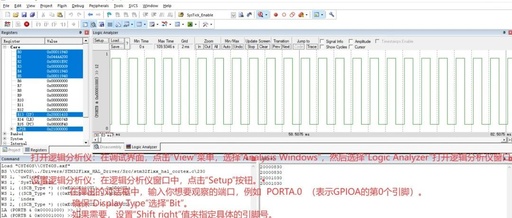
Handcrafted OS Transformation Benchmark Code – Simple Scheduling Algorithm (Part 2)
This article will rewrite the handcrafted OS – a function running the minimum core code of FREERTOS, as shown in the figure below. Mainly: rewriting vTaskSwitchContext + background tick interrupt automatically switches tasks. In fact, the functionality has been completed in two articles, but it seems clumsy to represent using UART. This article aims to … Read more