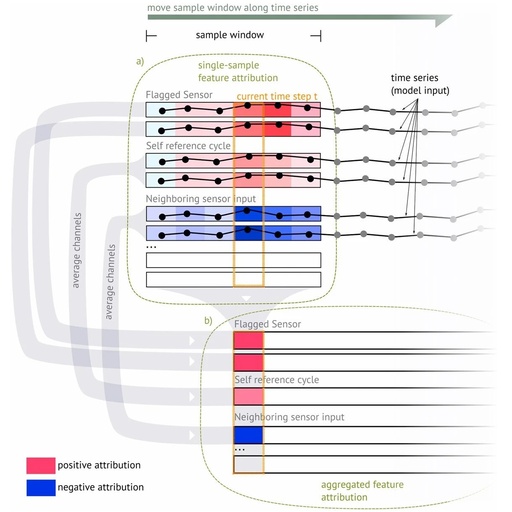
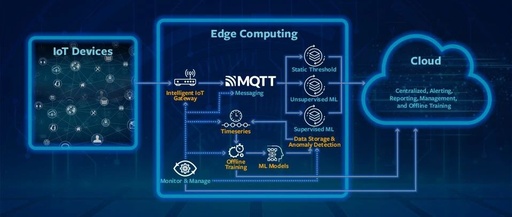
Intelligent Algorithms for PLC: Integrating Machine Learning to Improve Anomaly Detection Accuracy by 50%!
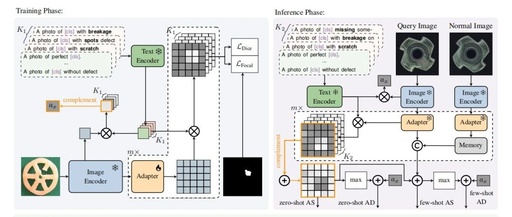
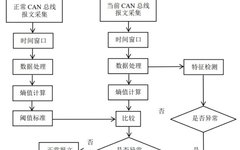
Introduction Hello everyone! Today, I want to share a technological breakthrough that is exciting the field of industrial automation — the perfect combination of PLC and machine learning! Don’t be intimidated by the term “machine learning”; I will explain it in the most relatable way.Trust me, this intelligent algorithm can directly improve the anomaly detection … Read more