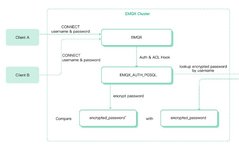
Enterprise-Level Low-Code IoT Platform Overview
Enterprise-level low-code IoT platform The enterprise-level low-code IoT platform is an integrated platform that includes IoT (Internet of Things) device connectivity, data collection, processing, analysis, and visualization capabilities. It aims to help enterprises quickly build and deploy IoT solutions without the need to write extensive code. Below are some key features and advantages of the … Read more