46331, and CVE-2022-38469) in GE Digital’s Proficy Historian server, affecting multiple critical infrastructure sectors. Threat actors could exploit these vulnerabilities to access historical data, crash devices, or execute code remotely. These vulnerabilities impact GE Proficy Historian v7.0 and later, with one vulnerability having a CVSS v3 score of 9.8, while the other four have a CVSS v3 score of 7.5. The presence of these vulnerabilities is particularly concerning in ICS and operational technology (OT) environments, as these historical database servers share process information with enterprise systems, creating an attractive pivot point for attackers to jump from IT networks to OT systems. By exploiting this set of vulnerabilities, attackers could execute arbitrary code with SYSTEM privileges on remote GE Proficy Historian servers. Additionally, attackers could build a fully functional shell command line interface (CLI) that supports various commands, including bypassing authentication, uploading arbitrary files, reading arbitrary files, deleting arbitrary files, and executing code remotely. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) quickly released an ICS advisory identifying these vulnerabilities as allowing for authentication bypass via alternate paths or channels, unrestricted file uploads of dangerous types, improper access control, and weak password encoding. Currently, GE has stated that GE Proficy Historian v8.0.1598.0 is affected, and corresponding mitigations for all recently released vulnerabilities in GE Proficy Historian have been published, urging users to upgrade for protection.
Team82 Reproduced the Exploit
Database servers in ICS environments can serve as a bridge between an organization’s information technology (IT) network and its operational technology (OT) network. Uri Katz, a security researcher from Claroty’s Team82, emphasized this in his article analyzing the GE Proficy vulnerabilities.
“Due to its unique position between IT and OT networks, attackers target historical databases and can use them as a pivot point to access OT networks,” Katz said. “Historical databases often contain valuable data about industrial processes, including information about process control, performance, and maintenance.”
The Importance of Database Historical Servers
Database historical servers (also known as operational historical servers or process historical servers) enable companies to monitor and analyze data from their industrial control systems and physical device networks. Essentially a data lake for storing time-series data in industrial environments, historical databases collect real-time information about critical infrastructure, manufacturing, and operations.
However, for attackers, historical database servers represent an opportunistic bridge between the IT and OT parts of the network, as they are typically centralized databases connected to both. Therefore, according to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), historical servers have been identified as potential attack targets in ICS networks, including man-in-the-middle attacks and database injection attacks.
Databases are a common attack point for threat actors, but an uncommon type of database is being highlighted as a potential key target: historical data servers. The GE database vulnerabilities are not isolated incidents: in the past, security researchers have also found similar security issues in Schneider Electric’s Vijeo Historian Web server and Siemens’ SIMATIC Process Historian.
ICS historical databases usually operate by collecting data from various sources within industrial control systems, such as control devices, sensors, and programmable logic controllers (PLCs). The collected data is typically gathered through SCADA-specific protocols or OPC DA/OPC UA, simplifying the data collection process. The data is then stored in databases and made available through user interfaces or APIs.
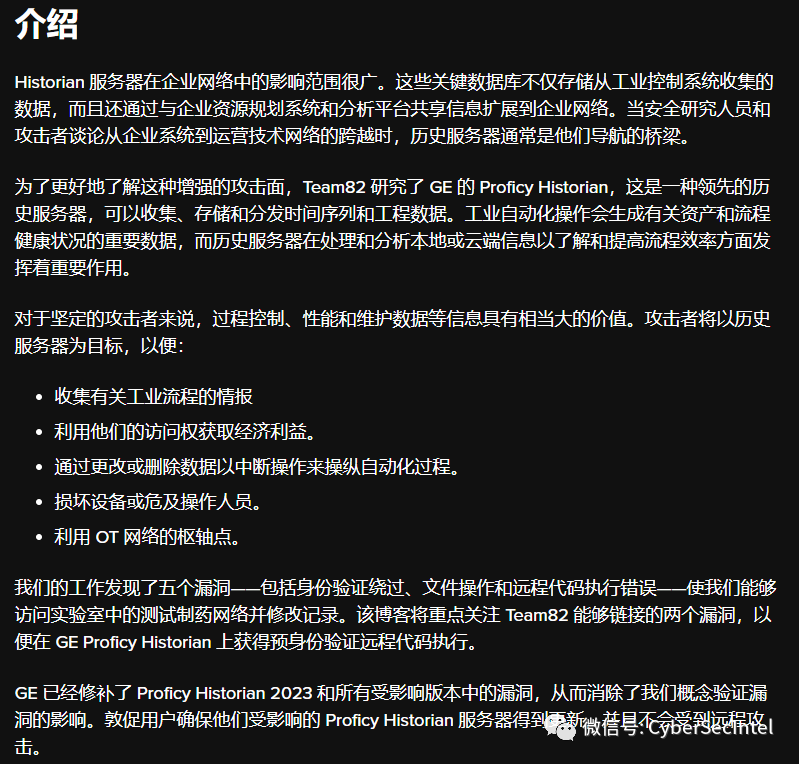
In addition to process links through sensors, control devices, and PLC networks, historical databases can also connect to other systems, such as enterprise resource planning (ERP) systems and analytics platforms, for more comprehensive data analysis and decision-making.
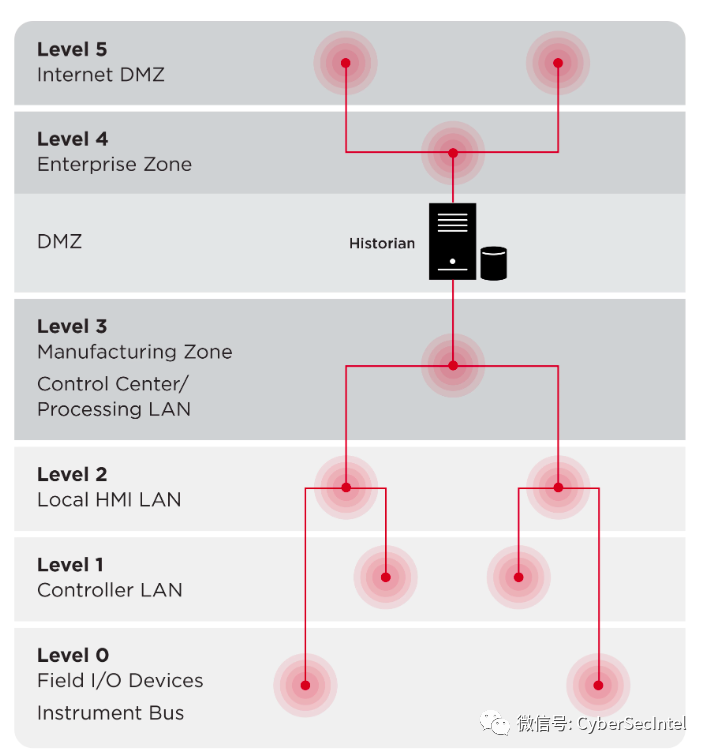
For various reasons, historical databases may become targets for attackers. One major reason is that historical databases often contain valuable data about industrial processes, including information about process control, performance, and maintenance. Attackers may target ICS historical databases to gain access to this data for economic gain or to gather intelligence about industrial processes.
Another reason attackers may target ICS historical databases is that they can be used to disrupt or manipulate industrial processes. For example, an attacker with access to ICS historical records may be able to alter or delete data, or otherwise manipulate data to disrupt the operation of industrial processes. This could have serious consequences, such as disrupting commodity production, creating safety hazards, or damaging equipment.
ICS historical databases may also be part of larger-scale network attacks against industrial control systems. In such cases, attackers may use ICS historical databases as a stepping stone to access other parts of the network or to steal data from the system.
The Importance of DMZ Protection
CISA noted in its control system network security deep defense strategy document that while integrating IT and OT networks can make industrial technology more agile and cost-effective, “multi-network integration strategies often lead to vulnerabilities that significantly reduce an organization’s security and may expose critical mission control systems to cyber threats.”
While only one of the four ICS recommendations released by CISA on January 17 relates to historical servers, CISA has previously warned about vulnerable historical database servers, such as the 2021 Siemens SIMATIC Process Historian vulnerability. In previous ICS-CERT advisories, the organization has also warned about default passwords in vulnerabilities in Schneider Electric’s Wonderware Historian in 2017 and Schneider Electric’s Vijeo Historian Web server in 2013.
Claroty’s Team82 installed historian software, outlined the message structure it uses for communication, and looked for methods to bypass authentication to compromise the server. The vulnerabilities it discovered could allow attackers to bypass authentication, delete code libraries, replace libraries with malicious code, and then execute that code.
In an email interview, Katz from Team82 said that so far, there have been no publicly reported incidents where attacks using historical servers have caused harm. However, he added that historical database servers do represent an interconnectedness between operational networks and information networks that may be exploited in the future.
“Historian servers are generally not exposed to the internet, but they are often located in the DMZ layer between enterprise networks and OT networks,” he said. “Some vulnerabilities can be chained together to bypass authentication and achieve pre-authentication remote code execution.”
Experts say that industrial and critical infrastructure organizations should include historical database servers in their cybersecurity planning. In a list of five scenarios that companies should execute as ICS tabletop exercises, Dean Parsons of the SANS Institute pointed out a vulnerability involving data historians collecting sensitive device and control data.
“A set of compromised IT Active Directory credentials [can] be used to access the Data Historian and then pivot into the industrial control environment,” Parsons said, who is also the CEO and chief consultant of ICS Defense Force. “It is critical to separate ICS networks from the Internet and IT business networks.”
Claroty’s Katz said organizations should ensure that historical servers are up-to-date and separated from other parts of the network. “Network segmentation is… a mitigation measure that can help defend against these vulnerabilities and prevent attackers from using them as a pivot from IT to OT,” he said.
Some ICS cybersecurity vendors, such as Waterfall Security and Clarify, limit access to historical servers. Instead, they clone systems or provide proxy services in the IT segment, allowing engineers and technicians to access data while preventing attackers from executing code or altering data.
1. https://claroty.com/team82/research/hacking-ics-historians-the-pivot-point-from-it-to-ot
2. https://industrialcyber.co/threats-attacks/clarotys-team82-details-five-exploitable-vulnerabilities-in-ge-proficy-historian-deployed-in-critical-infrastructure-sectors/
3. https://www.darkreading.com/ics-ot/vulnerable-historian-servers-imperil-ot-networks


