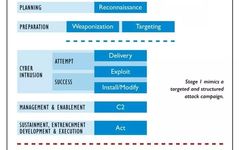
The ICS Cyber Kill Chain
The ICS Cyber Kill Chain The ICS Cyber Kill Chain is a report written by Michael J. Assante and Robert M. Lee of the SANS Institute, published in 2015. This report describes the specific processes attackers use to target ICS and abstracts these processes into the ICS Cyber Kill Chain. The report outlines two phases … Read more