Editor’s Note: Currently, the security issues of IoT devices are mainly limited by hardware and software. Often, if the configuration does not keep up, even if developers want to address security issues, they may feel powerless. On the software level, the built-in protection mechanisms of the system are particularly critical, especially permission-based protections. We know that there is a specific class of vulnerabilities used for privilege escalation, which plays an undeniable role in the combination of vulnerabilities. After all, running under system permissions can easily bypass many security policies. Correspondingly, for IoT devices, root permissions have become a battleground for attackers. This topic is presented by Yang Jingyu from Tencent Anti-Virus Lab, who not only analyzed the attack surface of IoT devices from multiple dimensions but also publicly disclosed two vulnerabilities reported to CNNVD as case studies, offering us a feast of IoT security knowledge.
The following content is the transcript of Yang Jingyu’s speech, organized by Kanxue Academy (WeChat public account: ikanxue).

Yang Jingyu
Yang Jingyu (Jingle) graduated from University College London with a master’s degree in Information Security and currently works at Tencent Anti-Virus Lab, focusing on malicious code research. The open-source version of Tencent Hubble Analysis System has been included in the BlackHat arsenal. He is passionate about research in IoT security and virus analysis.

Introduction
2017 was a year of rapid development for IoT, as well as a year marked by the outbreak of security issues related to IoT. In this era of both opportunities and challenges, we need to proactively face the unknown world. Today, I bring you a technical sharing regarding the root permissions of IoT devices. The ‘God Mode’ in the title refers to the state after obtaining root permissions on the IoT system, as entering root mode allows many protective mechanisms to be bypassed, enabling the activation of previously disabled functions and gaining supreme permissions, hence the term ‘God Mode’ for root mode.
1. Overview
1.1 Author Introduction
First, let me introduce myself. My name is Jingle, I hold a master’s degree in Information Security from University College London, and I completed my undergraduate studies in Computer Science at Beijing Normal University. I currently work at Tencent Anti-Virus Lab, specializing in security research. The open-source version of Tencent Hubble Analysis System (HaboMalHunter) has been included in the BlackHat arsenal. I am very passionate about security technology and hope to exchange and learn with everyone.
1.2 Topic Outline
Next, let me introduce the outline of this topic. The scope of IoT security is very broad, involving both technical and non-technical aspects, but today we will focus on the technical side, concentrating on discussing security issues related to root IoT devices. This includes common methods to root IoT devices, security threats after obtaining root permissions, and corresponding mitigation measures.
Additionally, it should be noted that the vulnerability cases introduced in this topic have all been reported to CNNVD and confirmed. Since we only care about the technology, we have omitted the names of the relevant manufacturers.
1.3 Background Introduction
Since IoT security is a new emerging field of research, I will first briefly introduce some relevant background knowledge.
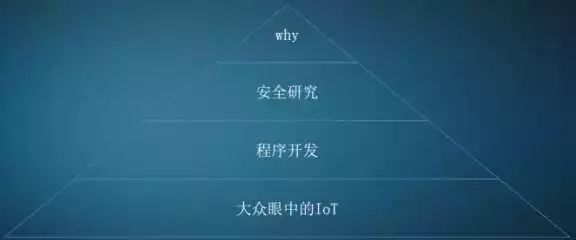
-
IoT in the Public Eye

To the public, IoT means the interconnection of all things, making life more convenient. For example, smart switches break the spatial limitations between people and household appliances. For instance, through automatic timing, the electric heater will automatically start before I get off work, so when I get home, the whole house is warm. When it’s time for work during the day, the electric heater will automatically turn off, alleviating concerns about leaving the house unattended and the risk of fire. From this example, it is clear that security is a significant concern; people worry about electrical safety and privacy when using cameras, which are directions we as security researchers should consider for improvement.
-
IoT from a Programmer’s Perspective
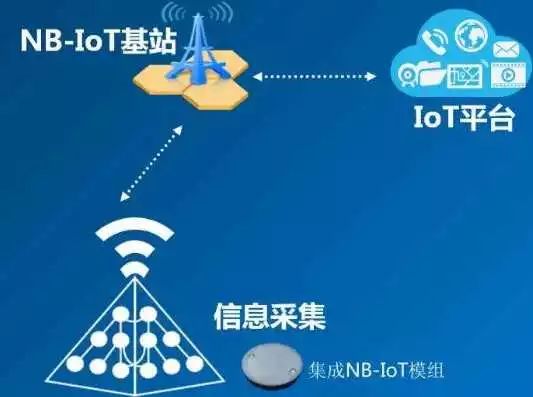
Most of you present are technical professionals, so let’s shift our perspective to see what IoT looks like from a programmer’s viewpoint. To programmers, IoT devices are embedded devices with networking capabilities. An embedded device primarily consists of an embedded CPU, usually ARM or MIPS, hardware peripherals such as memory, USB, network cards, and sensors, along with an embedded operating system, mostly Linux. The networking capabilities mainly involve communication protocols such as Wi-Fi, Bluetooth, 3G, and the latest NB-IoT protocol.
These devices first collect information through sensors, such as temperature, humidity, images, and sounds. Then, they upload this information to cloud servers via communication protocols. The cloud server records, organizes, and mines the data, then feeds the results back to the user. At the same time, these IoT devices can also receive instructions from users and servers, executing corresponding actions such as switching circuits or moving cameras.
-
IoT from a Security Researcher’s Perspective

Next, let’s discuss IoT from a security researcher’s perspective. The first impression is that it’s a gold mine, as there are bound to be vulnerabilities to exploit. What are the reasons for the current state of IoT security? First, IoT technology is currently in a phase of rapid development, and the pace of building security infrastructure has not kept up, resulting in a reactive state of discovering and patching vulnerabilities.
Secondly, due to the limited computational resources of IoT devices, it is challenging to port existing security mechanisms to IoT. For example, a household camera with 64MB of RAM and 32MB of ROM flash makes it difficult to implant mature network security services like IDS, IPS, and firewalls, as even a rule library can exceed the entire memory capacity.
Today, we will focus on a very important aspect of IoT security, the security issues related to root access. Here, I want us to think together about the most critical question of this sharing:
Why Root?
First, users have the need to root IoT devices to break limitations; for instance, many users flash the firmware of brand routers to replace it with OpenWRT.
Secondly, developers have needs, such as analyzing the functionalities of competing products. The most significant demand comes from security researchers who need to obtain system root permissions to better study IoT devices. This includes extracting firmware for static analysis and obtaining system runtime parameters, such as Linux partition information and boot parameters, and even directly debugging on the device. All of this aims to discover vulnerabilities earlier and make IoT devices more secure.
Finally, the strongest demand comes from black markets, driven by profit motives. After gaining root permissions, it becomes easier to conduct traffic manipulation, exploit vulnerabilities, launch DDoS attacks, and mine cryptocurrencies. As security researchers, we are in a constant race against black market actors, striving to discover vulnerabilities before attackers do, to provide a safer environment for everyone.
2. Rooting Methods
Next, let’s discuss methods to root IoT devices. First, we need to model attacks on IoT devices, then analyze each attack surface, and finally identify weak points from these attack surfaces.

As shown in the figure, an IoT device model can be divided into four major attack surfaces: hardware layer, network layer, system layer, and application layer. Any minor vulnerability within these attack surfaces could potentially become a key point for obtaining root permissions.
-
Hardware Layer
First, let’s look at the hardware layer. The security of the hardware layer is actually the most significant difference between IoT security and traditional software security or web security. In traditional security concepts, hardware security issues receive relatively low attention, and vulnerabilities that emerge typically score low. In fact, some vulnerability submission requirements explicitly state that non-physical contact is necessary for remote attacks.
However, IoT security is different from traditional security; physical layer security is crucial. Regardless of how root permissions are obtained, the resulting security threats are substantial.
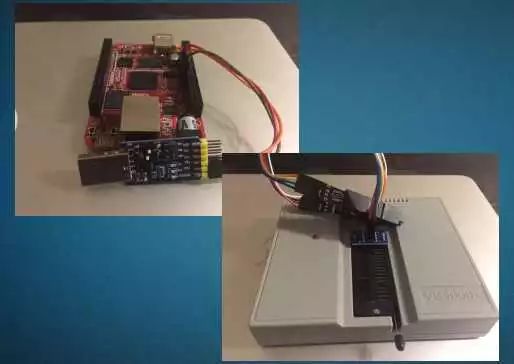
For physical layer attacks, I will mainly introduce two methods today: the first is UART debugging, and the second is using an SPI flash programmer.
For UART debugging, this is a very direct method to obtain root permissions on IoT devices. You only need to find some keywords on the circuit board, such as VCC, 3.3V, GND, RX, TX, or even directly labeled UART interfaces. Then, use a multimeter to measure the voltage during the boot phase, identify the ground and VCC, and try RX and TX; usually, you can determine the serial port interface. Then, by connecting to the serial port with a remote terminal, you can directly obtain a Linux shell, and in most cases, the user is root.
UART debugging can provide very important runtime parameters, such as the MTD partition table and Linux system boot parameters. After obtaining root permissions, you can read the /dev/mtdN device file to extract the ROM data of the IoT device, which contains essential firmware data.
As for the SPI flash programmer, those familiar with embedded development will be very familiar with it. The SPI flash programmer, in conjunction with the chip clip, bypasses the CPU and directly reads and writes to the NOR flash of the IoT device. At this point, the device has not started, so any software-level security measures cannot prevent reading and writing firmware through the programmer.
In my actual research, I have successfully read and written firmware for about 20 IoT devices; only one SOP16 NOR flash chip could only be read, and writing caused garbled data, rendering the device bricked. The firmware dumped through the programmer can be used for subsequent static analysis to find root methods.
Here’s a friendly reminder: Both hardware-based attack methods may damage the device, especially when flashing firmware. Fortunately, most IoT devices are relatively inexpensive, so I have not gone bankrupt yet.
-
Network Layer
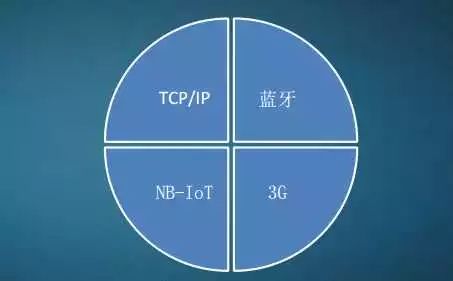
Next, let’s shift our attention to the network layer. This layer encompasses both traditional security and unique aspects of IoT security.
First, most IoT devices use Wi-Fi, while some use wired networks. For these TCP/IP-based devices, traditional penetration testing techniques can still discover numerous vulnerabilities.
Moreover, IoT devices do not only use TCP/IP. They also involve wireless protocols such as Bluetooth, 3G, and NB-IoT. Each new feature and protocol tends to expose some security issues. There is ample opportunity for exploration here, such as the Bluetooth vulnerability Blueborne that emerged this year.
-
System Layer
Next, let’s look at the security issues at the system layer. Most IoT devices are embedded devices running Linux. Vulnerabilities that occur in the Linux system are inherited by IoT devices. For example, vulnerabilities like shellshock and dirtycow can be exploited by malicious software to attack IoT devices and gain root permissions. Additionally, some design flaws in the system can lead to serious consequences.
Here, I would like to share a vulnerability submitted by Tencent Anti-Virus Lab to CNNVD.
This vulnerability is quite easy to understand, but since the product has already been released and there are multiple versions, the cost and difficulty of modification are predictably high.
-
Application Layer
Finally, let’s focus on the security of the application layer. The application layer carries a diverse array of requirements, and each IoT function is unique, making it challenging to have common attack methods. Mastering reverse engineering and dynamic debugging techniques for ARM and MIPS is essential for better discovering vulnerabilities at the application layer. Here, I will introduce another vulnerability reported by Tencent Anti-Virus Lab to CNNVD to illustrate the security analysis methods for the application layer.
Thus, we find that all four major aspects of IoT—physical layer, network layer, system layer, and application layer—have security issues that could lead to attackers gaining root permissions. Now, let’s think together about the severe security threats that could arise when an attacker gains root permissions on an IoT device.
3. Security Threats
From the perspective of a Linux programmer, gaining root permissions equates to obtaining supreme power, which is the origin of the term ‘God Mode’ in this sharing. Simply put, if an attacker launches a remote attack and gains root permissions on an IoT device, they can do anything on the software level, except take the physical device.
Compared to traditional Linux security, the threats faced by IoT security are significantly greater.
First, due to the limited computational capabilities of IoT devices, they cannot withstand some previously common network attacks, let alone 0-day attacks, leading to a surge of worms targeting IoT devices in recent years.
Secondly, the unique usage scenarios of IoT lead to firmware updates being a costly operation. Many users do not actively update firmware, which means that even if manufacturers have patched vulnerabilities, IoT devices remain vulnerable to known exploits due to users not updating in a timely manner.
Finally, because IoT devices operate continuously 24/7 and are connected to the internet in real-time, even possessing recording and video capabilities, once an IoT device is controlled by an attacker, it can continuously engage in malicious activities.

These malicious activities include traditional DDoS attacks, using IoT devices as bots to launch network attacks against target websites, leading to website outages.

Secondly, there is the increasingly popular mining activity, as IoT devices generally do not lose power, and the electricity cost is borne by the attackers. Even if the CPU computing power is limited, if scaled, it becomes a favored malicious activity for attackers.
Finally, do not overlook the new threats posed by IoT devices being attacked within internal networks. Traditional security defenses focus on perimeter defenses between external and internal networks, deploying numerous firewalls, IDS, and IPS to keep enemies at bay. However, they often fail to consider that even with a strong perimeter, once IoT devices inside the network are compromised, attackers can launch attacks from within the network to compromise other devices on the same subnet.
I would like to share another interesting vulnerability submitted to CNNVD.
4. Mitigation Measures

Having discussed the security threats posed by rooting IoT devices, let’s now talk about corresponding mitigation measures. Currently, IoT security is in a state of ‘attack strong, defense weak’, largely because existing mitigation measures are not well-utilized. These methods are often overlooked or cannot be adapted to IoT devices due to performance issues. Today, I will not elaborate too much but will propose some targeted solutions to mitigate the vulnerabilities mentioned earlier.
First, regarding firmware verification, I recommend using digital signature technology. Sign the firmware when releasing it, and during upgrades and subsequent runs, perform signature verification. This resolves the issue of CRC being replaced by attackers. TI provides an RSA-based firmware digital signature solution that everyone can explore further.
Secondly, concerning password generation, generating random passwords is feasible, but the random seed needs to be particularly well-protected to prevent attackers from obtaining it.
Finally, for vulnerabilities related to the Wi-Fi functionality that can be exploited, it is best to impose physical restrictions on IoT capabilities or directly purchase suitable hardware to avoid such issues.
5. Conclusion
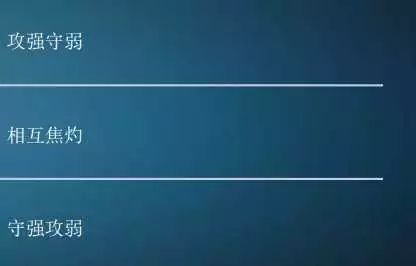
I am very fortunate to share with you today on the topic of IoT root permissions and related security issues. I wonder if you have experienced this: The development of IoT security also follows a natural law, which is a pattern of ‘attack strong, defense weak’ in the early stages, ‘stalemate’ in the middle stage, and ‘defense strong, attack weak’ in the later stages.
This pattern has appeared multiple times throughout the history of internet development, such as the evolution of Windows security from Windows 2000 and XP, which served as a training ground for software security, to the current Windows 10 where every vulnerability is highly valuable. Similarly, web security has evolved from XSS and SQL injection, which often led to entire site data breaches, to the point where WAFs are now standard.
Currently, IoT security is still in a phase where attackers are very strong, but with the frequent emergence of IoT security incidents and the increasing security awareness among IoT manufacturers, we will soon enter a stalemate phase. Ultimately, with the enforcement of policies and regulations and the efforts of information security professionals, IoT will develop towards being safer and more reliable. Thank you very much.
6. References
1. https://www.armis.com/blueborne/
2. https://wikidevi.com/wiki/Ralink_RT5350
3. http://processors.wiki.ti.com/index.php/Basic_Secure_Boot_for_OMAP-L138_C6748
4. http://www.cnnvd.org.cn/web/xxk/ldxqById.tag?CNNVD=CNNVD-201708-1472
If you want to obtain the PPT of this speech,
click the link to read the original article to view and download!
Review of Kanxue Security Developer Summit:
-
[Shocking Arrival Tomorrow!] The 2017 Kanxue Security Developer Summit, we finally waited for you!
-
The 2017 Kanxue Security Developer Summit concluded successfully!
-
[Kanxue 2017 Security Developer Summit Speech Review 0x1] How to Hack Drones
-
Customized Countermeasures – Security Practices Against Game Cheating (Kanxue 2017 Security Developer Summit Speech Review 0x2)
-
Analysis of WEB Security Programming (Kanxue 2017 Security Developer Summit Speech Review 0x3)
-
Trends in Business Security Development and Challenges to Security R&D (Kanxue 2017 Security Developer Summit Speech Review 0x4)
-
The Downfall of Flash: The End of the Vulnerability King Flash Player
-
Intelligent Security: Devices & Applications & ICS (Kanxue 2017 Security Developer Summit Speech Review 0x6)