1. Introduction
1. Introduction
MQTT, which stands for Message Queuing Telemetry Transport, is an ISO standard (ISO/IEC PRF 20922) based on the publish/subscribe paradigm. It was released by IBM. Due to its lightweight, simple, open, and easy-to-implement characteristics, it is very suitable for IoT scenarios that require low power consumption and limited network bandwidth, such as remote sensing data, automotive, smart homes, smart cities, and healthcare.
2. MQTT Protocol
2. MQTT Protocol
The MQTT protocol is designed for environments with limited computing power, low bandwidth, and unreliable networks. Its applications are very broad. Currently, there are many supported server programs, and languages such as PHP, JAVA, Python, C, C# can send related messages to MQTT.
The latest version is 5.0, which can be found at
https://github.com/mqtt/mqtt.github.io/wiki/servers, where server software supporting MQTT is listed. The collaboration and application for automotive manufacturers mentioned in HiveMQ shows that the automotive industry has applied the MQTT protocol.

Here are a few points of interest:
1. Uses a publish/subscribe messaging pattern, supporting one-to-many message publishing;
2. Messages are transmitted via the TCP/IP protocol;
3. Simple packet format;
4. The default port is TCP 1883, WebSocket port 8083, and default messages are not encrypted. Port 8883 is the default for the MQTT protocol encrypted via TLS.
3. Publish/Subscribe Model
3. Publish/Subscribe Model
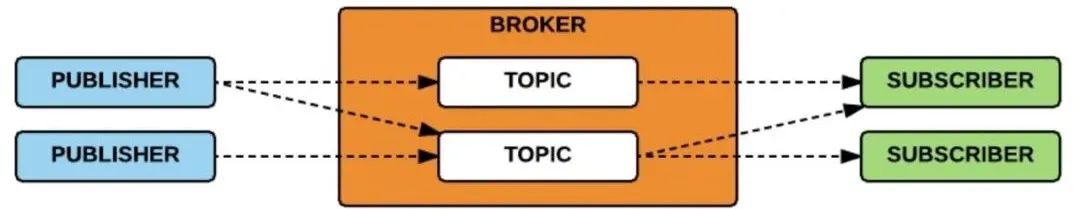
In the MQTT protocol, there are three roles and one main concept. The three roles are Publisher, Subscriber, and Broker, with the main concept being Topic.
The sender of the message is called the Publisher, while the receiver is called the Subscriber. Both the sender and subscriber connect to the Broker to publish or subscribe to messages. The Broker generally serves as the server, and the container storing messages is the Topic. The Publisher sends messages to the Topic, and the Subscriber must first “subscribe to the Topic” before receiving messages. In each subscription, the Subscriber can receive all messages from the Topic.
The flowchart of the MQTT protocol is as follows:
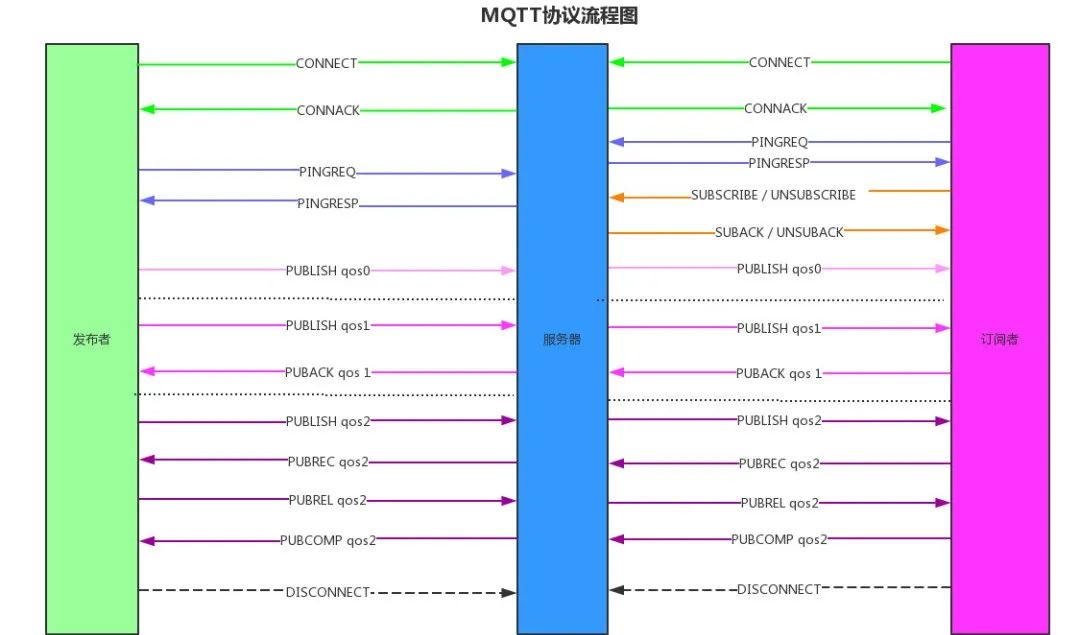
This article does not go into too much detail about the protocol; those interested can refer to the citations at the end.
4. MQTT Attack Points
4. MQTT Attack Points
Based on its characteristics, the following attack points can be expanded:
1. Authorization: Anonymous connection issues; anonymous access means anyone can publish or subscribe to messages. If sensitive data or commands are present, it could lead to information leakage or malicious commands from attackers;
2. Transmission: Default unencrypted messages can be subjected to man-in-the-middle attacks, allowing retrieval of verified usernames and passwords;
3. Authentication: Weak password issues; weak passwords can be brute-forced, posing security risks;
4. Application: Plaintext configuration on the subscriber side can lead to leakage of verified usernames and passwords;
5. Vulnerabilities: Defects in the server software can be exploited, or improper parsing of content on the subscriber or server side can create security vulnerabilities, affecting the entire system.
Utilization of MQTT
There are currently open-source tools targeting MQTT, primarily focusing on mqtt-pwn. This tool is powerful and easy to use. The GitHub address is
https://github.com/akamai-threat-research/mqtt-pwn, and the documentation can be found at
https://mqtt-pwn.readthedocs.io/en/latest/.
Tool Installation
Installing mqtt-pwn is straightforward. It can be installed directly on the local machine or used via Docker. The text will use the Docker method. First, ensure that Docker and Docker Compose are installed, then run the following commands for installation:
git clone https://github.com/akamai-threat-research/mqtt-pwn.git
cd mqtt-pwn
docker-compose up –build –detach
Run:
docker-compose ps
docker-compose run cli
Then you will see the mqtt-pwn interface.

MQTT Anonymous Access
Use the connect command of mqtt-pwn to connect. connect -h displays help information; other commands function similarly. When using, refer to the help and documentation to quickly familiarize yourself. For services with anonymous access, simply use connect -o host; this command also supports entering usernames and passwords. If no connection exception is displayed, it indicates a successful connection. After a successful connection, you can use system_info to view system information.
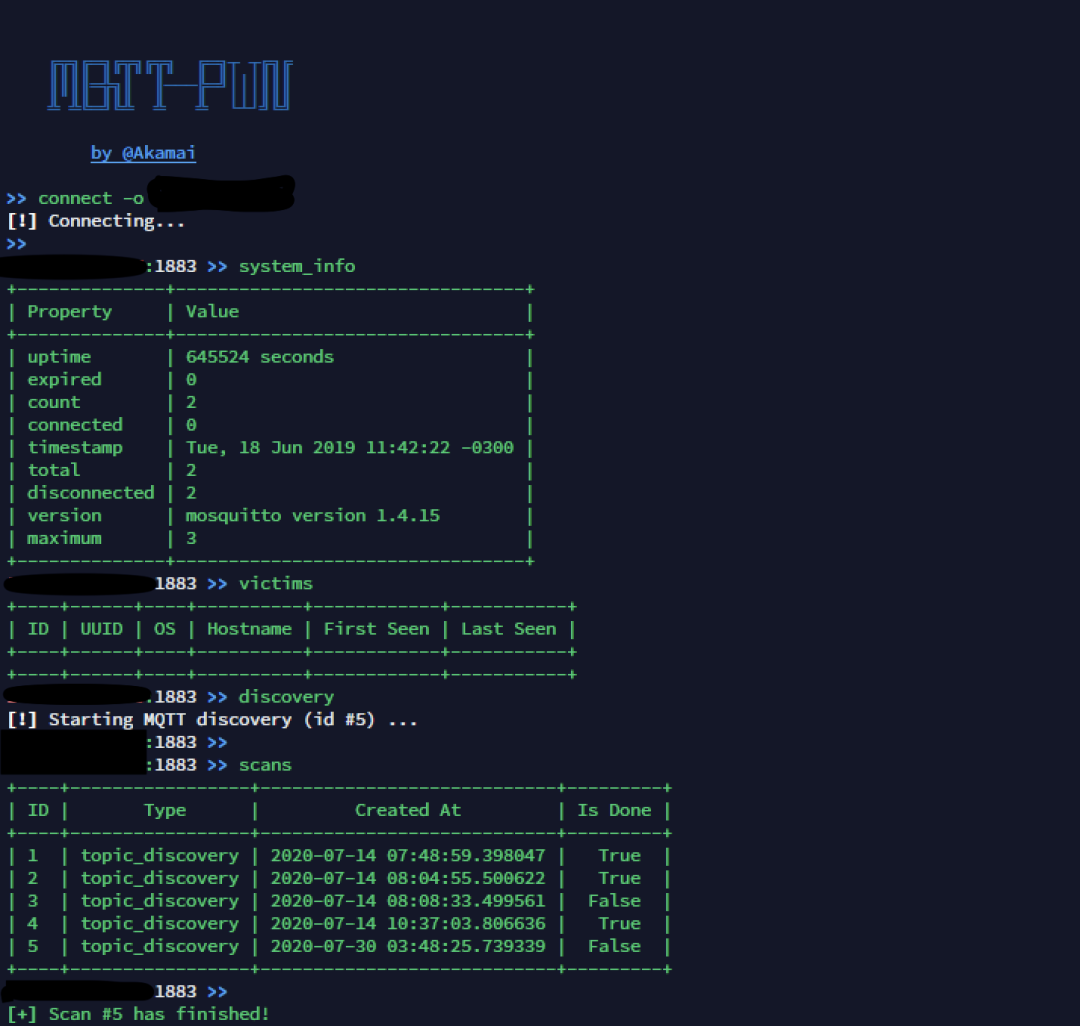
Next, you can check the topic information and other content. First, execute discovery and wait for “scan #1 has finished” to display. Then execute scans -i followed by the serial number, and then execute the topics command to see the topic information. The discovery command can use the -t parameter to set the timeout. The topics command can use the -l parameter to set the number of entries to view.
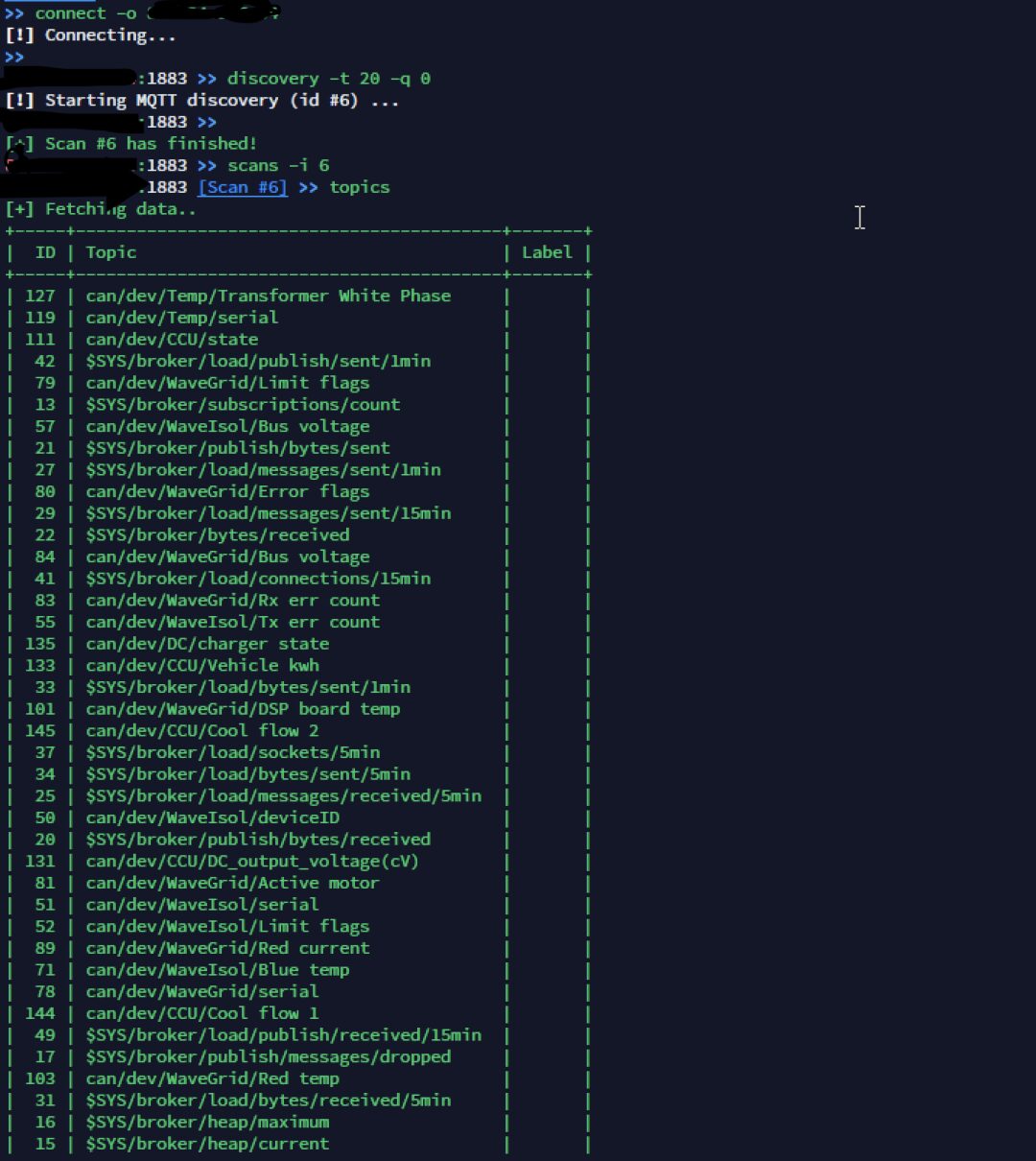
You can enter messages to view the content of the topic. Use -l to limit the number of entries, and -i to view the content of a specific message.
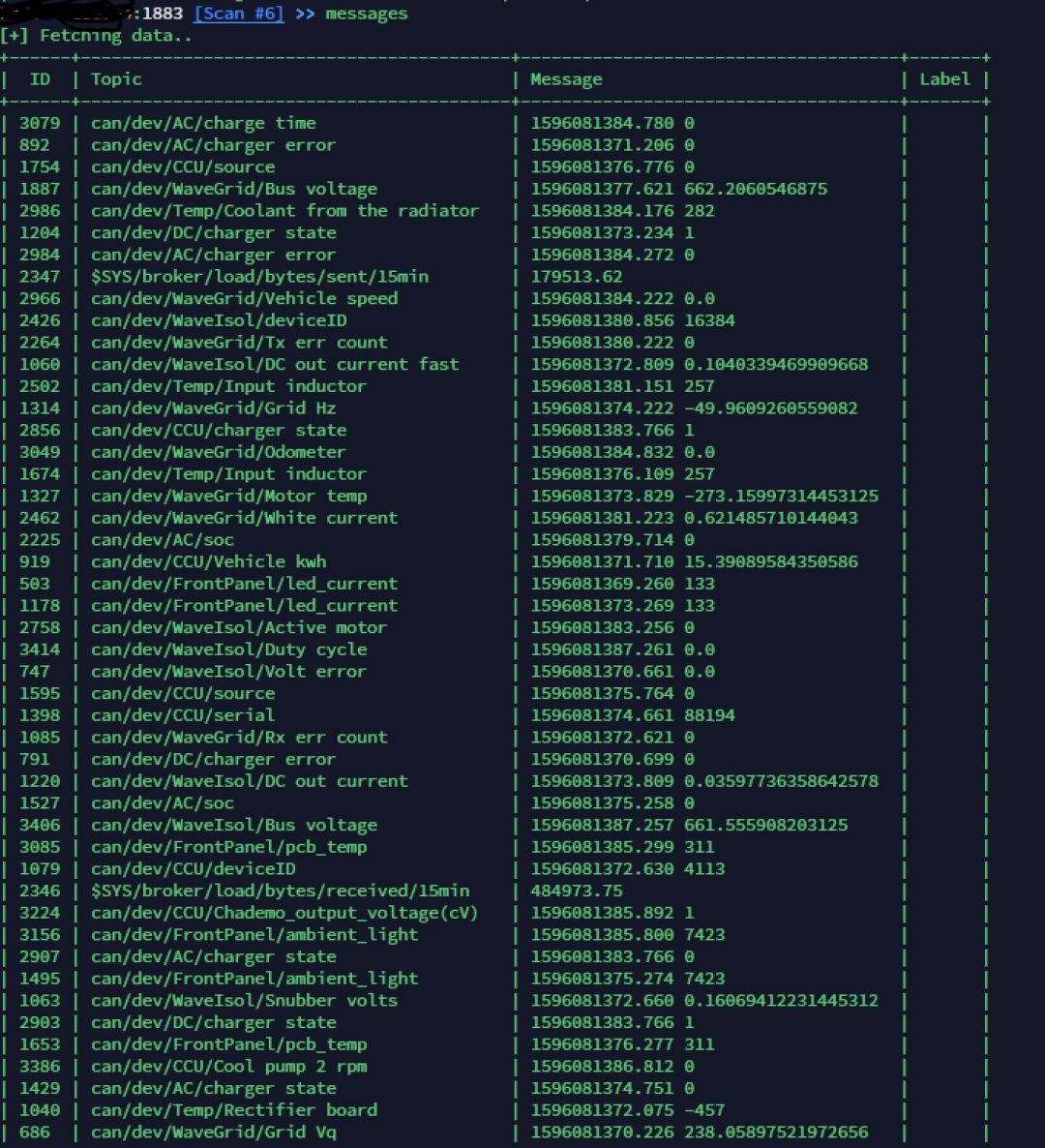
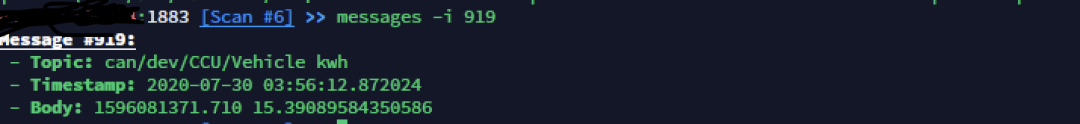
MQTT Username and Password Brute Force
Metasploit includes a brute force module for MQTT, but actual tests have shown that the effectiveness is not ideal. Here, we will continue to introduce mqtt-pwn. mqtt-pwn has a brute force function and comes with a simple dictionary to brute force MQTT usernames and passwords.
bruteforce –host host –port -uf user_dic -pf pass_dic
The default port is 1883, and the user and password dictionaries are located in the mqtt-pwn’s resources/wordlists folder.
For example, execute bruteforce –host 127.0.0.1 for brute forcing. After a successful brute force, you can use the obtained information to connect and operate, adding the username and password options when connecting.
mqtt-pwn also supports more features, such as Owntracks (GPS Tracker), Sonoff Exploiter, etc. Interested parties can refer to the documentation for testing.
Discoveries in Applications
In actual usage scenarios, we can capture verification information from traffic through man-in-the-middle hijacking. Below is the content captured by Wireshark.
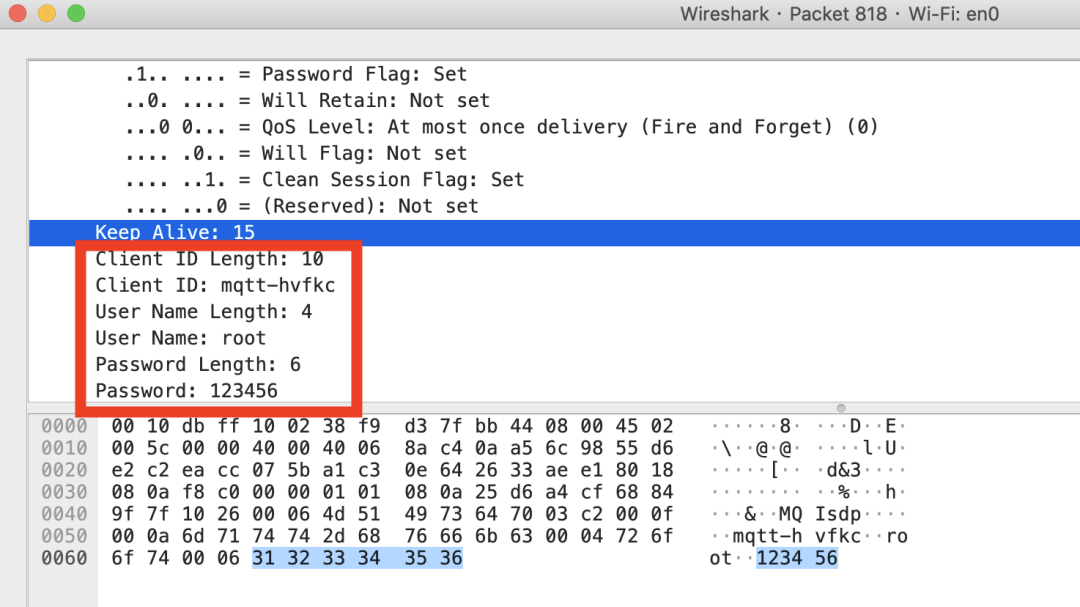
In addition, since various languages have implemented MQTT clients, web applications also have WebSocket MQTT. This allows verification information to be obtained through web source code or network requests.
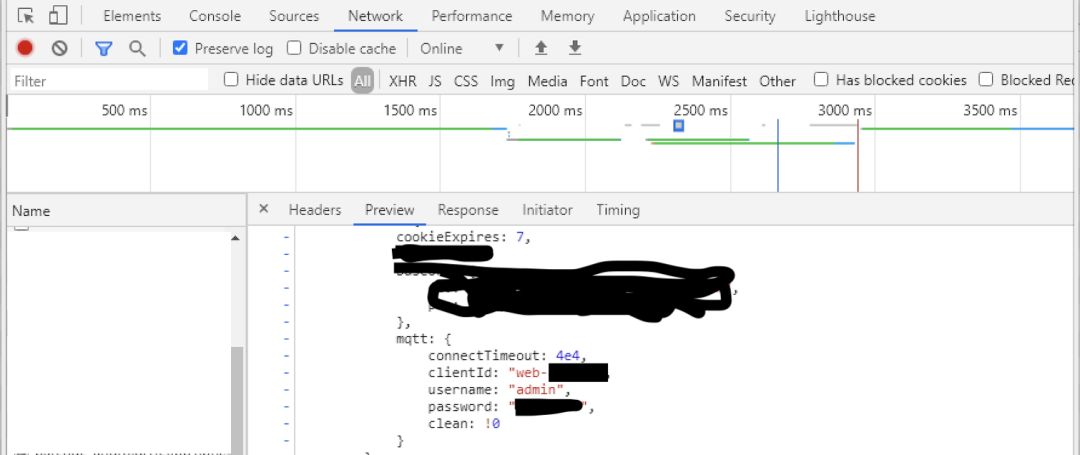
Server Vulnerabilities
Here are some historical MQTT vulnerabilities for reference.
CVE-2017-7296
CVE-2017-7650
CVE-2018-17614
CVE-2019-5432
CVE-2020-13849
Mosquitto Vulnerability List
5. Detection and Discovery
5. Detection and Discovery
The powerful nmap supports MQTT protocol recognition and can directly identify the MQTT protocol through nmap. Additionally, besides the default ports mentioned above, some administrators may modify the default ports, so you can also try nearby ports like 1884, 8084, 8884 for quick detection, or add numbers in front as combinations. If targeting a single target, you can scan all ports. For large-scale scans or increased scanning efficiency, advanced port scanning tools like masscan, zmap, RustScan can be used, along with nmap for protocol recognition. An example command for nmap is as follows:
sudo nmap -p1883,8083,8883 -sS -sV –version-intensity 9 -Pn –open target_ip
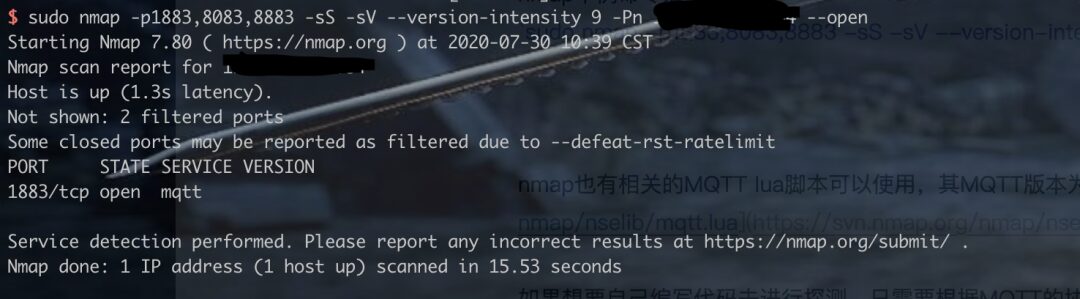
nmap also has related MQTT lua scripts available for use, with the MQTT version being 3.1.1. The script can be found at
https://svn.nmap.org/nmap/nselib/mqtt.lua.
If you want to write your own code for detection, you just need to send and receive messages via socket according to the MQTT protocol standards. For detailed information about the MQTT protocol, you can refer to the documentation at https://docs.oasis-open.org/mqtt/mqtt/.
Existing network space mapping platforms have basically implemented MQTT detection. You can directly use these search engines to obtain a large number of services using the MQTT protocol.
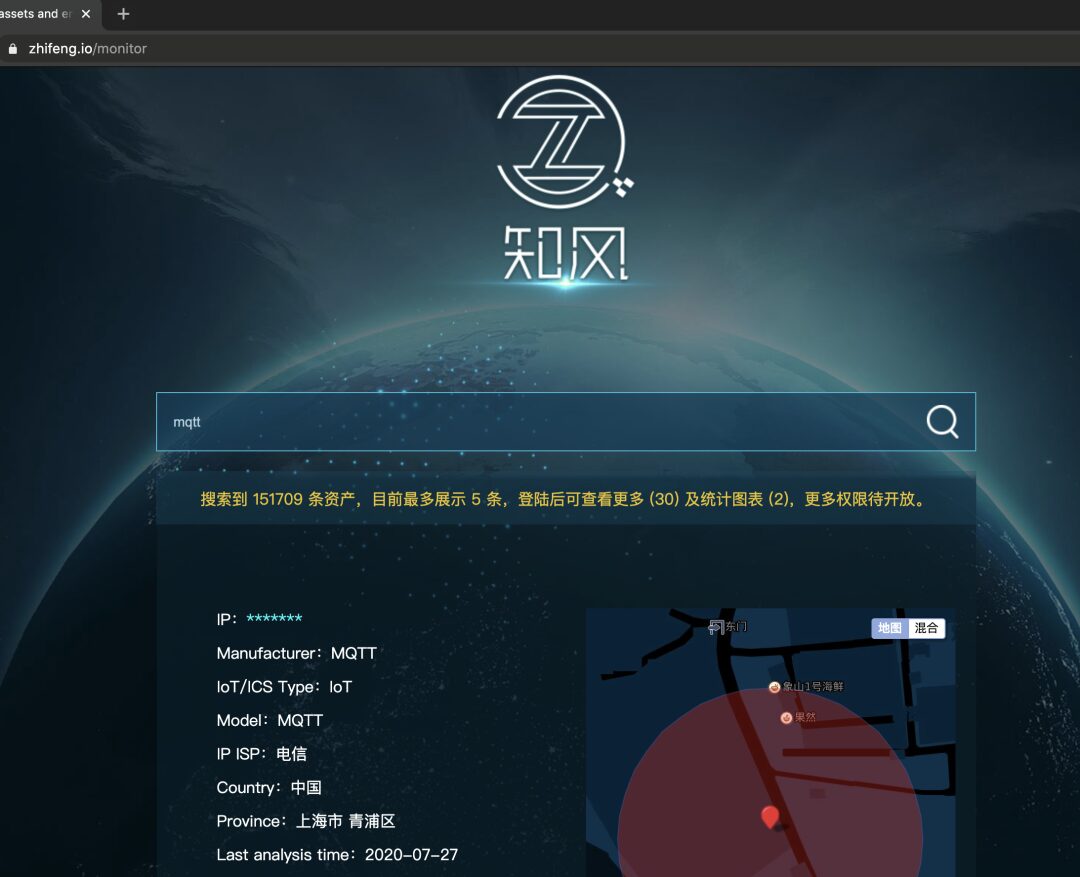
· Zhifeng
In the Zhifeng search engine targeting IoT and ICS detection, searching for the keyword mqtt reveals 150,000 open services.
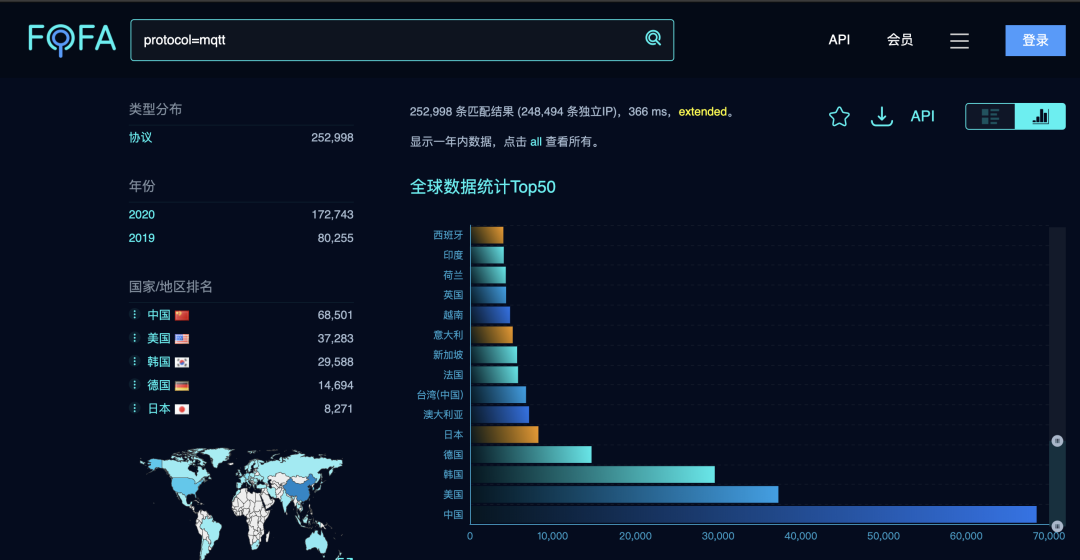
· Fofa
The search keyword is protocol=mqtt, with 250,000 open services detected in the past year.
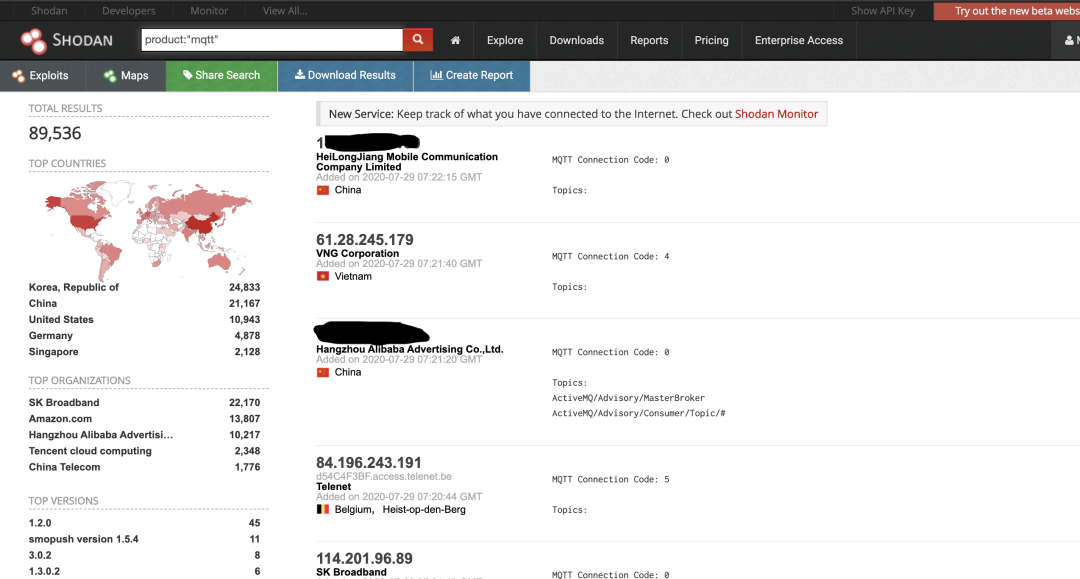
Search keywords:
product:”MQTT”
product:”Mosquitto”
There are over 110,000 open services detected on Shodan.
From the above search results, each engine has its strengths and weaknesses. Both Shodan and Zhifeng will list topics in their detection of this protocol, while Fofa has the most discoveries but only identifies the protocol without listing topics. Additionally, the Zhifeng system has high geographic positioning accuracy, capable of locating within a hundred-meter range.
6. MQTT Security Recommendations
6. MQTT Security Recommendations
1. Do not enable anonymous access; set authentication on the server (BROKER) and increase username and password verification.
2. Prioritize encrypted data transmission based on actual conditions to prevent man-in-the-middle attacks.
3. Encrypt payloads before secure transmission.
4. Use the latest server programs to set up services.
5. Do not upload implemented code to public platforms such as GitHub.
7. Conclusion
7. Conclusion
When writing this article, there were not many articles on MQTT security available online. However, through understanding, there are still many contents to explore, such as MQTT gateways in industry, numerous server software supporting MQTT, and its wide range of applications. This article briefly introduces MQTT security content, and there is much more to explore. Interested friends are welcome to communicate and discuss more.
Finally, I remind everyone to set up services for learning during the study and research process. Please do not conduct testing, destruction, or other activities on targets found online.
https://dzone.com/articles/exploiting-mqtt-using-lua https://www.hindawi.com/journals/wcmc/2018/8261746/ https://github.com/akamai-threat-research/mqtt-pwn https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b https://book.hacktricks.xyz/pentesting/1883-pentesting-mqtt-mosquitto https://hackmd.io/@QwmL8PAwTx-bYDnry-ONpA/H1nm2tHzb?type=view https://ttm4175.iik.ntnu.no/prep-iot-mqtt.html https://mobilebit.wordpress.com/tag/mqtt/ https://www.hivemq.com/blog/seven-best-mqtt-client-tools/ https://nmap.org/nsedoc/lib/mqtt.html
http://mqtt.p2hp.com/
Original source: Yinji Security
