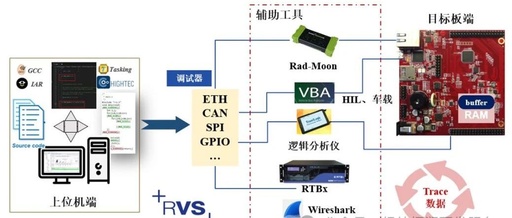
Introduction to ECU Control Software Development and Testing
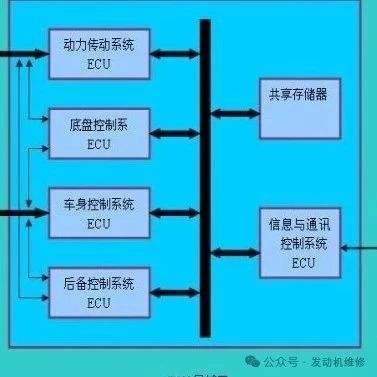
With the background of technological advancements in electrification, intelligence, and connectivity, the electronic and electrical architectures across various industries are undergoing profound transformations. New architectures are gradually replacing traditional ones in fields such as automotive, engineering machinery, energy storage, and shipping, transitioning from traditional distributed architectures to domain-centric and even central-centric models, with controller functions … Read more