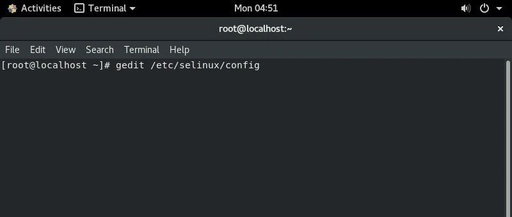
Installing Nginx on Rocky Linux 9
Installing Nginx on Rocky Linux 9 Hello everyone, I am Xing Ge. Nginx has become one of the mainstream choices for web service deployment due to its high performance, low resource consumption, and excellent reverse proxy capabilities. This article will guide you through the process of installing and configuring the Nginx service from scratch on … Read more