
The COVID-19 pandemic has made remote working the new norm and brought the business world into a phase that is yet to be explored. Undoubtedly, due to the lack of face-to-face interaction and standard distance restrictions, many users have had to digitally sign some official documents over the past few years. To maintain the authenticity and integrity of such documents containing key information, DSA algorithm was proposed and adopted as a global standard for verifying digital signatures.
Before continuing to study the algorithm, you will review asymmetric encryption since it validates digital signatures based on asymmetric encryption architecture (also known as public key encryption architecture).
What Is Asymmetric Encryption
In asymmetric encryption methods, you use two different keys, one for encryption and the other for decryption. You use the public key for encryption; meanwhile, you use the private key for decryption. However, you must generate both keys from the receiving end.
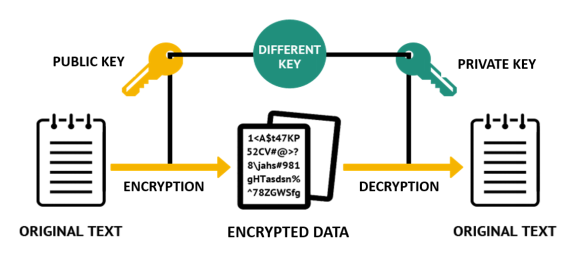
As shown in the above figure, using separate keys for encryption and decryption helps eliminate key exchange, as is the case with symmetric encryption.
For example, if Alice needs to send a message to Bob, then both the private and public keys must belong to Bob.
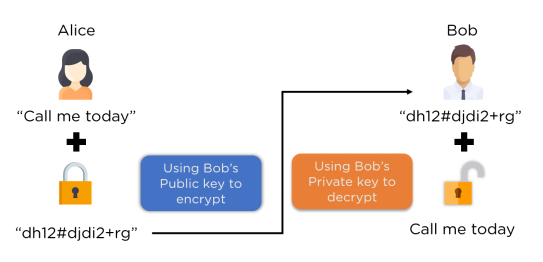
The flow of the above figure is as follows:
-
Step 1:Alice first encrypts the message using Bob‘s public key
-
Step 2: The encrypted message arrives at Bob
-
Step 3:Bob decrypts the message with his key
This eliminates the requirement for the sender and receiver to exchange any keys, thus minimizing the opportunity window for exploitation. Now that you understand how asymmetric encryption occurs, you will learn how to set up a digital signature architecture.
What Is a Digital Signature
The purpose of a digital signature is to authenticate and verify documents and data. It can prevent official documents from being tampered with or forged during transmission.
Typically, asymmetric key systems use public key encryption and private key decryption. However, for digital signatures, the situation is exactly the opposite. The signature is encrypted using the private key and decrypted using the public key. Because the keys are linked, decoding with the public key can verify whether the private key that signed the document is correct, thus validating the signature’s origin.
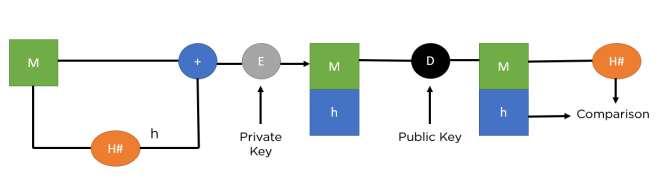
M – Plaintext (Plaintext)
H – Hash function (Hash function)
h – Hash digest (Hash digest)
‘+’ – Bundle both plaintext and digest (Bundle plaintext and digest)
E – Encryption (Encryption)
D – Decryption (Decryption)
The above figure shows the entire process from key signing to verification. Therefore, please complete each step to thoroughly understand the process.
-
Step 1:M, the original message, is first passed to the hash function represented by H# to create a digest.
-
Step 2:Next, it bundles the message with the hash digest h and encrypts it using the sender’s private key.
-
Step 3:It sends the encrypted bundle to the receiver, who can decrypt it using the sender’s public key.
-
Step 4:Once it decrypts the message, it passes through the same hash function (H#) to generate a similar digest.
-
Step 5:The newly generated hash value is compared with the bundled hash value received with the message. If they match, it verifies data integrity.
There are two industry-standard ways to implement the above methodology. They are:
1. RSA Algorithm
2. DSA Algorithm
Both algorithms serve the same purpose, but there are significant differences in encryption and decryption functions. Now that you understand how it should operate in verifying signatures, let’s delve into our focus today, the DSA algorithm.
What Is the DSA Algorithm?
The Digital Signature Algorithm is the FIPS (Federal Information Processing Standard) for digital signatures. It was proposed in 1991 and globally standardized by the National Institute of Standards and Technology (NIST) in 1994. It operates within the framework of modular exponentiation and the discrete logarithm problem, which are computationally difficult as strong systems.
The DSA algorithm provides the following three benefits:
-
Message Verification: You can verify the source of the sender using the correct combination of keys.
-
Integrity Verification: You cannot tamper with the message because it prevents the bundle from being fully decrypted.
-
Non-repudiation: If the signature is verified, the sender cannot claim they never sent the mail.
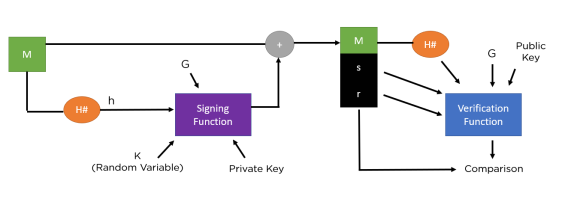
The above figure shows the entire process of the DSA algorithm. Here, you will use two different functions, one for signing and one for verification. The difference between the image of a typical digital signature verification process and the one above lies in the encryption and decryption parts. They have different parameters, which you will study in the next section of this lesson on the DSA algorithm.
Steps of the DSA Algorithm
Remember the above figure, let’s continue to see how the entire process works, from key generation to final signature verification.
1. Key Generation
-
You first choose a prime number q, known as the prime divisor.
-
Choose another prime number p such that p-1 mod q = 0.
-
Choose an integer g (1<g<p) that satisfies two conditions, g**q mod p = 1 and g = h**((p–1)/q) mod p.
-
x is our private key, which is a random integer such that 0 < x < q.
-
y is our public key, which you can compute as y = g^x mod p.
-
Now the private key package is {p,q,g,x}.
-
The public key package is {p,q,g,y}.
2. Signature Generation
-
It passes the original message (M) through the hash function (H#) to obtain our hash digest (h).
-
It passes the digest as input to the signing function, which aims to provide two variables as output, s and r.
-
In addition to the digest, you can also use a random integer k such that 0 < k < q.
-
To calculate the value of r, use the formula r = (g^k mod p) mod q.
-
To calculate the value of s, use the formula s = [K-1(h+x . R)mod q].
-
Then the signature is packed as {r,s}.
-
The entire message package and signature {M,r,s} are sent to the receiver.
3. Signature Verification
-
You use the same hash function (H#) to generate the digest h.
-
Then this digest is passed to the verification function, which also requires other variables as parameters.
-
Calculate the value of w such that: s*w mod q = 1.
-
Calculate the value of u1 according to the formula, u1 = h*w mod q.
-
Calculate the value of u2 according to the formula, u2 = r*w mod q.
-
The final verification component v is calculated as v = [((g^u1 . y^u2) mod p) mod q].
-
It compares the value of v with the value of r received in the bundle.
-
If they match, the signature verification is complete.
Now that you understand the functionality of the DSA algorithm, you must know its advantages over alternative standards like the RSA algorithm.
Advantages of DSA

-
Highly Robust: DSA is highly robust in the security and stability aspect compared to alternative signature verification algorithms.
-
Better Speed: The key generation is much faster compared to the RSA algorithm and such.
-
Less Storage: DSA requires less storage space to work its entire cycle.
-
Patent Free: When NIST released it, it was patent-free to enable its global use free of cost.
-
Highly Robust: DSA is highly robust in terms of security and stability compared to other signature verification algorithms.
-
Better Speed: Key generation is significantly faster compared to algorithms like RSA.
-
Less Storage Space: DSA requires less storage space to run its entire cycle.
-
No Patent: When NIST released it, it was patent-free, allowing for global use without cost.
This concludes our lesson on the DSA algorithm.
How Simplilearn Can Help You?
We hope this article helps you understand the importance of digital signatures in this era, as well as the impact of cryptography in shaping business threat models. However, this is just a small part of the vast ocean of cybersecurity, an industry with a growing demand for trained professionals.
Simplilearn offers a “Cybersecurity Expert” course that will teach you all the knowledge you need to start a career in cybersecurity or enhance your skills. The course is filled with industry-leading learning topics, helping you understand everything you need to learn before stepping into the field.
Conclusion
By now, you have understood the importance of asymmetric cryptography, how digital signatures work, the functionality of DSA, the steps involved in signature verification, and its advantages over similar counterparts. We hope this tutorial helps you understand the DSA algorithm. If you have any questions regarding this article on the DSA algorithm, please let us know in the comments section of this tutorial, and our experts would be happy to assist you.
Click the blue text
Follow us
If you have any other questions
You can contact us through the service account at the bottom

[Shengpulun Digital Technology]
Contact Us
Or call the contact number
4008061196
We are committed to serving you
Email: [email protected] Website: www.shengpulun.com
Shengpulun is committed to introducing world-class digital technology online courses to cultivate practical digital talents for the progress and development of the domestic digital industry. Helping companies and individuals provide cutting-edge skills needed in the job market for data science, artificial intelligence, machine learning, cloud computing, and the digital economy.