📢 Latest News On April 2, 2025, Beijing time, the official Go team urgently released Go 1.24.2 and Go 1.23.8, focusing on fixing a critical security vulnerability in the <span><span>net/http</span></span> package—HTTP Request Smuggling (CVE-2025-22871). This vulnerability could allow malicious attackers to bypass security checks, construct illegal requests, and threaten server security.
🚨 Vulnerability Impact Scope
- • All Go servers or proxy servers using
<span><span>net/http</span></span>to handle Chunked Transfer Encoding. - • If the service is deployed behind a reverse proxy (such as Nginx or Apache), it may also be affected by this vulnerability, and proxy configurations should be checked accordingly.
🔍 Vulnerability Details: HTTP Request Smuggling
What is HTTP Request Smuggling? HTTP Request Smuggling is an attack technique where an attacker constructs malformed HTTP requests to exploit differences in how servers and proxies parse requests, bypassing security policies to inject malicious requests, poison caches, or even steal data.
Cause of the Vulnerability In Go’s <span><span>net/http</span></span> package, when processing requests with Chunked Encoding, if the Chunk-Size Line ends with <span><span>\n</span></span> (LF) instead of the standard <span><span>\r\n</span></span> (CRLF), some proxies or servers may misinterpret it, leading to request smuggling.
Example of an Attack A malicious request might look like this:
GET / HTTP/1.1
Transfer-Encoding: chunked
5\n // Illegal chunk line (ends with LF only)
Hello
0\r\n\r Before the Fix: Some servers might incorrectly interpret <span><span>5\n</span></span> as a valid chunk, allowing subsequent data to be exploited by attackers.After the Fix: Go 1.24.2 strictly rejects such requests and returns an error directly.
🛠️ Fix Details: How Does Go 1.24.2 Close the Vulnerability?
This update adds strict <span><span>net/http</span></span> chunk encoding validation logic:
- 1. Enforce CRLF Detection
- • The chunk size line must end with
<span><span>\r\n</span></span>, otherwise an error is returned “chunked line ends with bare LF”.
- • If extra
<span><span>\r</span></span>appears within the chunk line, an error “invalid CR in chunked line” is thrown to prevent attackers from constructing malformed data.
- • Ensure all chunked request parsing complies with HTTP specifications to avoid parsing ambiguities.
Key Logic of the Fix Code (Simplified version):
if bytes.IndexByte(p, '\r') != len(p)-2 {
return errors.New("invalid chunked line")
}
p = p[:len(p)-2] // Remove CRLF, only process valid data 💡 Impact and Recommendations
✅ Scenarios That Must Upgrade:
- • Your Go service is directly exposed to the public, handling user requests.
- • Using
<span><span>net/http</span></span>as an HTTP server or client with Chunked Transfer Encoding enabled.
🔍 How to Check if Affected?
- • Run
<span><span>go version</span></span>, if the version is lower than 1.24.2 or 1.23.8, immediate upgrade is required. - • Use security scanning tools (like Burp Suite) to test if the server allows bare LF chunked requests.
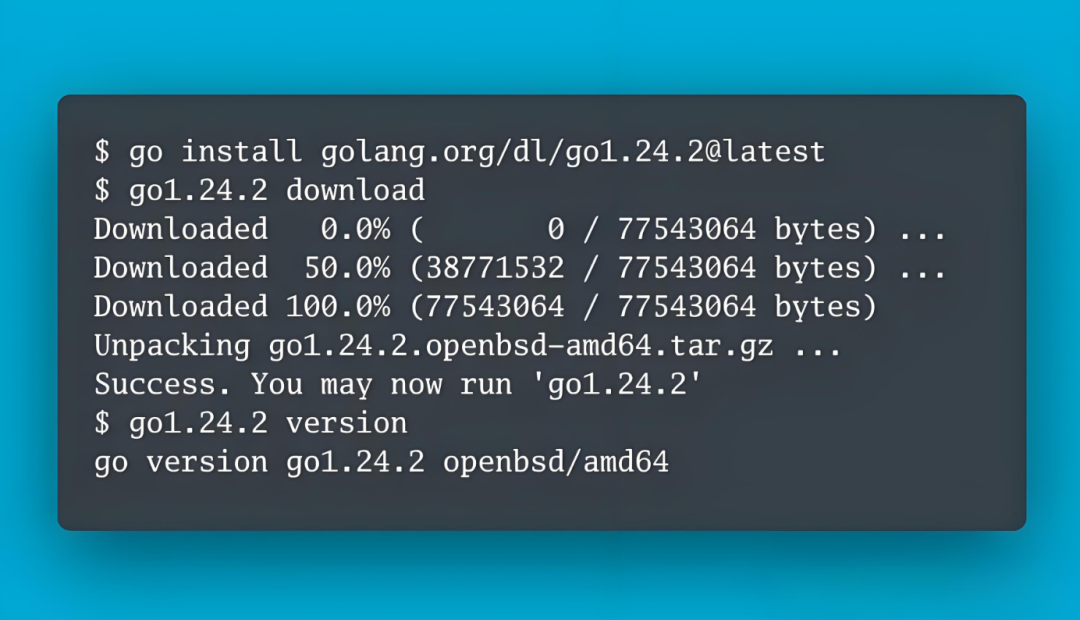
📌 Upgrade Command
go get golang.org/dl/go1.24.2
go1.24.2 download 🚀 Summary
Go 1.24.2 is a critical security update, and all developers should upgrade as soon as possible to avoid being exploited by malicious attackers using the request smuggling vulnerability. If your business relies on HTTP Chunked Transfer Encoding, it is recommended to:
- 1. Immediately upgrade to Go 1.24.2.
- 2. Check reverse proxy configurations, ensuring compliance with RFC standards.
- 3. Monitor for abnormal requests, to prevent potential attacks.
We believe that the Go language and algorithms provide a powerful “interview tool” for ordinary developers and are committed to sharing comprehensive programming knowledge. Here, you can find the latest Go language tutorials, algorithm analyses, tips to enhance interview competitiveness, and industry trends.
Welcome to follow “Fudada Architect Daily Question”, let Go language and algorithms assist your career development.
·