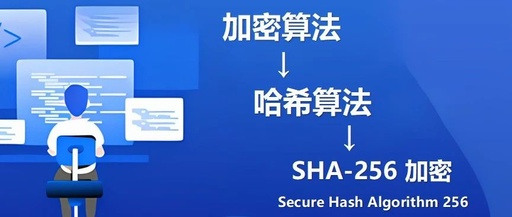
Java Cryptography Architecture: Providing Multiple Encryption Algorithms to Meet Data Encryption and Security Authentication Needs
In Java development, data security is of utmost importance, and the Java Cryptography Architecture acts as a reliable “security guard,” providing various encryption algorithms to ensure data safety. Below, I will guide you through how it meets the needs for data encryption and security authentication. 1. What is the Java Cryptography Architecture? Let’s first discuss … Read more