
This article is an excellent piece from the KX Forum
Author from KX ForumID: Mr.YX
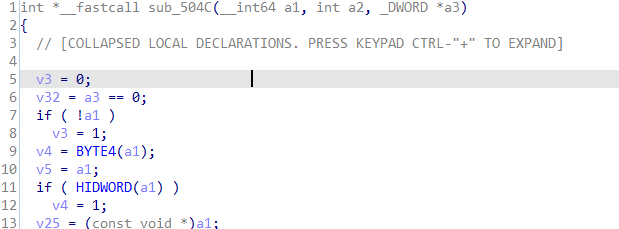
1. Open libsmsdk.so, locate the JNI_Onload function, import the jni.h file, and find the RegisterNatives function.
if ( v11 == -2109534065 ) { v20 = v9->functions->RegisterNatives(&v9->functions, v34, (const JNINativeMethod *)off_7283C, 6); v5 = -1802225456; v10 = 86439211; v11 = -(~(v20 >> 31) | 0x3253F2B3) - 581453431; }2. off_7283C is the function dynamically registered with JNI.
.data.rel.ro:0007283C off_7283C DCD aZ1 ; DATA XREF: JNI_OnLoad+2F0↑o.data.rel.ro:0007283C ; JNI_OnLoad+2F6↑o ....data.rel.ro:0007283C ; "z1".data.rel.ro:00072840 DCD aLandroidConten ; "(Landroid/content/Context;)Ljava/lang/S"....data.rel.ro:00072844 DCD sub_3F094+1.data.rel.ro:00072848 DCD aX2 ; "x2".data.rel.ro:0007284C DCD aLjavaLangStrin_2 ; "(Ljava/lang/String;Ljava/lang/String;)L"....data.rel.ro:00072850 DCD sub_3F098+1.data.rel.ro:00072854 DCD aX4 ; "x4".data.rel.ro:00072858 DCD aLjavaLangStrin_2 ; "(Ljava/lang/String;Ljava/lang/String;)L"....data.rel.ro:0007285C DCD sub_3F0A0+1.data.rel.ro:00072860 DCD aX6 ; "x6".data.rel.ro:00072864 DCD aLjavaLangStrin_2 ; "(Ljava/lang/String;Ljava/lang/String;)L"....data.rel.ro:00072868 DCD sub_3F524+1.data.rel.ro:0007286C DCD aZ3 ; "z3".data.rel.ro:00072870 DCD aLjavaLangStrin_3 ; "(Ljava/lang/String;)I".data.rel.ro:00072874 DCD sub_3F634+1.data.rel.ro:00072878 DCD aY2_0 ; "y2".data.rel.ro:0007287C DCD aZljavaLangStri ; "(ZLjava/lang/String;ZLjava/lang/String;"....data.rel.ro:00072880 DCD sub_3F7AC+1{ "data": { "pri": "......", "fingerprint": "......", "tn": ".....", "sessionId": "......", "fpEncode": xx }, "encrypt": 1, "organization": "......", "channel": "......"}at java.net.SocketOutputStream.write(SocketOutputStream.java:153) at com.android.okhttp.okio.Okio$1.write(Okio.java:76) at com.android.okhttp.okio.AsyncTimeout$1.write(AsyncTimeout.java:155) at com.android.okhttp.okio.RealBufferedSink.emitCompleteSegments(RealBufferedSink.java:176) at com.android.okhttp.okio.RealBufferedSink.write(RealBufferedSink.java:46) at com.android.okhttp.internal.http.Http1xStream$FixedLengthSink.write(Http1xStream.java:288) at com.android.okhttp.okio.RealBufferedSink.emitCompleteSegments(RealBufferedSink.java:176) at com.android.okhttp.okio.RealBufferedSink$1.write(RealBufferedSink.java:198) at java.io.OutputStream.write(OutputStream.java:75) at com.ishumei.O000O0000O0oO.O000O00000OoO.a(Unknown Source:245) at com.ishumei.O000O0000O0oO.O000O00000OoO.a(Unknown Source:119) at com.ishumei.O0000O000000oO.O000O0000OoO$O0000O000000o$1.run(Unknown Source:94) at android.os.Handler.handleCallback(Handler.java:790) at android.os.Handler.dispatchMessage(Handler.java:99) at android.os.Looper.loop(Looper.java:164) at android.os.HandlerThread.run(HandlerThread.java:65)public static String a(boolean z, String str, boolean z2, String str2) { try { return new SMSDK().y2(z, str, z2, str2); } catch (Throwable th) { throw new IOException(th); } }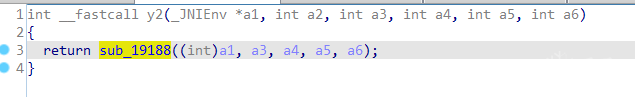
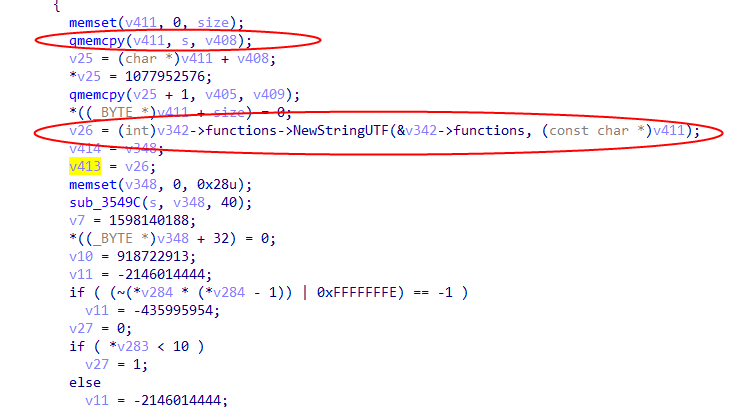
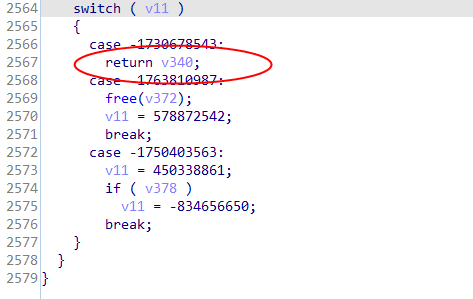
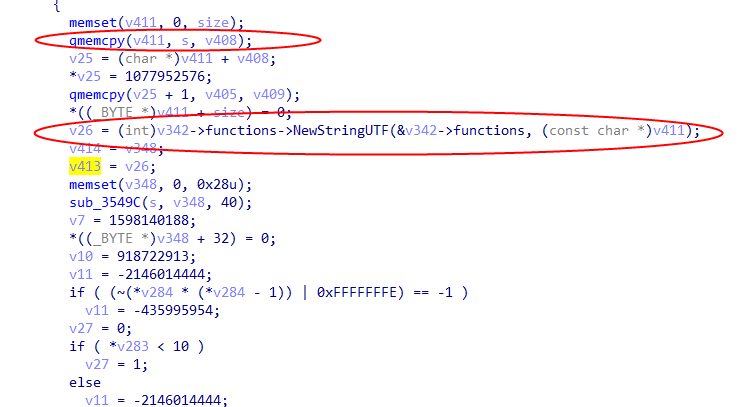
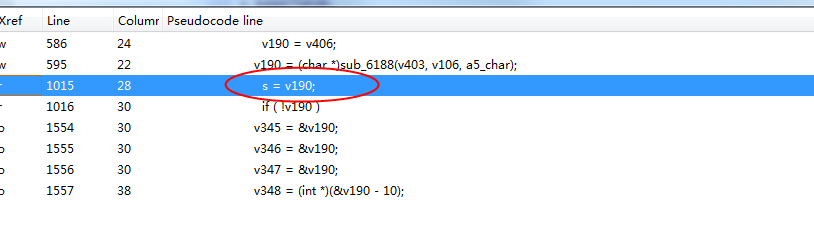
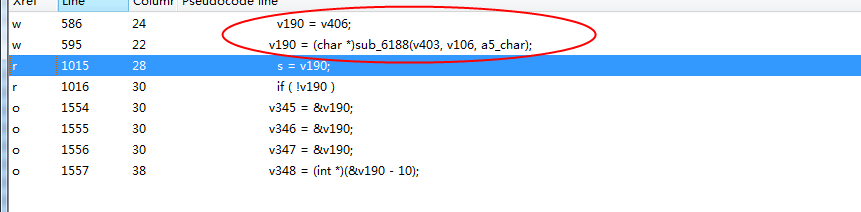
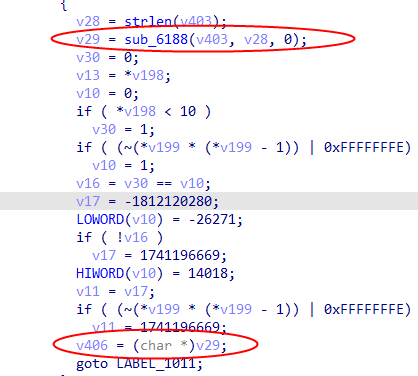
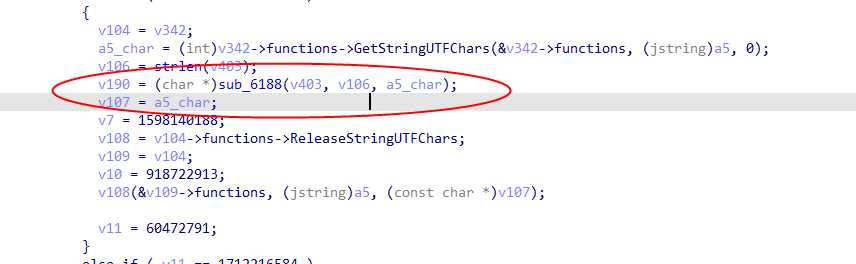
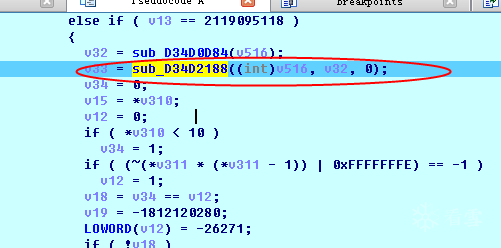

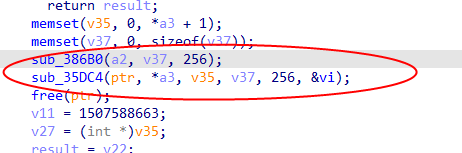
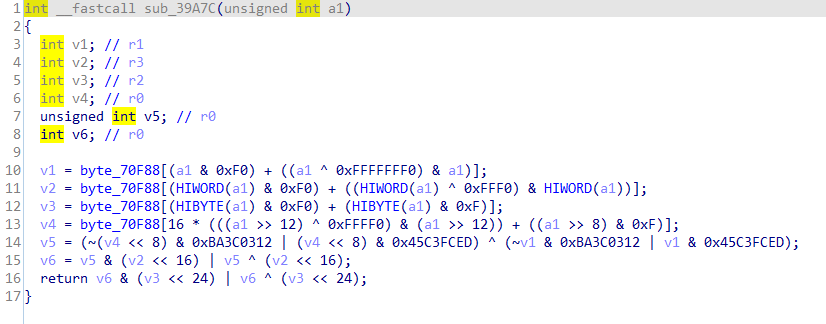
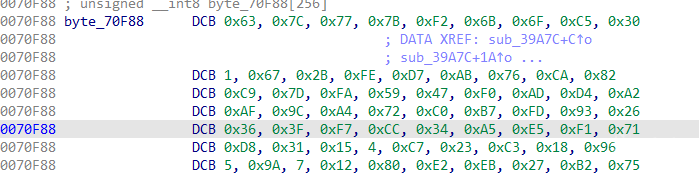
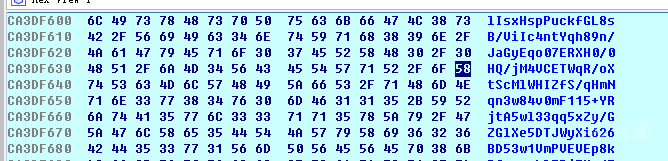 It can be confirmed that this function is the encryption algorithm.
It can be confirmed that this function is the encryption algorithm. 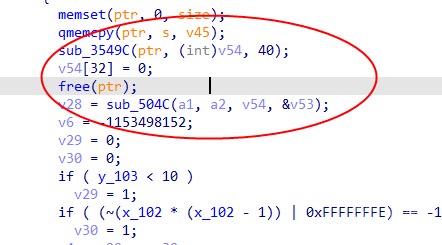
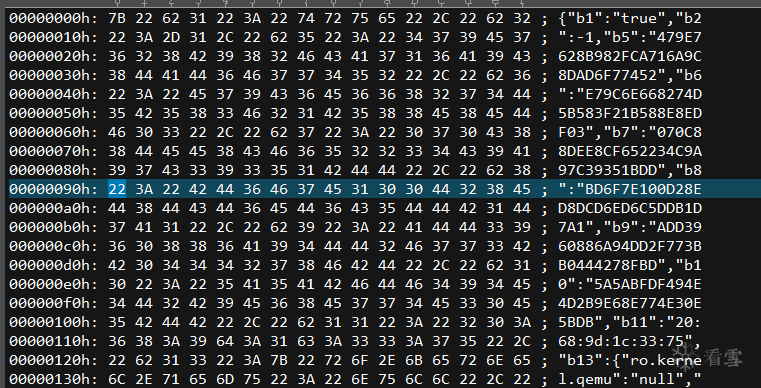
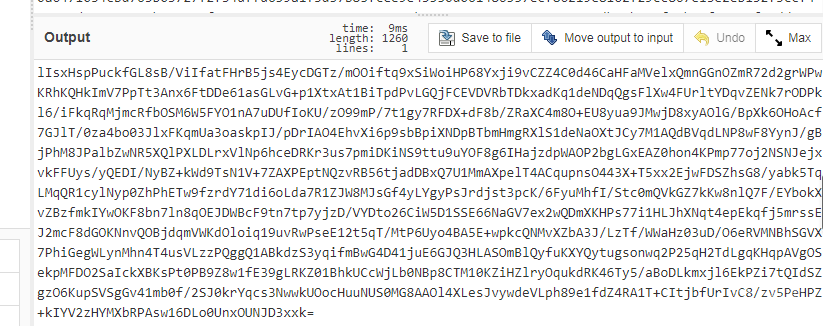
 Success!
Success!

KX ID: Mr.YX
https://bbs.pediy.com/user-home-853873.htm
# Previous Recommendations
-
Tool Use – From IDA to Understanding
-
A Method to Remove Virtual Machine Shell through Backend Compilation Optimization
-
Fuzzing Thunder’s Torrent Parsing Logic with WinAFL
-
AFL’s LLVM Mode Source Code Analysis
-
Linux Kernel Privilege Escalation Vulnerability CVE-2016-5159
Share the Ball
Like the Ball
Watch the Ball

Click “Read the Original” to learn more!