Guide to Diagnosing and Repairing ECU Control Anomalies
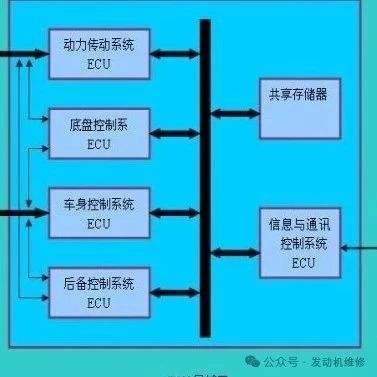
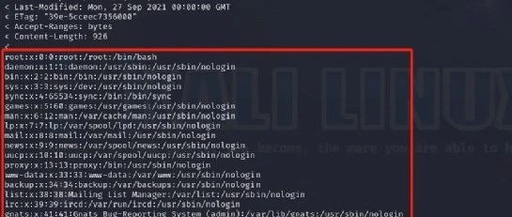
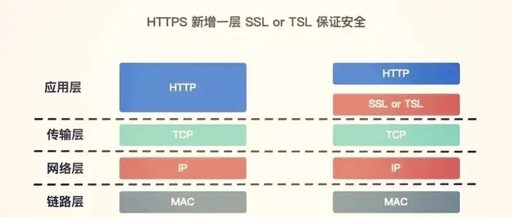
1. Core Fault Analysis of ECU Anomalies 1. Program Corruption: The “Amnesia” of Digital Neurons Typical Triggers: Unofficial ECU tuning (e.g., aggressive first/second-order program flashing leading to checksum failure) CAN bus signal conflicts (devices occupying diagnostic protocol IDs, such as permanent devices on the OBD interface) OTA upgrade interruptions (voltage fluctuations causing packet loss rate … Read more