With the rapid development of the Internet of Things (IoT), the number of devices has increased exponentially, leading to growing concerns about IoT security. Typically, integrity certification of IoT devices is achieved through software proof methods to timely detect system integrity tampering caused by malicious software execution within devices. However, existing IoT software proof methods face challenges such as low performance in synchronizing proofs for massive devices and difficulties in extending general IoT communication protocols. To address these issues, a lightweight asynchronous integrity monitoring solution is proposed, which extends software proof security certification messages over the general MQTT protocol, asynchronously pushing device integrity information, ensuring high security of the IoT system while improving the efficiency of device integrity proof verification. The proposed solution implements three main security functionalities: achieving device integrity measurement through a kernel module, lightweight authentication extension for device identity and integrity based on MQTT, and asynchronous integrity monitoring based on the MQTT extended protocol. The proposed solution can resist common software proof and MQTT protocol attacks, featuring lightweight asynchronous software proof and general MQTT security extensions. Finally, experimental results based on the MQTT IoT authentication prototype system show that the integrity measurement of IoT nodes, MQTT protocol connection authentication, and PUBLISH message authentication perform well, meeting the application needs for monitoring the integrity of massive IoT devices.

Scan the QR code to read the full article
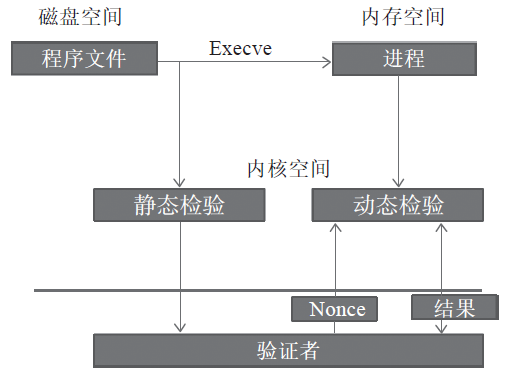
Figure 1 Device Measurement Process
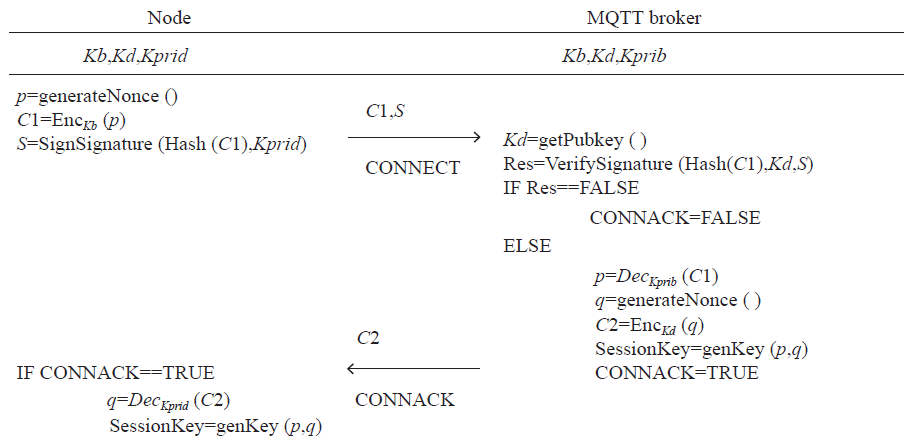
Figure 2 Identity Authentication Process
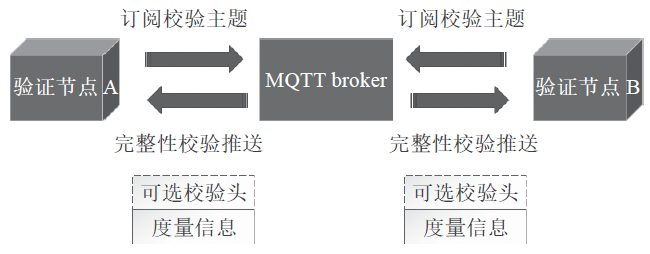
Figure 3 Verification Node Validation Process
(2) Experimental Results and Analysis
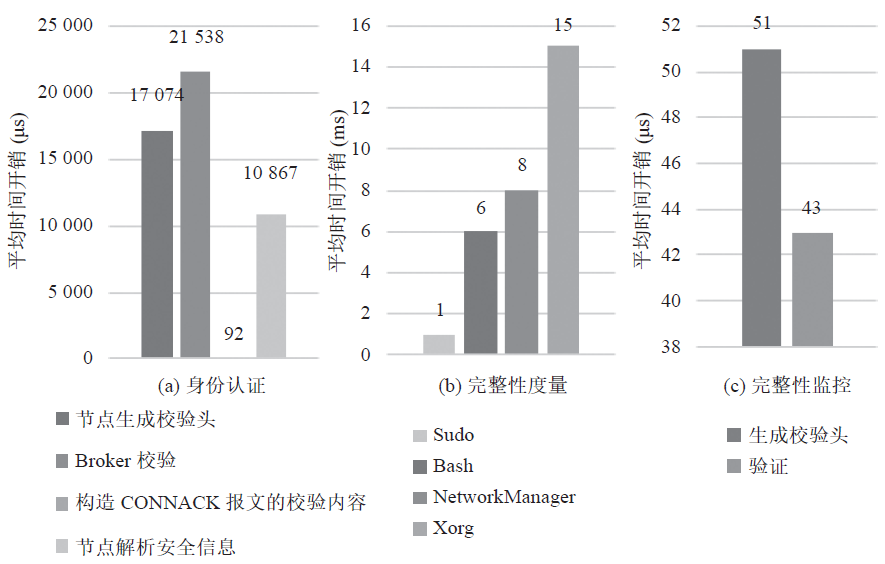
Figure 4 Performance Overhead
For the integrity measurement of processes within the system, the results are shown in Table 1. Tests were conducted 1,000 times on programs of different sizes, taking four examples: sudo with a size of 149,128 bytes, bash with 964,220 bytes, and Xorg with an average measurement overhead of 2,271,600 bytes, as shown in Figure 4(b).
Table 1 Integrity Measurement Results

After establishing a connection with the MQTT broker, the device node pushes the PUBLISH message to the broker. The PUBLISH message includes a verification header based on the measured content and uses the session key agreed upon in the CONNECT phase for MAC verification. The device node performs an SM4 hash calculation on the measurement content and uses the session key to generate the MAC authentication code. The broker receives the PUBLISH message, performs the same MAC authentication code calculation on the measurement content, and compares it with the verification header content in the message to confirm that the measurement content comes from a legitimate node. The measurement results are shown in Figure 4(c).
(3) Conclusion
This scheme extends the identity and integrity proof of IoT devices based on the general MQTT protocol, achieving lightweight IoT device software proof functionality. The system-level integrity measurement is provided through a kernel module measurement method in the device node system, and a lightweight integrity monitoring protocol is designed and implemented relying on the security extension of the MQTT protocol. This scheme features lightweight asynchronous software proof and general MQTT security extensions. It can effectively respond to the remote proof application needs of massive IoT devices, reducing synchronization proof overhead and verification node computational overhead, avoiding the impact of concurrent proof requests from multiple verification nodes on device availability, and facilitating dynamic adjustments and upgrades of IoT networks.