Industrial Control System Information Security
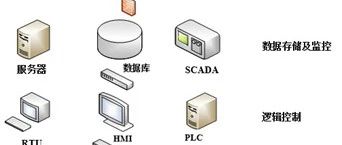
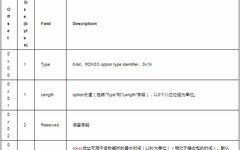
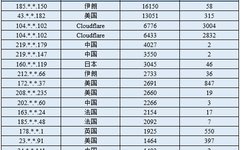
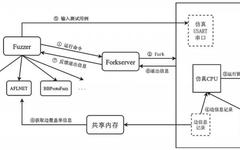
Quoted from: “Intelligent Manufacturing Information Security Technology” (Authors: Qin Zhiguang, Nie Xuyun, Qin Zhen) This book has been published, for details please see the end~ 「 1. Overview of Industrial Control Systems」 Industrial control systems (ICS) refer to a general term for various types of control systems, including monitoring and data acquisition systems and distributed … Read more