MIPS Stack Overflow: ROP Construction and Shellcode Injection
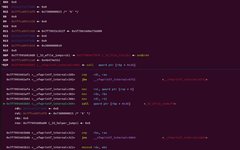
0. Introduction Recently, I wrote about the DVRF series topics, and I still feel a bit overwhelmed by the construction of ROP, so I decided to delve deeper into how to construct ROP chains during the May Day holiday. Note: The entire process should be replicated using Ubuntu 16.04. Do not use 18.04 or 20.04, … Read more